 A new piece of malware dubbed Gauss, that experts say is a direct descendant of Flame and also related to Stuxnet and Duqu, has been found on thousands of PCs in the Middle East, mostly in Lebanon. Gauss contains some of the same code as Flame, but is markedly different in a number of respects, specifically in its ability to steal online banking credentials and has an encrypted payload that experts haven’t yet been able to crack. Researchers say that Gauss is almost certainly the work of the same team that wrote the Flame malware, which they speculate is a state-sponsored group.
A new piece of malware dubbed Gauss, that experts say is a direct descendant of Flame and also related to Stuxnet and Duqu, has been found on thousands of PCs in the Middle East, mostly in Lebanon. Gauss contains some of the same code as Flame, but is markedly different in a number of respects, specifically in its ability to steal online banking credentials and has an encrypted payload that experts haven’t yet been able to crack. Researchers say that Gauss is almost certainly the work of the same team that wrote the Flame malware, which they speculate is a state-sponsored group.
Gauss is built on the same platform as Flame and has some of the same attributes, including the ability infect USB sticks connected to compromised machines. Researchers discovered the Gauss infections earlier this year during the investigation into the Flame attacks and estimate that there are about 2,500 infections so far. While looking at the various modules of Flame, researchers found one that didn’t quite match up with the rest of the tool and began looking into it further. What they found was a series of other modules, similar to Flame, some of which were already detected by antimalware products, and others that were not.
Gauss, like Flame, has a modular architecture and contains a number of pieces that perform discrete tasks. The tool is capable of stealing browser cookies and passwords, steal account information for social networks and IM applications, intercept online banking credentials for a handful of Middle Eastern banks as well as PayPal and Citibank and infect USB drives with a data-stealing module. When a clean USB thumb drive is connected to a Gauss-infected PC, the malware will copy itself to the USB drive. Then, when the drive is connected to a clean PC, the Gauss malware will run from the USB drive and collect whatever data it can from the new machine, which then is retrieved from the drive when it’s inserted into a Gauss-infected computer.
This complex routine led researchers to speculate that Gauss may have been designed to infiltrate a specific kind of network.
“It may have been built with an air-gapped network in mind,” said Roel Schouwenberg, a senior malware researcher at Kaspersky Lab, which discovered Gauss and assisted in the investigation into Flame earlier this year.
Air gaps are physical separations of machines on a network, often used in military and other sensitive environments as a way to keep machines housing classified data isolated or to prevent attackers from moving from one machine to another.
Gauss has a lot of similarities to its malicious predecessors, and researchers are confident that it is the handiwork of the same group that wrote Flame at a minimum, and likely Duqu and Stuxnet as well.
“Based on our analysis and the timestamps from the collected malware modules, we believe the Gauss operation started sometime around August-September 2011. This is particularly interesting because around September 2011, the CrySyS Lab in Hungary announced the discovery of Duqu. We do not know if the people behind Duqu switched to Gauss at that time but we are quite sure they are related: Gauss is related to Flame, Flame is related to Stuxnet, Stuxnet is related to Duqu. Hence, Gauss is related to Duqu,” Kaspersky Lab researchers said in a statement on the new malware.
Right now, the malware’s infrastructure is dormant and researchers said that the command-and-control system for the malware went offline last month. There are five C&C servers that were in use during the time that Gauss was active, and they were separate from the much larger C&C system used by Flame.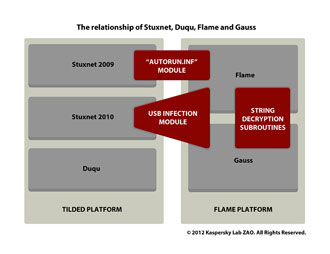
Named after the German mathematician Carl Friedrich Gauss, the new malware, like Flame, Duqu and Stuxnet before it, is somewhat of a mystery at the moment, in a number of respects. Researchers are not sure how the malware spreads or infects machines, although it does have a the same capability to infect USB sticks and exploits the same LNK vulnerability that both Stuxnet and Flame did. That turned out to be just one of the methods that Stuxnet used to compromise a new machine, and there may well be others yet to be discovered in Gauss, as well. It does not look as though Gauss uses any zero day vulnerabilities to infect PCs, but researchers are still unsure how the malware initially infects a new machine.
“It’s important to mention that Gauss infects USB sticks with a data stealing component that takes advantage of the same .LNK (CVE-2010-2568) vulnerability exploited by Stuxnet and Flame. At the same time, the process of infecting USB sticks is more intelligent and efficient. Gauss is capable of ‘disinfecting’ the drive under certain circumstances, and uses the removable media to store collected information in a hidden file. The ability to collect information in a hidden file on USB drives exists in Flame as well. Another interesting component of Gauss is the installation of a custom font called Palida Narrow. The purpose of this font installation is currently unknown,” Kaspersky’s researchers said.
The payload that Gauss delivers also is a mystery. The main payload is encrypted using a key that’s derived from a series of variables taken from the system it’s on and researchers haven’t been able to decrypt the file at this point. Aside from the data-stealing and banker Trojan functionality that’s already known, there could be other hidden functionality in Gauss that haven’t yet come to light.
“Gauss is much more multi-faceted I would say than Stuxnet, which had one particular goal,” Schouwenberg said. “This is more about surveillance than espionage. We don’t necessarily think they’re trying to steal any money, but maye just monitor what’s happening in these accounts.”
One of the other interesting aspects of Gauss’s discovery is its geographic distribution. The huge majority of the infected machines–1,660 of them–are located in Lebanon. Other Middle Eastern countries, including Israel and Palestine, also show infections, but not nearly as many as Lebanon.
Gauss is the latest in what has become an ever-expanding group of attack tools that researchers have classified as cyberweapons, or malware specifically designed by governments or government-sponsored groups to target foreign governments. Stuxnet was the first and most famous of these and was written specifically to compromise the machines running an Iranian nuclear facility. Next came Duqu, a similar tool with a broader target base that researchers said was closely related to Stuxnet and likely produced by the same team. When Flame appeared earlier this year, it signaled a change in the landscape, as researchers found that the malware used a novel spreading technique that involved using a forged Microsoft digital certificate in order to impersonate a Windows Update server.
Now comes Gauss, the latest member of the Stuxnet-Duqu-Flame family tree, armed with an encrypted payload and an odd proclivity to steal online banking credentials. That’s aberrant behavior for a tool allegedly designed by a government, but as the payload, and therefore the malware’s ultimate goal, are unknown at this point, the financial component to Gauss may become clear as time goes on.
“They really went to a lot of trouble to make it hard to break the crypto on Gauss. We’re keeping in mind the possibility of a destructive payload for ICS or SCADA systems,” Schouwenberg said. “Maybe it’s a side effect of the encrypted payload that no one will be able to copy and paste the code like they could with Stuxnet. Maybe they tried to learn some lessons from Stuxnet.”









