 A fresh batch of malicious PDFs is making the rounds via email, with the attackers trying to trick users into opening the files by making them look like instructions for an update to their email accounts. The difference this time, however, is that the attack uses a technique recently published by a researcher that takes advantage of the /launch command in Adobe software.
A fresh batch of malicious PDFs is making the rounds via email, with the attackers trying to trick users into opening the files by making them look like instructions for an update to their email accounts. The difference this time, however, is that the attack uses a technique recently published by a researcher that takes advantage of the /launch command in Adobe software.
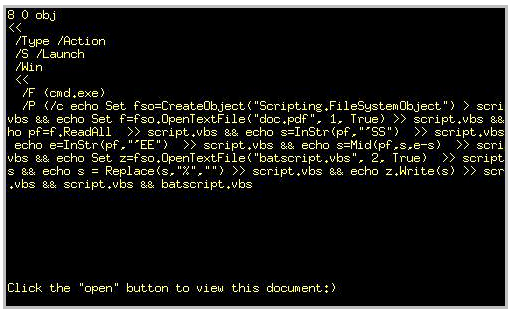
The technique, which was identified by researcher Didier Stevens recently, enables an attacker to launch commands and open file attachments on users’ machines. The attack produces a warning dialogue box, but users are accustomed to seeing, and ignoring, those in many situations. In this particular new malware campaign, the attackers have used that tactic, along with adding some extra white space to the dialogue box to make it look less suspicious.
Researchers at IBM ISS’ X-Force analyzed the new malicious PDFs and found that their creators had a good understanding of Stevens’s technique. Once a victim opens the email and clicks on the infected attachment, he’ll see a warning box. If he clicks “open”, Adobe Acrobat or Reader will launch cmd.exe, which creates a few scripts on the machine.
The ultimate payload of the malware is a file called game.exe, which turns out to be a variant of the Auraax or Emold worm, ISS said.
Disabling JavaScript does not prevent this technique from exploiting PDF readers, Stevens said at the time of his disclosure. “With Adobe Reader, the only thing preventing execution is a warning.
Disabling JavaScript will not prevent this (I don’t use JavaScript in my
PoC PDF), and patching Adobe Reader isn’t possible (I’m not exploiting a
vulnerability, just being creative with the PDF language specs),” he wrote.









