MOSCOW–The problem of attackers infecting legitimate Web sites with malware that then silently exploits vulnerabilities in users’ browsers reached unprecedented levels in 2009, with 1 in every 150 legitimate sites serving up malware, experts say.
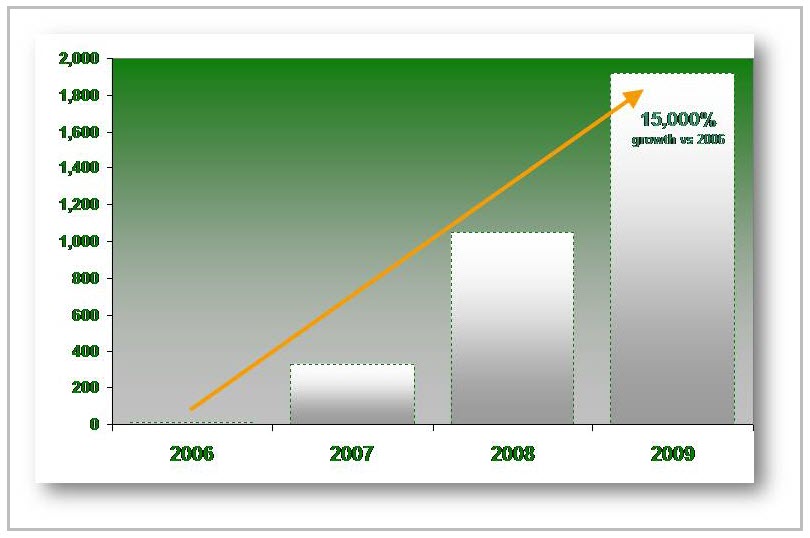
Analysts at Kaspersky Lab have been monitoring a pool of about 300,000 legitimate Web sites for the last several years, looking to see how many become infected with malware and how long the infections last. In 2006 the rate was about one infected site in every 20,000 otherwise clean sites. By 2009 that number had skyrocketed to one in every 150 sites, a massive increase driven by the continued success of mass SQL injections campaigns by malware such as Gumblar, Asprox and others.
Many of the infections also are using stolen FTP credentials to perpetuate a vicious cycle of user compromise, credential theft, site infection and malware storage. Once a user’s machine is infected with a particular type of malware, the program searches the user’s PC for FTP user names and passwords, which it then sends off to a remote server. The attacker behind these campaigns then use the FTP credentials to gain access to remote FTP servers, where they will store attack tools and exploit kits that later can be used for other infections.
It’s a frighteningly efficient and simple infection method that shows little evidence of slowing down. As long as it’s still effective, there’s no reason for the attackers to move on to other more complicated tactics.
“It still works very well. They have no trouble finding new sites to infect,” said Stefan Tanase, senior regional researcher on Kaspersky’s Global Research and Analysis Team, in a recent talk here during the company’s press tour.
One of the major reasons this attack vector is so wide open is that many users have no idea that it even exists. Internet users who have been trained over the years to be wary of emails that look like they come from their bank or credit card company and to avoid the sketchier corners of the Web have no clue that legitimate media and e-commerce sites are owned and actively attacking unsuspecting visitors.
That obviously works to the advantage of the attackers, who count on the visitors trusting these sites and not worrying about any slightly odd behavior they might see on them.









