Intel’s new ninth-generation CPUs come packed with hardware-based protections against two variants of the infamous Meltdown and Spectre speculative execution attacks.
The ninth-generation desktop Core processors are dubbed Coffee Lake, and became available for preorder on Tuesday. they’re built to address the Meltdown V3 and L1 Terminal Fault variants.
“The new desktop processors include protections for the security vulnerabilities commonly referred to as ‘Spectre,’ ‘Meltdown’ and ‘L1TF,'” an Intel spokesperson told Threatpost. “These protections include a combination of the hardware design changes we announced earlier this year, as well as software and microcode updates.”
‘Virtual Fences’
Spectre and Meltdown stem from a trick that computing processors use – speculative execution of memory – which helps them read memory before the addresses of all prior memory writes are known, ultimately increasing performance and speed.
The most common form of speculative execution allows a processor to predict the control flow 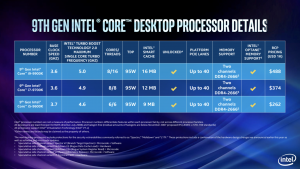 instead of waiting for all branch instructions to resolve, to determine which operations are needed to execute. But, while this method helps processors stay as optimal as possible, it also enables an attacker with local user access using a side-channel analysis to gain unauthorized disclosure of information.
instead of waiting for all branch instructions to resolve, to determine which operations are needed to execute. But, while this method helps processors stay as optimal as possible, it also enables an attacker with local user access using a side-channel analysis to gain unauthorized disclosure of information.
Earlier this year, Intel announced that it would implement hardware-based safeguards for its new chips to protect against this class of attacks. This set of CPU design features work with the operating system to install “virtual fences” to prevent side-channel inference, thus protecting the system from speculative execution attacks.
The new safeguards were also built into Intel’s next-generation Xeon Scalable processors, code-named Cascade Lake, as well as Intel’s eighth-gen Core processors, which are expected to ship before the end of the year.
Two variants are covered in these hardware-based protections:
One of those variants includes L1TF, a speculative-execution side-channel cache-timing vulnerability discovered in August. Three varieties of L1TF have been identified: CVE-2018-3615, CVE-2018-3620 and CVE-2018-3646.
The other addressed variant is Meltdown GPZ V3, or CVE-2017-5754, which stems from rogue data cache load and was discovered in January.
“In the new 8th Gen Intel Core U-series processor (WhiskeyLake) and 9th Gen Intel Core Desktop Processors (CoffeeLake), there are now hardware changes to protect against Meltdown (GPZ V3) and L1TF,” Intel told Threatpost.
In addition, Intel has released microcode updates for Intel microprocessor products launched in the last nine years that require protection against the side-channel vulnerabilities. That includes the company’s newer Skylake, Kaby Lake and Cannon Lake platforms, as well as its Broadwell and Haswell platforms, which were patched in February.
Mitigations for Other Variants
These hardware-based protections are specific to certain variants, and – as reported by Threatpost earlier this year – will not impact the newly-discovered Variant 4 or other potential speculative execution side channel-related flaws in the future.
In ninth-generation CPUs, Spectre V2 (the branch target injection variant of Spectre) is addressed by software plus microcode. However, “over time, products will also ship with the hardware changes to protect against V2 – for instance, Cascade Lake will have this,” the Intel spokesperson said.
Spectre V1 will continue to be addressed via software mitigations. Meanwhile, the Meltdown V3a – rogue system register read – will continue to be protected via microcode updates.
Finally, Variant 4 (or CVE-2018-3639) which could give attackers unauthorized read access to memory via speculative store bypass, will be covered by microcode and software patches. Variant 4 uses a different process to extract information and is more of a cache exploit and that can be used in browser-based attacks.
While hardware-based protections are now available, security experts stress that taking a proactive approach is still key when it comes to flaws like Spectre and Meltdown.
“To combat this and similar security risks, a proactive approach to threat detection is essential,” said Matthew Chiodi, vice president of cloud security at RedLock. “The higher level of vigilance drives up the economics of an attack and discourages hackers from exploiting emerging vulnerabilities. A real-time vulnerability management strategy enables organizations to identify systems running older versions of software. This is a particularly difficult issue to address in on-premise environments as they typically span large and often segmented IP ranges which means IP-based vulnerability scans can take weeks to complete.”











