The Panda threat group, best known for launching the widespread and successful 2018 “MassMiner” cryptomining malware campaign, has continued to use malware to mine cryptocurrency in more recent attacks. A fresh analysis of the group reveals Panda has adopted a newly-updated infrastructure, payloads and targeting.
While considered unsophisticated, researchers warn that the threat group has a wide reach and has attacked organizations in banking, healthcare, transportation and IT services. So far, researchers estimate that Panda has made away with more than $100,000 in Monero – and with attacks as recently as August 2019, the threat group isn’t ceasing its activities anytime soon, they said.
“Panda’s willingness to persistently exploit vulnerable web applications worldwide, their tools allowing them to traverse throughout networks, and their use of RATs, means that organizations worldwide are at risk of having their system resources misused for mining purposes or worse, such as exfiltration of valuable information,” said Christopher Evans and David Liebenberg with Cisco’s Talos research team.
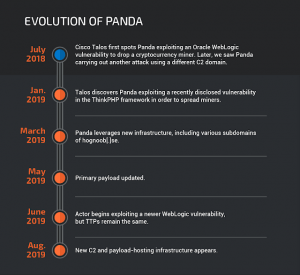
Researchers first became aware of Panda in the summer of 2018 after they engaged in a widespread illicit mining campaign called “MassMiner.” During that campaign, the threat actor used MassScan, a legitimate port scanner, to sniff out various vulnerabilities in servers to exploit, including a WebLogic vulnerability (CVE-2017-10271) and a remote code execution vulnerability in Apache Struts 2 (CVE-2017-5638).
The threat group then would exploit the flaws and install malware, which would set about mining for Monero and hooking up with a crypto-wallet and mining pool.
Since then, in 2019, researchers said that the threat group has constantly evolved to update its infrastructure, exploits and payloads.
“Shortly thereafter [the 2018 campaign], we linked Panda to another widespread illicit mining campaign with a different set of command and control (C2) servers,” researchers said. “We believe Panda is a legitimate threat capable of spreading cryptocurrency miners that can use up valuable computing resources and slow down networks and systems.”
Panda has constantly changed the vulnerabilities that it targets over the past year. For instance, in January 2019, Talos researchers saw Panda exploiting a recently-disclosed vulnerability in the ThinkPHP web framework (CNVD-2018-24942). And in June 2019, Panda began to target a newer WebLogic vulnerability (CVE-2019-2725) and leveraging an updated payload with new features to download a secondary miner payload.
In the most recent campaigns, including one which took place in August 2019, Panda began employing a different set of command-and-control (C2) servers as well as a new payload-hosting infrastructure.
In March 2019, for instance, researchers observed the actor leveraging new infrastructure, including various subdomains of the domain hognoob[.]se. And in August, researchers said they observed several attacker IPs, post-exploit, pulling down payloads from a newer URL and saving the file as “BBBBB” (a slight departure from previous behavior, when the file was saved under a random 20-character name). Panda would then execute the file via PowerShell.
Panda has changed up its payload over the summer as well, so that it’s initial payload now uses the Certutil command-line utility – which can be used to obtain certificate authority information and configure Certificate Services – to download the secondary miner payload.
Though the threat actor has swapped up its payloads, targeting and infrastructure, very little of its TTPs [tactics, techniques and procures] are sophisticated, Cisco’s Evans told Threatpost.
For instance, “They attempt to hide their miners using the exact same popular techniques we see with other groups,” he told Threatpost. “Their infrastructure is predictable: I can usually peg a new Panda domain as soon as I see it in the data; they tend to just be iterations of each other. Their early infrastructure was registered using an email address that immediately allowed Dave to pivot into their social media in China. They attack the same honeypots day after day with the same payloads. They don’t even bother to confirm their victims are running a vulnerable system before they deliver an exploit.”
Between swapping up its tactics, domains and payloads, researchers said that Panda has now made more than $100,000 through illicit cryptomining – and moving forward, Panda remains an active threat that system administers should be wary of.
“There are several ways to detect mining activity but let’s focus on the simple solutions of patching and basic security controls,” Evans told Threatpost. “If you’re running a web-accessible WebLogic server that has hasn’t been patched against vulnerabilities like CVE-2017-10271, it’s likely they have at least targeted the system for exploitation if not actually dropped a miner on it… In addition, if you don’t need it open to the Internet, take it off.”
Interested in the role of artificial intelligence in cybersecurity, for both offense and defense? Don’t miss our free Threatpost webinar, AI and Cybersecurity: Tools, Strategy and Advice, with senior editor Tara Seals and a panel of experts. Click here to register.