Despite a high-profile memory-related vulnerability in password managers capturing headlines last week, a recent Threatpost poll found that 84 percent of respondents use password managers – while only 10 percent said they don’t due to security risks.
There have been vulnerabilities found before in this kind of software, and malware has also been found targeting it. The latest issue allows a local adversary to crack open and steal passwords stored by the 1Password, Dashlane, KeePass and LastPass utilities; the firms have fiercely hit back on the assessment that this poses a serious risk.
Threatpost asked readers to weigh in on whether they embrace password managers or think they pose too much of a risk: And more than 700 respondents decided to weigh in on the poll.
A full 84 percent said that they do indeed use password managers, while only 10 percent felt that they’re too risky. However, individual comments showed that some don’t password-manager users still fully trust them.
“I use one for non-important password storage, important ones are in my mind,” said one respondent.
“They’re risky, but convenient,” said another.
Others weighed in on other concerns around these utilities. One respondent in the anti-password manager camp commented that they inspire a false sense of security; and another noted that “local banking contracts do not allow for their use.”
Humans: The Main Risk?
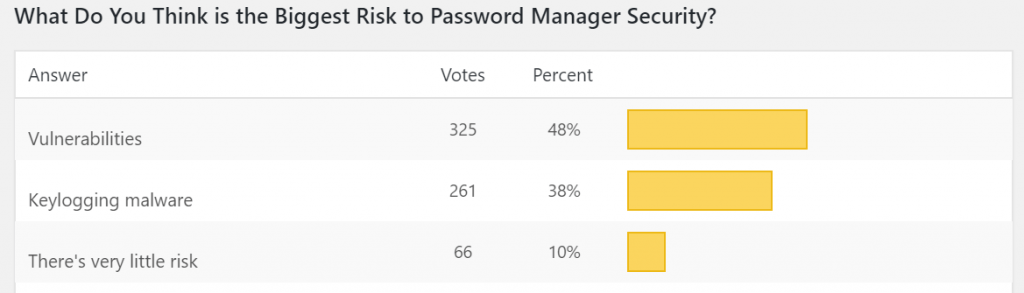
As far as the biggest risk to password-manager security, vulnerabilities (48 percent) and keylogging (38 percent) took the top places. Other individual answers included “man-in-the-browser malware,” “side-channel attacks” and “cloud-exposed vulnerabilities.”
But many respondents blamed a lack of user awareness, saying the greatest risk is: “Laziness, weak master password; non-use of 2FA,” “end users,” “humans”, “the person behind the keyboard” and “users not using a strong enough master password, or leaving the app ‘always on.'” And one respondent, unconcerned about putting too fine a point on it, simply said, “dumb people.”
Elaborating on this theme that the weakest point in password-manager security is the users, Threatpost reader “Brekmister,” commented: “Hackers will always find a way around and users will fall for it because they won’t know any better. If there are vulnerabilities in a piece of software and the user knows what they are doing then, ppfffttt yeah, whatever. Well, even then we are still human beings… The No. 1 key point to what I think can stop attacks is education for the users. Which frankly is too hard, so we just keep patching things.”
2FA: Making Managers Safer?
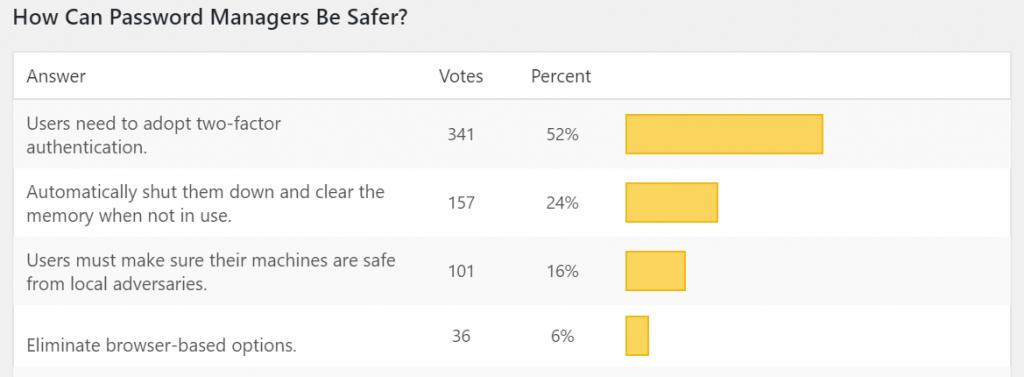
When it comes to how password managers could be safer, individual suggestions included eliminating web-based password managers, and better design so that passwords are securely stored in separate sandboxes. Auto-clearing memory and additional obfuscation of username/email addresses used for accounts were also mentioned. However, half (52 percent) said that users need to adopt two-factor authentication (2FA), making this the clear favorite for reducing risk.
However, “you cannot make password managers safer using 2FA,” said Threatpost reader Paul Moore. “If your password manager uses authentication over encryption, you have bigger issues. Several companies advertise 2FA support, but it’s not technically possible. It’s security theatre by the marketing department.”
Another reader named Rich argued that this is “not entirely true.”
He explained, “For password managers that store their vaults in the cloud, 2FA prevents phishing attacks from getting your vault, even if they get your master password. Otherwise I agree. If malware can keylog your master password, it can get the local cache of your vault.”
Another Threatpost reader, Diogene, noted that “encryption is much more important. The best solution is using a very long encryption key stored on a removable device that you keep physically separate from password manager data file most of the time.”
The Spreadsheet Effect
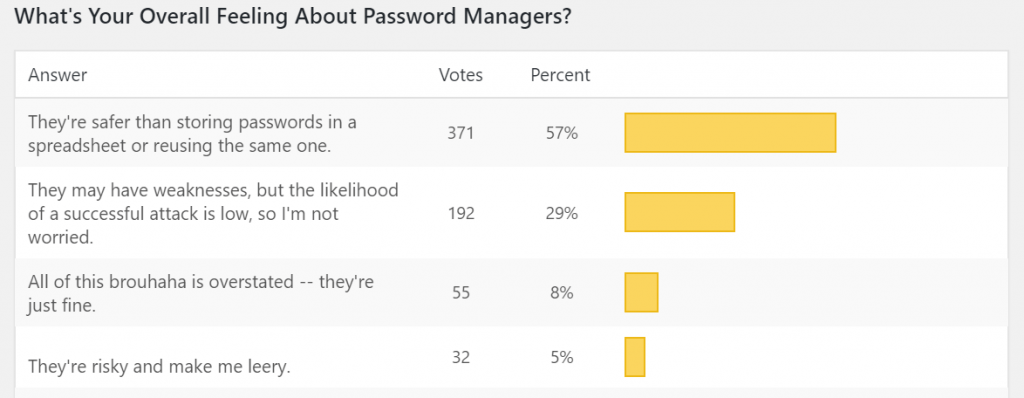
When asked about their overall attitude towards password managers, about half (56 percent) said they’re safer than storing passwords in a spreadsheet or reusing the same one for multiple accounts. One reader made the assessment that they’re “risky, better than spreadsheets and safety is only as good as security awareness.”
However, the idea of keeping a spreadsheet with passwords provoked an array of responses. One poll-taker said that he or she has eschewed a manager for “a list of passwords in an encrypted document.”
Similarly, “I don’t use a password manager,” one commentator said. “I do use a password-protected excel spreadsheet to hold my passwords. That way they are in my hands and not some third party. I also keep a hard-coded printout in a safe place.”
Don’t miss our free Threatpost webinar this Wednesday, Feb. 27 at 2 p.m. ET, featuring Patrick Hevesi of Gartner; Mike Burr of Google Android; and David Richardson from Lookout.
One reader listing himself as “Mark” argued with that line of thinking. “But what you’ve described is just how password managers work – they don’t share the passwords with third parties,” he said. “And even if you don’t trust LastPass, with managers like KeePass, there is no third party. And the recent security risks exposed likely affect your hand-made method too: When you view your decrypted passwords in excel, can you view one at a time? Are the passwords scrubbed from memory after you’ve viewed them? If not, you’re vulnerable in the same way.”
The Memory Flaw
The latest issue with password managers (1Password, Dashlane, KeePass and LastPass) at the time of testing by ISE was that each of the utilities stored either the master password or individual credentials on insecure memory on the PC. This could allow a local adversary or a remote attacker, who compromised the system, to obtain passwords maintained by the utilities.
The one exception, researchers note, is when the password managers are not in use.
“All password managers we examined sufficiently secured user secrets while in a ‘not running’ state. That is, if a password database were to be extracted from disk and if a strong master password was used, then brute forcing of a password manager would be computationally prohibitive,” ISE’s team explained.
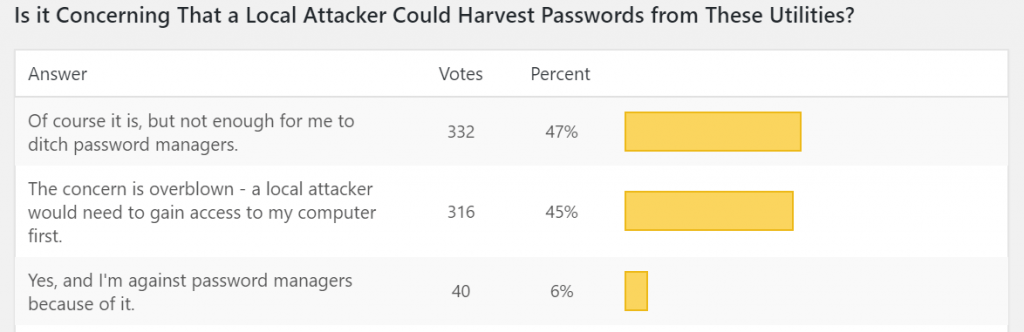
When asked if it’s concerning that a local attacker could harvest passwords using the latest vulnerability, about half (47 percent) of the Threatpost poll respondents agreed that it is, but “not enough for me to ditch password managers.”
“it’s scary, but I am still open to adapting a password manager,” one said. “This is why I set short lockouts and auth when needed,” said another.
In fact, just 6 percent said that the vulnerability is concerning and wards them off password managers.
“I switched password managers because of it,” said one. Another respondent added, “I’ll have to monitor how my password manager handles their weaknesses and adjust.”
About a third (29 percent) agreed that “they may have weaknesses, but the likelihood of a successful attack is low, so I’m not worried.”
Another almost half (45 percent) felt that the concern here is actually overblown given that a local attacker would need to gain access to the victim’s computer first.
Many of the comments noted that if one’s computer is already compromised, then the vulnerability become moot or at the very least, redundant.
“A local adversary can just install [a] keylogger,” as one pointed out. “Any password is vulnerable if the computer is compromised,” another respondent noted. Other assessments included, “If your device is compromised, so are you. No software can protect you.” And, “an attacker with access to my computer can harvest my passwords anyways.”
Even so, as one Threatpost reader commented, the vulnerability should be fixed.
“All password management software has to review how they store master passwords and the passwords database,” the reader said. “In all cases, the master password should not be held in memory if not needed. At the same time, the passwords database should not be loaded fully into memory (like some password-management software does). Only single entry (which is used at the moment) should be in memory, and once used, should be removed, so nothing can be scraped from memory.”
Interested in learning more about mobile enterprise security threats and best practices? Don’t miss our free Threatpost webinar this Wednesday, Feb. 27 at 2 p.m. ET.
Patrick Hevesi of Gartner; Mike Burr of Google Android; and David Richardson from Lookout will join Threatpost senior editor Tara Seals.
They’ll discuss the top evolving threats and risks that are unique to this work-from-anywhere environment; best practices for addressing them; and new challenges on the horizon, such as 5G services.