Researchers today identified a series of ongoing targeted attacks primarily designed to steal sensitive corporate financial data from industrial and engineering organizations in the Middle East.
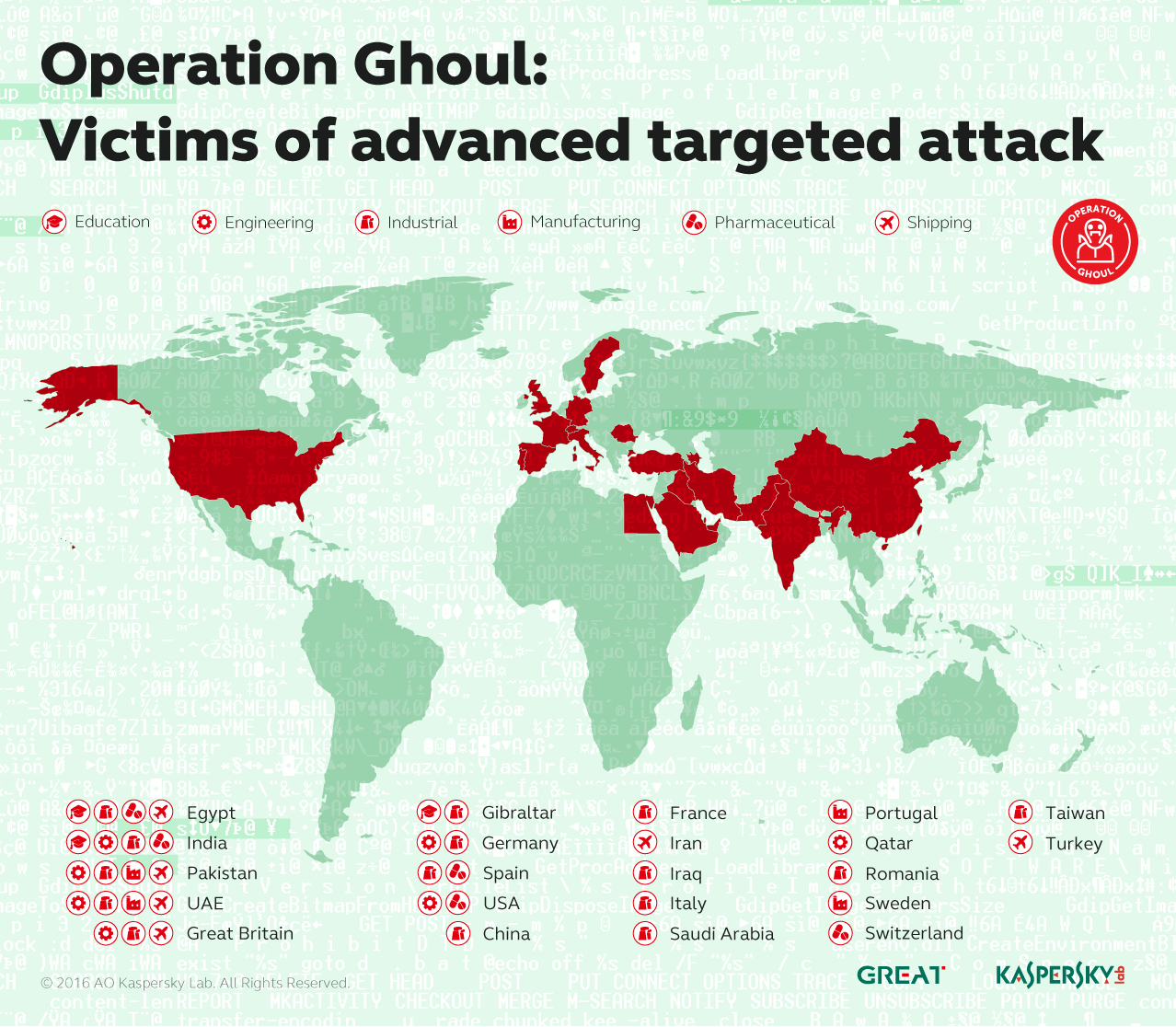
The group behind the campaign, nicknamed Operation Ghoul by researchers at Kaspersky Lab’s Global Research and Analysis Team, has carried out attacks against 130 organizations in 30 countries to date according to a report published Wednesday.
While the attacks have been mostly focused on countries in the Middle East – 70 percent of attacks hit companies in the United Arab Emirates – researchers have also observed attacks carried out in India, the United Kingdom, and Germany. Ghoul has hit Spain the hardest; 25 organizations in the country have been targeted by the campaign.
Researchers claim that while attack lacks sophistication – the campaign utilized a single command and control server – it shouldn’t make it any less dangerous.
“Unlike state-sponsored actors, which choose targets carefully, this group and similar groups might attack any company. Even though they use rather simple malicious tools, they are very effective in their attacks,” Mohammad Amin Hasbini, a security expert at Kaspersky Lab said, “Thus companies that are not prepared to spot the attacks, will sadly suffer.”
The attacks are built around spear phishing emails with compressed .7z attachments that if opened, trigger data stealing malware. The malware executable begins to suck up passwords, keystrokes, and screenshots to forward it along to attackers. In some cases victims are tricked into following phishing links.
The malware, based on HawkEye, a commercial spying tool, also grabs FTP server credentials, account data from browsers, messaging clients, and email clients, along with clipboard data. From there the attackers use a combination of HTTP GET posts and email messages from already compromised organizations to exfiltrate the data.
The emails, sent to executives and higher ups at organizations, appear to come from a bank in the United Arab Emirates, the Emirates NBD and feature phony subject lines such as “Your payment copy advice from Emirates NBD Bank/subsidiary.”
The most recent swell of attacks started on June 8 and June 27 but researchers claim artifacts associated with the malware files and attack sites suggest the origin of Ghoul could be traced back to March 2015.
The campaign is the latest in a long line of targeted attacks against Middle Eastern industrial sector.
Energy organizations in the Middle East were targeted a few years ago by attackers peddling the njRAT espionage malware. Similar to Operation Ghoul, attackers dropped the remote access Trojan on companies in order to glean data; credentials stored in browsers, steal files, view a user’s desktop and access their computer.
In 2013 attackers were spotted using the Citadel banking Trojan on petrochemical companies in the Middle East. In those attacks, hackers targeted webmail at companies. Attackers could elbow their way into employee or contractor emails and send messages and facilitate phishing campaigns.