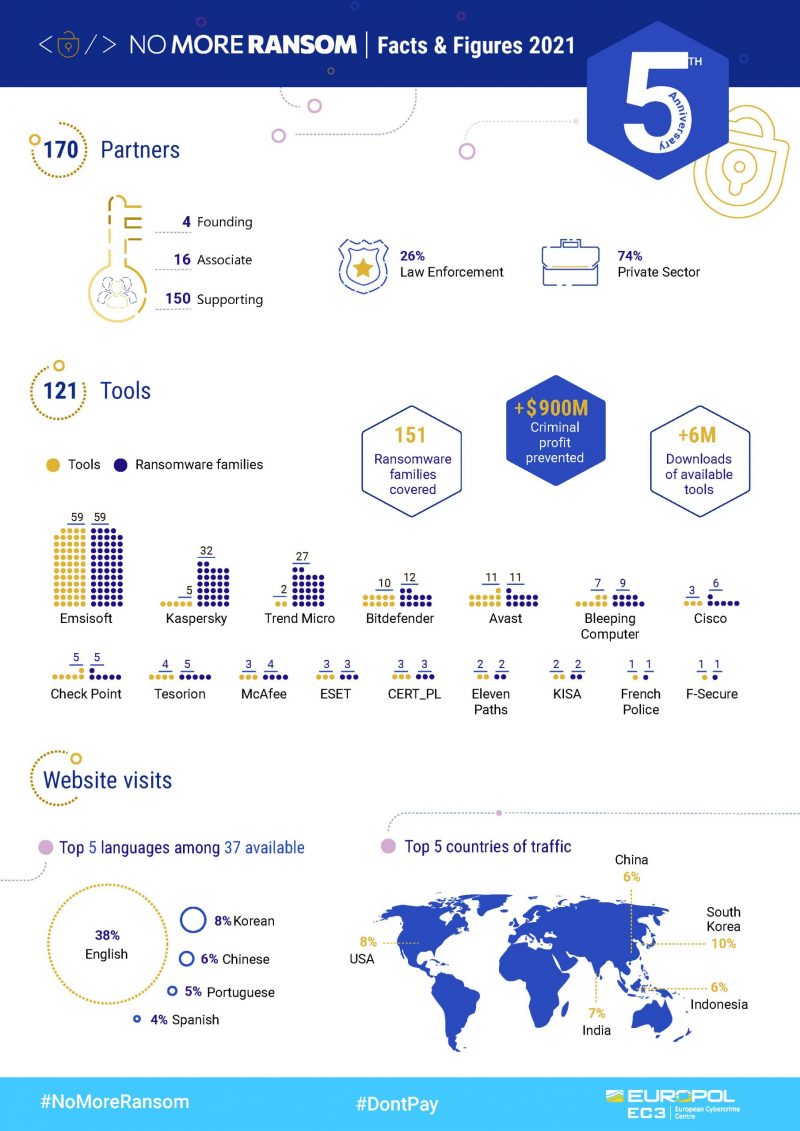
To date, the No More Ransom repository of ransomware decryptors has helped more than 6 million victims recover their files, keeping nearly a billion euros out of the hands of cybercriminals, according to a Monday release.
Launched five years ago, No More Ransom is maintained via cooperation between the European Cybercrime Centre and several cybersecurity and other types of companies, including Kaspersky, McAfee, Barracuda and AWS. Its purpose is to keep victims from handing over the cash that helps fuel more ransomware attacks, according to Europol.
“The general advice is not to pay the ransom,” No More Ransom advises. “By sending your money to cybercriminals you’ll only confirm that ransomware works, and there’s no guarantee you’ll get the decryption key you need in return.”
Instead, the group directs victims to their Crypto Sheriff tool. There, victims can enter either the URL, onion or Bitcoin address given by the attacker to pay the ransom. The tool searches the No More Ransom database, where the offerings have grown from an initial four decryptors back in 2016 to the current roster of 121 tools to decrypt 152 ransomware families. It’s also free and available in 37 languages, according to the group.
If no decryptor is available for a given ransomware infection, keep checking back: No More Ransom regularly adds new unlock tools.
Don’t Pay the Ransom: Here’s Why
Ransomware victims are increasingly reluctant to pay ransom demands. A Threatpost poll from June found 80 percent of respondents who were hit by a ransomware attack flat out refused to pay for a decryptor that might, or might not, show up.
Worse yet, a June report from Cybereason indicates victims who are quick to pay identify themselves as easy prey. Cybereason reported that 80 percent of organizations that paid a ransom were hit with a follow-up attack. Half of those were attacked a second time by the same group, but a full third attracted additional threat actors smelling an easy payday.
No More Ransom is an answer to the rise of cyber insurance companies, which seem to be injecting massive amounts of cash into the ransomware ecosystem. During the first half of 2020, ransomware attacks made up 41 percent of the total cyber insurance claims, according to a June Cyber Claims Insurance report from Coalition.
Besides funding a criminal enterprise, payment of ransomware to sanctioned nation-state actors could put an organization in violation of the U.S. Department of Treasury, which added several ransomware groups to its sanctions list in October 2020.
Regular backups remain the best way to protect data from a ransomware attack, the Europol said. They further recommend users be mindful of the links they click on and update their security software. But most importantly, the cybercrime cops appeal to organizations to avoid handing over their money.
“If you become a victim, do not pay!” the Eurpol said. “Report the crime and check No More Ransom for decryption tools.”
![]() Worried about where the next attack is coming from? We’ve got your back. REGISTER NOW for our upcoming live webinar, How to Think Like a Threat Actor, in partnership with Uptycs on Aug. 17 at 11 AM EST and find out precisely where attackers are targeting you and how to get there first. Join host Becky Bracken and Uptycs researchers Amit Malik and Ashwin Vamshi on Aug. 17 at 11AM EST for this LIVE discussion.
Worried about where the next attack is coming from? We’ve got your back. REGISTER NOW for our upcoming live webinar, How to Think Like a Threat Actor, in partnership with Uptycs on Aug. 17 at 11 AM EST and find out precisely where attackers are targeting you and how to get there first. Join host Becky Bracken and Uptycs researchers Amit Malik and Ashwin Vamshi on Aug. 17 at 11AM EST for this LIVE discussion.