A new version of the evolving ransomware threat GandCrab has been identified by researchers – but evidence of the new malware self-propagating via the Windows transport protocol Server Message Block (SMB) exploit still remains to be seen.
Security researchers at Fortinet said that they have spotted version 4.1 of GandCrab in the wild. The ransomware was first spotted six months ago, but has already grown and continuously evolved to become a formidable and threatening ransomware sample in 2018.
Recent reports, suggesting the ransomware exploited a vulnerability in the SMB transport protocol used by Windows machines including on XP and Windows Server 2003, raised concern.
The SMB exploit (EternalBlue) was used in the destructive WannaCry ransomware attacks in 2017. That means if the reports were true, GandCrab developers have started pushing their malware to vulnerable Windows XP and 2003 PCs, wrote security researcher Kevin Beaumont in a post about the ransomware earlier this month.
“Impacting legacy XP and 2003 systems suggests some older environments may end up at risk where there is poor security practice — e.g. no working antivirus software,” he wrote. And while a patch (MS17-010) for the SMB exploit (which includes Windows XP and 2003) was issued by Microsoft after WannaCry, many of these legacy systems have not been updated.
However, while the new version contains a new network communication method, researchers said they could not find evidence that the malware can self-propagate via the Windows SMB exploit.
“Since we had not seen any technical report for the claim, we decided to investigate and confirm this rumour since this functionality was not observed during our previous analysis. However, this was to no avail,” the researchers said in a recent post about the newest GandCrab sample.
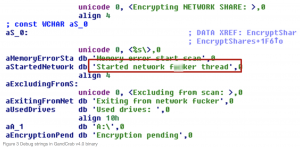 Rumors had suggested that a module dubbed “network f**ker,” found in a debug string of the malware’s binary, is supposedly responsible for performing the SMB exploit.
Rumors had suggested that a module dubbed “network f**ker,” found in a debug string of the malware’s binary, is supposedly responsible for performing the SMB exploit.
Researchers said they found this module string in version 4.0 of the malware (not in samples of the most recent 4.1 version, however), but could not find any actual function that resembles the reported exploit capability.
“Since this string is not connected to any actual exploit spreading function that we could uncover, it seems much more likely that it is simply referring to the encryption of network shares, and not for any sort of exploit propagation,” they said.
New Communication Tactic
Despite no evidence of leveraging the SMB exploit, the newest sample of the ransomware does come with other malicious tricks up its sleeve, including a new network communication tactic: “This new version of the GandCrab malware contains an unusually long hard-coded list of compromised websites that it connects to,” Fortinet researcher said. “In one binary, the number of these websites can go up to almost a thousand unique hosts.”
GandCrab 4.1 connects to one of the URLs in the list, and sends data scooped up from the victims – including the IP address, computer name, network name, username, and list of anti-malware tools present on the system.
Interestingly, researchers said they found no definitive evidence that the hard-coded websites included in the malware had actually ever been compromised to act as servers or download sites for GandCrab.
“Even more curious, the fact is that sending victim information to all live hosts in the list is illogical in a practical sense, given that a single successful send would have been enough for its purposes,” researchers said. “With these points in mind, we have started to think that this function is either experimental, or simply there to divert analysis and that the URLs included in the list are just victims of a bad humour.”
Researchers also found that the newest version of GandCrab is programmed to kill several processes “to ensure the full encryption of targeted files.” These processes include msftesql.exe, sqlagent.exe, sqlbrowser.exe, sqlwriter.exe, and oracle.exe.
“Killing off these processes allows for the encryption routine to successfully complete its goal without any undesirable interruptions,” researchers said. “Additionally, these targeted file types often contain data that is valuable to the victim, and therefore… increases the likelihood that the victim will consider making a payment to get their files back.”
GandCrab – A Long Past
Back in March, Check Point researchers said that the group behind GandCrab has infected over 50,000 victims mostly in the U.S., U.K. and Scandinavia. And in only two months after the ransomware group was first in business, criminals earned up to $600,000.
The malware is particularly tricky as it has been continually been tweaked to deal with potential roadblocks– such as Romanian Police and Europol seizing command-and-control servers tied to the ransomware’s campaigns in March, or a free decryptor released in March.
The ransomware was most recently spotted by Cisco Talos researchers as part of several large-scale spam campaigns in May.
Despite a lack of evidence for the “SMB exploit,” researchers at Fortnet warned that GandCrab will continue to evolve and may adopt the method in the future.
“However, with GandCrab’s rapid development over the past week, and the public speculation of this exploit propagation functionality, we would not be a surprise if the threat actors decided to add it in a future update,” they said.










