A mass injection campaign has surfaced over the last two weeks that’s already compromised at least 40,000 web pages worldwide and is tricking victims into downloading rogue, unwanted software to their computer.
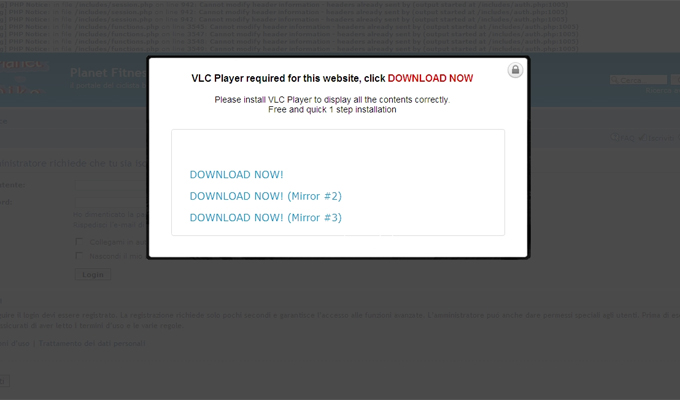
The campaign, dubbed GWload by researchers at Websense, relies on a Cost Per Action scam that convinces users into thinking the page they’ve navigated to has been locked and that they need a special version of VLC Player to open it.
A Cost Per Action scam is a social engineering ploy where the attacker locks content until a certain access is completed. In this case, attackers are using code to defeat browser-based ad-blocker software and then tricking users into downloading something they don’t need.
While VLC Player is a legitimate media player, the version being linked to here is loaded with copious amounts of bloatware. Binaries of more than half a dozen different types of software, including ShoppingChip, SweetIM/SweetPacks, Amonetize Updater, CouponScout, Bprotector and CS Browser Assistant are silently downloaded when the user agrees to download VLC Player and another piece of software, Registry Helper, that piggybacks onto it.
Websense notes the GWload attack has mostly centered on business and economy websites in the United States but ‘Sex,’ ‘Web Hosting’ and ‘Information Technology’ sites and webpages in Taiwan, Italy and Germany also make up a good chunk of the infected sites.
While Websense first noticed the injection campaign pop up the week of Oct. 14, it appears to have really caught on as of late. A graph on the firm’s Security Labs blog today points out its spotted nearly 275,000 injected web pages and that’s just in the last week.
The timing of the campaign is something researchers are suggesting coincides with the recent arrest of “Paunch” the creator of the Blackhole Exploit Kit the week before. Elad Sharf, a senior security researcher at Websense wrote that the change in tactics – from serving exploits to serving social engineering tricks “could suggest that actors adapt to change rapidly to keep their attack going.”
Unlike Blackhole though, this campaign doesn’t lead to malicious payload websites but to actual legitimate websites that have been compromised and used as launching pads for the rogue software installations.
Paunch, the alleged hacker behind the famed Blackhole Exploit Kit was arrested earlier this month in Russia. It’s unclear if there’s actually a connection between the arrest and the increased proliferation of these kind of campaigns. At the time Aleks Gostev, chief security expert for Kaspersky Lab’s Global Research & Analysis Team prophesied Black Hole would either “disappear, be taken over by other developers, or replaced by other exploit kits.”