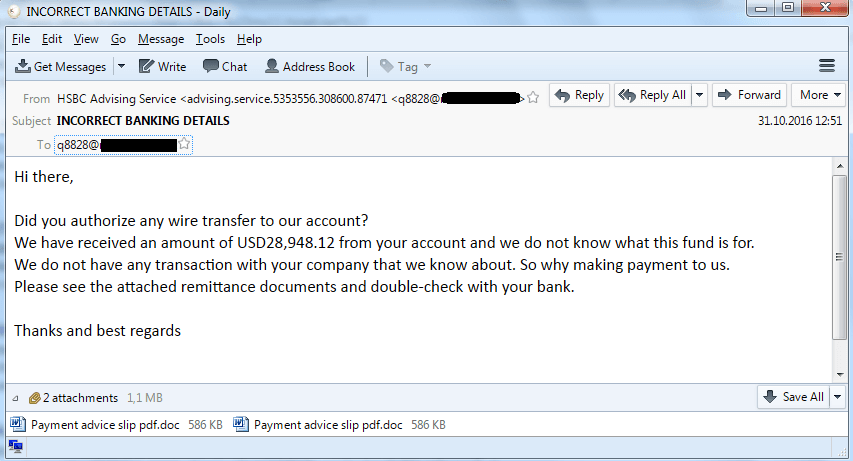
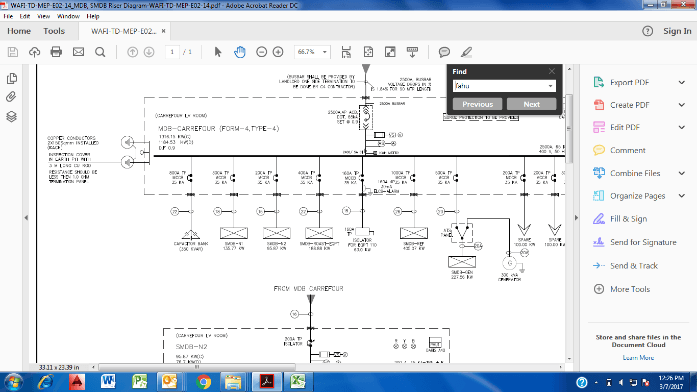
Nigerian cybercriminals targeting industrial firms have stolen a slew of sensitive technical drawings, network diagrams, cost estimates, and project plans already this year. The data, exfiltrated by a cocktail of different spyware programs, wasn’t stolen from just executives, but also operators, engineers, designers and architects.
The thefts stem from a series of Business Email Compromise (BEC) attacks. In total, researchers with Kaspersky Lab said this week they’ve seen over 500 companies – mostly in the industrial and transportation sector – from 50 countries hit by strategic phishing messages over the past several months.
A report by the company’s Industrial Control Systems Cyber Emergency Response Team broke down the phishing attacks on Thursday.
A map, published alongside the report, suggests corporations in the Middle East (the United Arab Emirates in particular), Russia, Germany, and India have been the hardest hit.
Like most BEC attacks, the attacks begin with phony but authentic looking emails, complete with attachments named “Energy & Industrial Solutions W.L.L_pdf,” and so on.
All the emails came with .RTF files armed with either an old Microsoft Word exploit – CVE-2015-1641, or macros and OLE objects that trigger the download of additional malicious files. Data sniffing malware, packed both with VB and .NET packers, from eight different families – including ZeuS, Pony, LokiBot, and a variety of RATs – were also used in the attacks, Kaspersky Lab said Thursday.
While it’s clear what’s been taken, it’s unclear exactly who’s behind the campaign. Researchers hint it’s either one group using different malware families or different groups working in tandem, using the same command and control setup to distribute their wares.
In some instances the attackers were able to gain access to websites belonging to the companies they targeted in order to host malware on their servers and use them as their C+C. In other cases attackers managed to secure access to email accounts of company employees and send malicious emails and attachments to executives at other companies.
When they couldn’t infiltrate their victims’ sites or emails to spread malware, the attackers set up C+C domains to mimic the actual name of the company targeted, or blended of the site’s legitimate name and its top-level domain.
The attackers didn’t do much to cover their tracks. The bulk of the domains, according to researchers, were registered to Nigerian residents.
Once a corporate machine has been compromised, the sky’s the limit for the attackers. The report claims they can carry out man-in-the-middle attacks, take screenshots of correspondence, redirect messages from the victim’s mailbox and track internal transactions by the company.
Researchers with the firm reported seeing screenshots of diagrams, mockups of electrical and information networks, and Autodesk AutoCAD projects on some command and control servers. The data is technical in nature and could likely be used to carry out future attacks, Kaspersky Lab suggests.
“There is no need for the attackers to collect this kind of data in order to perpetrate their phishing scams. So what do they do with this information? Is the collection accidental, or intentional – perhaps commissioned by a third party?” Maria Garnaeva, senior security researcher, Critical Infrastructure Threat Analysis, Kaspersky Lab said.
“So far, we have not seen any of the information stolen by Nigerian cybercriminals on the black market. However, it is clear that, for the companies being attacked, in addition to the direct financial loss, a Nigerian phishing attack poses other, possibly more serious, threats.”
While these types of attacks aren’t necessarily new, Kaspersky Lab researchers said they observed a significant uptick in attacks focusing on industrial corporations in October 2016. The attacks have been ongoing and are “unlikely to end any time soon,” the report asserts.
The attacks supplement statistics recently released by the U.S. government. The FBI said in May that BEC schemes had grown a whopping 2,370 percent in the last two years.
The report, released via the FBI’s Internet Crime Complaint Center (IC3), said that since late 2013 businesses have lost more than $5.3 billion. Of that, $3 billion came at the hands of Nigerian phishers, the FBI said. Most of those funds were ultimately funneled to banks in China and Hong Kong via wire transfers and phony tax form scams.
Researchers with Dell SecureWorks, who in the past have displayed an aptitude for analyzing these kind of scams, described at the RSA Conference earlier this year how they managed to derail one. The researchers, Joe Stewart and James Bettke, posed as an executive, gained the trust of one fraudster, and successfully had several mule accounts tied to the attacker frozen, mitigating potential extensive future loss.
Stewart said at the time it’d be helpful if there was some sort of centralized repository for reporting these kinds of attacks.
“There’s no shortage of people who recognize these things and string them along. The problem is that there’s no central place to report these accounts and get them shut down,” Stewart said. “Some of these guys have accounts in every country. Try to find the right contact at a particular bank in a particular country and tell them that they have accounts used by fraudsters. There’s no easy way to do it. There needs to be someone leading the effort and the charge.”