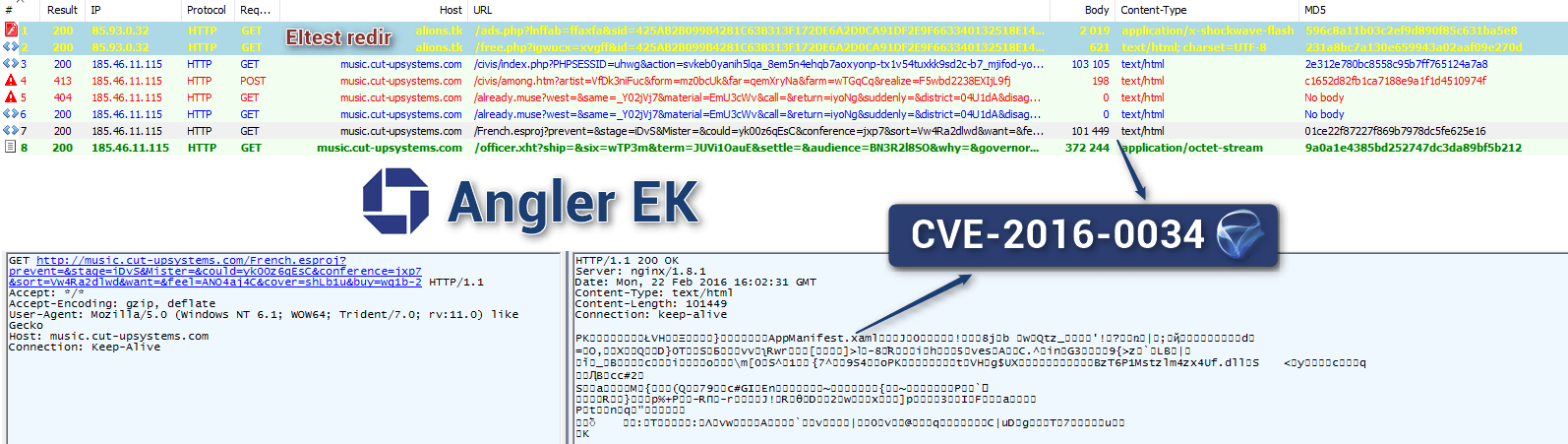
Exploits for a vulnerability in Microsoft Silverlight have found their way into the dangerous Angler Exploit Kit a little more than a month after it was patched.
French security researcher Kafeine said he was able to get independent confirmation from researchers at Kaspersky Lab that the exploit targeted CVE-2016-0034, which was fixed by Microsoft in bulletin MS16-006 that was part of January’s Patch Tuesday release.
The quick turnaround was anticipated not only by Kafeine, but also by Kaspersky researchers who disclosed the bug to Microsoft and shortly after the bug was patched, said they had discovered it being used in limited targeted attacks, and warned it would not be long before attacks went mainstream.
“It’s a big deal; Silverlight vulnerabilities don’t’ come around that often,” said Kaspersky Lab researcher Brian Bartholomew. “Exploitation of the zero day itself is fairly technical, but once a proof-of-concept falls into the hands of someone who knows what they’re doing and reverse engineers the patch, it’s not that difficult to produce a weaponized version of it.”
Kafeine shared a timeline related to the Angler integration of the Silverlight attacks, starting last Thursday with the inclusion of a code snippet that resulted in a new call if Silverlight was indeed installed on the compromised computer. By yesterday, the calls in question were dropping TeslaCrypt ransomware in attacks.
Silverlight vulnerabilities and exploits are not as prevalent as similar attacks involving Adobe Flash Player, but are still coveted by attackers.
“There is an interest in all that is reasonably widely used, exploitable and allows [remote code execution] after driveby,” Kafeine said.
According to Microsoft, the vulnerability opens the door to remote code execution and affects Microsoft Silverlight 5 and Microsoft Silverlight 5 Developer Runtime; later builds after 5.1.41212.0 are not affected.
Exploit kits—Angler being among the most actively updated and widely used—infect websites in a variety of manners. Users landing on these sites running vulnerable web browsers, usually Internet Explorer, are infected and served iframes that redirect to attacker-controlled sites where additional malware—in this case, ransomware—is dropped.
The Silverligtht vulnerability serves to give an attacker an initial foothold on a compromised machine. From there, additional payloads are served to the infected computer and can lead to the loss of sensitive data or further network infiltration.
This particular bug has an interesting back story that Kaspersky Lab’s Global Research and Analysis Team shared in January.
Kaspersky’s Costin Raiu and Anton Ivanov found the bug after investigating data exposed in this summer’s Hacking Team breach. Prompted by an email from a Russian hacker named Vitaliy Toropov to Hacking Team that was published in July by Ars Technica, the researchers decided to pursue Toropov’s claims that he had a Silverlight zero day for sale that was at least two years old in 2013 and which he said could survive for a few more years without detection.
The researchers found an older Silverlight exploit submitted to Packet Storm by Toropov, wrote a YARA rule for it that was deployed to Kaspersky customers. That rule was not triggered until November by an exploit compiled shortly after the Hacking Team breach went public.
Kaspersky researchers were unsure whether this exploit was the same one uncovered in the Hacking Team data or a new one written after the leak. Kaspersky’s Bartholomew said there are commonalities in both samples that are unique to Toropov.
“Not many people write Silverlight zero days, so the field is narrowed significantly,” Bartholomew said. “On top of that, there are some error strings used in his old exploit from 2013 that we latched on to and thought were unique. These were the basis of our rule.
“This exploit contains the same error strings a .NET application ID that is the same as the old one. Every time you build new app in .NET, you get a new ID. This has the old one. All of this adds to the pile of indicators that point to him.”