The bulk of “unknown” malware is being delivered to systems via Web-based attacks, proxies and FTP sessions, according to a study released by Palo Alto Networks this week.
The study dubbed “The Modern Malware Review,” found more than 26,000 malware samples, and focuses on what the firm calls unknown and undetected malware–samples that got past other antimalware systems.
The report emphasizes the shift attackers have made in recent years from email-based exploits to Web-based exploits and in turn. Since Web pages load instantly and attacks can be tweaked on the fly while email-based attacks are sent en masse and generally target a wider variety of people, there’s an inherent difference in how both are recognized.
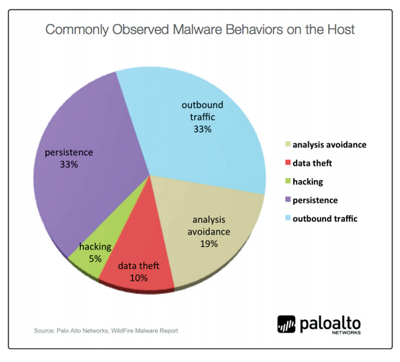 Ninety-four percent of the undetected malware came from Web-browsing or Web proxies.
Ninety-four percent of the undetected malware came from Web-browsing or Web proxies.
The report calls FTP-based exploits “one of the most effective and evasive sources of malware;” 94 percent of FTP samples were only seen once, while 95 percent were never noticed by antivirus and 97 percent used non-standard ports to infect systems.
“FTP had the ignominious distinction of being both a common source of unknown malware as well as one of the sources that rarely received coverage,” said the report.
Palo Alto gives a handful of recommendations for mitigating Web and FTP-based malware including investigating unknown traffic, restricting rights to dynamic DNS domains, real-time detection and blocking, and more fully deploying antimalware technology.
The research is the result of monitoring three months of data compiled from the company’s WildFire feature, a malware blocking component of Palo Alto’s firewall service. More than 1,000 networks were monitored and while just over 68,000 malware samples were found, 26,363 were what the company referred to as undetected.









