Researchers are warning users about a wave of recent attacks targeting U.S. financial institutions that leverage a new banking Trojan dubbed IcedID.
The IcedID Trojan was spotted in September by researchers at IBM’s X-Force Research team. They said the Trojan has several standout techniques and procedures, such as the ability to spread over a network and the ability to monitor a browser’s activity by setting up a local proxy for traffic tunneling.
“At this time, the malware targets banks, payment card providers, mobile services providers, payroll, webmail and e-commerce sites in the U.S.,” researchers wrote in a report released Monday explaining the discovery. Two U.K.-based banks are also targeted by the malware.
Similar to the TrickBot and Dridex Trojans, IcedID both webinjection and redirection attack techniques, researchers said.
“While it is still early to tell how it will fare, its current capabilities, distribution choices and targets point to a group that is no stranger to this domain,” wrote Limor Kessem, Maor Wiesen, Tal Darsan and Tomer Agayev, the X-Force researchers who co-authored the report.
They said IcedID is being distributed by the Emotet Trojan, which is used as a dropper to put IcedID on targeted systems. Emotet is known for its spam campaigns, designed to look like messages from banks, which contain malicious .zip archives.
“IcedID possesses the ability to move to other endpoints, and X-Force researchers also observed it infecting terminal servers,” X-Force reports. “Terminal servers typically provide terminals, such as endpoints, printers and shared network devices, with a common connection point to a local area network or a wide area network, which suggests that IcedID has already been targeting employee email to land on organizational endpoints.”
To maintain persistence on hosts, IcedID creates a RunKey in the registry of the host’s Windows system that allows it to survive reboots. According to X-Force, IcedID requires a reboot to complete its full deployment. The reboot also serves as way to attempt to evade analysis via sandboxes that do not emulate rebooting, researchers said.
Once the malware components are in place the victim has their internet traffic redirected through a local proxy that the adversary controls.
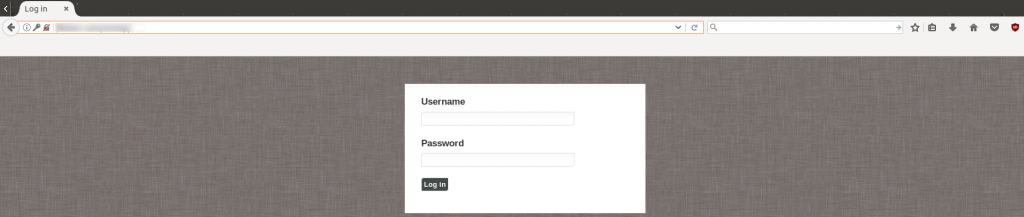
“The malware listens for the target URL from the list (of financial institutions) and, once it encounters a trigger, executes a designated webinjection. The webinjection sends the victim to a fake bank site set up in advance to match the one originally requested,” researchers wrote.
That fake bank site is a “web-based remote panel” prompting a user for a username and password combination.
To thwart detection by the end user, the malware redirects traffic at the same time keeping the bank’s correct URL in the address bar. That live connection also means the bank’s correct SSL certificate always shows.
“From that point on, the attacker controls the session the victim goes through, which typically includes social engineering to trick the victim into divulging transaction authorization elements,” researchers report.
Communication between host and the attacker’s command-and-control server is via SSL.