Graphics chipmaker Nvidia has issued three patches for high-severity vulnerabilities in its GPU display driver, which could lead to information disclosure, escalation of privileges and denial of service (DoS) in impacted Windows gaming devices.
Nvidia’s graphics driver for Windows is used in devices targeted to enthusiast gamers; it’s the software component that enables the device’s operating system and programs to use its high-level graphics hardware.
The most severe of the flaws, CVE‑2019‑5675, could be exploited to launch DoS attacks that could cripple the system, as well as give attackers escalation of privileges and disclose system information, according to a Thursday advisory released by Nvidia.
The bug exists in the kernel mode layer handler component of the driver. Kernel mode is generally reserved for the lowest-level, most trusted functions of the operating system; in this case, the layer handler for the DxgkDdiEscape interface within the kernel mode does not properly synchronize shared data, which could lead to glitches in the behavior of the data – resulting in malicious attacks, according to Nvidia’s security release, issued Thursday.
“[The driver] contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape, where the product does not properly synchronize shared data, such as static variables across threads, which can lead to undefined behavior and unpredictable data changes, which may lead to denial of service, escalation of privileges or information disclosure.”
The flaw has a CVSS score of 7.7, making it a high-severity vulnerability.
Another flaw, CVE‑2019‑5676, exists in the driver’s installer software and is also rated high-severity. The software incorrectly loads Windows system dynamic link libraries (DLLs) without validating their path or signature.
This could enable a DLL preloading attack, where an attacker gains control of a directory on the DLL search path, and places a malicious copy of the DLL in that directory – leading to privilege-escalation of through code execution.
Multiple security researchers were credited with reporting this flaw, including Kushal Arvind Shah with Fortinet’s FortiGuard Labs; Łukasz ‘zaeek’; Yasin Soliman; Marius Mihai; and Stefan Kanthak.
The final vulnerability, CVE‑2019‑5677, could lead to DoS. This flaw also exists in the driver’s kernel mode layer (nvlddmkm.sys) handler, for the DeviceIoControl interface. The software in this component “reads from a buffer using buffer-access mechanisms such as indexes or pointers that reference memory locations after the targeted buffer, which may lead to denial of service,” according to the advisory.
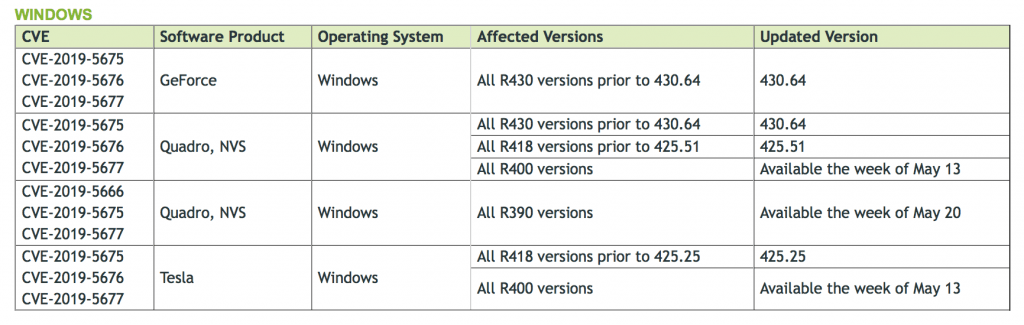
Nvidia is encouraging users to update its driver on various software products running on Windows. Patches are currently available for various versions of GeForce and Tesla (see a full breakdown of patches below).
Device manufacturers that use Nvidia drivers, such as Lenovo for its IdeaPad, ThinkPad, ThinkStation and other devices, have also dropped their own advisories on when patches will be available.
The chipmaker has patched an array of flaws so far in 2019: In April, Nvidia released fixes for eight high-severity vulnerabilities in its “Linux for Tegra” driver packages; the worst of which could allow information disclosure, denial of service and code execution on impacted systems. And in March, Nvidia patched a high-severity vulnerability in its GeForce Experience software, which could lead to code-execution or DoS of products if exploited.