Oracle has released a massive Critical Patch Update (CPU) for July, addressing 334 security vulnerabilities covering a vast swathe of its enterprise portfolio.
Of the 334 vulnerabilities covered this month, 61 are rated critical, with a CVSS rating between nine and 10. Oracle said in its advisory Tuesday that it has observed several exploits operating in the wild, across the spectrum of security holes, so applying the update should be at the top of the to-do list for administrators.
The update marks an all-time high for CPU fixes for the vendor, overtaking its previous record of 308 in July 2017. Not that large numbers of fixes are uncommon: In its previous CPU in April, it fixed 251 flaws; and before that, in January, it addressed 233.
Oracle’s business-critical applications are heavily represented, with the majority of the patches in the CPU issued for the widely deployed PeopleSoft enterprise resource planning platform, the E-Business Suite, the MySQL database, Siebel CRM, the Fusion middleware, JD Edwards products and more. Taken together, these systems house the most sensitive information for any company, including financial information, HR data, vertical-specific information like student grades and loans or healthcare PHI, plus strategic operational data on business processes and intellectual property.
Java patches were also issued – but only eight of them, which is a 75 percent drop from last year’s July CPU.
Oracle’s financial services applications received the most patches (56), followed by Fusion middleware (44), and then retail applications and the MySQL database (31 respectively). About 65 percent of the flaws can be exploited remotely without entering credentials, according to an analysis today from ERPScan. On the financial services front, 21 of the 56 bugs could allow attackers to gain access to systems remotely, without having to enter user credentials; in Fusion, 38 of the 44 would allow this.
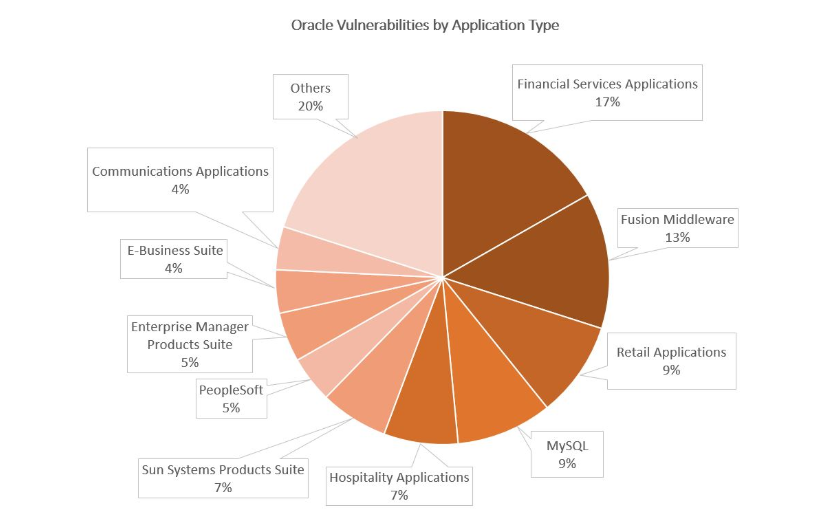
Source: ERPScan
Bugs of Note
In terms of notable vulnerabilities, one of the most serious in Fusion allows a remote user to access and modify data via a flaw in the Oracle Business Process Management Suite Process Analysis & Discovery component (CVE-2018-3100); another allows bad actors to gain elevated privileges using an issue with the Oracle Fusion Middleware MapViewer Map Builder component (CVE-2018-2943). Other issues in Fusion can cause denial-of-service conditions.
PeopleSoft meanwhile received 15 fixes, with two carrying a high 9.8 CVSS score. This is especially of interest given that the application suite supports core enterprise functions such as HR, finance, supply chain management, services automation and more.
“As it manages a wide range of business processes and stores key data, a successful attack against PeopleSoft allows an attacker to steal or manipulate different business critical information, depending on modules installed in an organization,” ERPScan noted in its analysis.
There are also multiple flaws in the Oracle E-Business Suite that would allow a remote user to access and modify data on the target system: There are 14 patches in all, with the highest CVSS score clocking in at 8.2. One of the issues would also allow a local user to exploit a flaw in the Oracle Order Management Product Diagnostic Tools component to gain elevated privileges (CVE-2018-2954).
On the Java front, the CPU contains eight new security fixes for Oracle Java SE. All of the vulnerabilities are remotely exploitable without authentication; they exist in Java SE versions 6u191, 7u181, 8u172, and 10.0.1, with the highest CVSS score coming in at 9.
“On the surface, the downward trend of Java SE patches would appear to be positive,” said James Lee, executive vice president and global CMO at Waratek, in a posting. “However, it may actually be more of a reflection of the adoption rates of Java SE 9 and 10 as the Java community continues to rely on older versions of Java. With low adoption rates, there are simply fewer users in a position to report bugs in the newest versions of Java.”
Other serious flaws of note include a privilege escalation bug in Oracle middleware (CVSS 9.8) and a cross-scripting vulnerability in JD Edwards TETaskProperties maflet (CVSS 9.1) that can be used to hijack administrators’ session data. These were among 17 critical vulnerabilities reported to Oracle by ERPScan, which said that it wasn’t credited in the advisory thanks to its status as a sanctioned Russian entity by the U.S. Treasury Department.
“Unfortunately, Oracle decided to dismiss ERPScan’s contribution and did not give a credit since ERPScan were put on a Treasury sanctions list,” the company said in an email. “As we see it, Treasury sanctions only prevent financial transactions and do not prohibit non-financial relationships. It means that if research teams only send information on vulnerabilities to the vendor, nothing prevents this company to give them a credit. Nonetheless, sanctions always raise concerns, and the situation is not very promising for anybody.”
In all, Oracle credited 43 independent researchers as well as analysts from Apple, GE, Google, Pulse Security, Trend Micro, Secunia and others.
Number of Vulnerabilities by Product











