A new malware family called Jaff has been identified by researchers who say they are currently tracking multiple massive spam campaigns distributing the malware via the Necurs botnet.
“It came out of nowhere with a huge bang,” Cisco Talos researchers said Friday
In the last 24 hours, the firm has observed several large-scale email campaigns each using a PDF attachment with an embedded Microsoft Word document functioning as the initial downloader for the ransomware.
According to Proofpoint researchers Jaff was being distributed as part of a massive spam campaign involving tens of millions of messages. If recipients downloaded and enabled a Word macro associated with the PDF the ransomware was downloaded. Actors behind the malware then demanded a ransom of 1.79 bitcoins (currently $3,300).
“Interestingly we identified several characteristics that we have previously observed being used during Dridex and Locky campaigns,” wrote Cisco Talos researchers Nick Biasini, Edmund Brumaghin and Warren Mercer and Colin Grady, who co-authored a report posted Friday. Similar characteristics include how the ransomware is being distributed and the C2 communication patterns, researchers said.
“However we are confident that this is not simply a new or “retooled” version of Locky ransomware. There is very little similarity between the two codebases, and while it is possible that the same actors who once used Necurs to spread Locky has switched to distributing Jaff, the malware itself is distinct enough in nature that it should be treated and referred to as a different ransomware family altogether,” Cisco’s researchers said.
Proofpoint, who published its research on the malware Thursday, said its similar to Bart ransomware it reported on in June 2016. Bart and Jaff have a payment screen similar to Locky, researchers note. Not similar is the fact Bart encrypts files without first connecting to a command-and-control server, Jaff needs to be downloaded to first.
Spam sent to recipients are typically from either “Joan <joan.1234@[random domain]>” or “John <john.doe123@[random domain]>”, according to Proofpoint. Subject lines vary and are brief such as “Receipt to print.” Message text is sometimes blank or can include short notes such as “Please print 2 copies”.
The infection process begins with a victim opening the single attached PDF file (“nm.pdf”) that comes with the messages.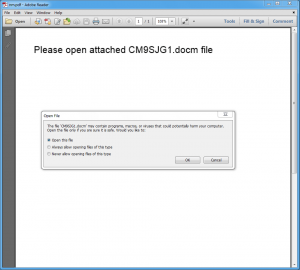
“In each case, the file attachment was a malicious PDF document with an embedded Microsoft Word document. When victims open the PDF, they are greeted with a message in the body of the PDF, which will then attempt to open the embedded Microsoft Word document,” Cisco wrote. “A JavaScript inside the PDF is used to open the embedded Microsoft Word document, however the target is prompted to approve the activity.
At this stage, researchers believe, that by requiring a user to approve the opening of the embedded Word document the attackers are attempting to circumvent sandbox environments used to detect malware.
If the Word document is launched a user is asked to “Enable Editing.” If approved the Word document executes a VBA macro that acts as the ransomware downloader, Brumaghin, Mercer and Grady said. The script calls on several download domains to retrieve the Jaff payload.
“The binary blob downloaded is then XOR’d using a XOR key embedded within the maldoc, we observed multiple XOR keys throughout this campaign. This is found within the Module3 of the VBA Macro, with the XOR key being ‘d4fsO4RqQabyQePeXTaoQfwRCXbIuS9Q’,” researchers at Cisco wrote.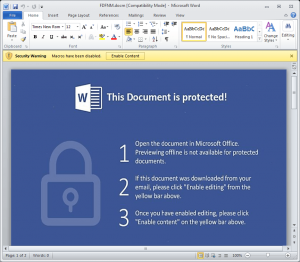
Once the XOR process has been completed the actual ransomware file (PE32) is launched using the Windows Command Processor.
According to researchers, the malware cycles through system folders and encrypts them, adding the file extension .jaff. Once infected, ransom instructions include telling the victim to install the full Tor Browser software package in order to access the ransom payment system. “It is interesting to note that the instructions do not appear to instruct the user to make use of any sort of Tor proxy service such as Tor2Web,” Cisco researchers said.
Both Proofpoint and Cisco Talos note that the payment portal victims are taken to look very similar to those used by Locky and Bart. “How to buy Decryptor Bart?” was changed to “How to buy jaff decryptor?”, according to Proofpoint.










