A phishing campaign that takes advantage of Google’s ability to decode non-ASCII URL data on the fly is making the rounds – looking to fool the unsavvy by effectively hiding the website address of the campaign’s phishing page.
The campaign makes use of what’s called percentage-based URL encoding – a basic URL-encoding technique in which normal ASCII characters (i.e., “abc” and “123”) are converted into a string that starts with “%” and is followed by two hexadecimal digits. When resolving such an address, Google will convert this non-ASCII format into a string that is universally accepted and understood by all web browsers and servers, on the fly.
The cybercrooks are making use of this in order to trick secure email gateways (SEG) into delivering their phishing emails, by hiding the true destination of the messages’ embedded malicious links. That’s according to the Cofense Phishing Defense Center, which last week observed a specific campaign using the method.
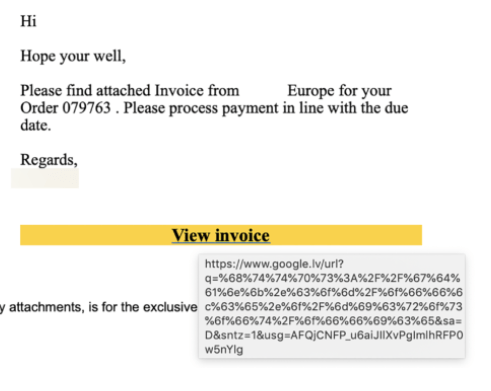
“The phishing email is simple and originates from a compromised email account of a relatively well-known American brand, informing recipients that they have a new invoice awaiting payment,” explained Milo Salvia, Cofense researcher, in a posting on Wednesday, noting that the phishing page itself is a well-done imitation of the Office 365 login portal and aims to steal corporate users’ credentials. He added, “The email body has an embedded hyperlink button, highlighted in yellow, where users can click to view the invoice.”
Here’s where the trickery comes in: The hyperlink button’s address is presented with percentage-based encoding, as seen here – thus obscuring the true destination of the hyperlink:
“[The URL’s destination] is not immediately obvious to the untrained eye, and unfortunately the same is true for many perimeter security devices,” explained Salvia. In other words, it’s possible to slip past email gateways that don’t have decoding ability. However, there’s a second wrinkle to the campaign’s efforts: The URL’s top-level domain is the legitimate Google Latvia homepage address (google.lv).
The use of a benign top-level domain can further flummox email defenses, but to boot, the campaign is making use of Google’s auto-decoding function. Specifically, it’s using it to redirect the recipient to a secondary malicious URL that’s hiding in the encoded part of the string.
“The first part of the URL is benign “hxxps://google.lv/url?q=”, which tells the web browser to use Google to query a specific URL…the second part of the string is the payload,” explained Salvia. “When users click on the hyperlink within the email, they are redirected through their browsers to Google to query the encoded string. This is recognized as a URL to redirect the user to the final destination of the malicious payload.”
This simple but effective approach gets around basic URL and domain checks by perimeter devices, according to the researcher.
Techniques like these have translated into phishing effectiveness continuing to hold steady. According to a recent phishing survey from Webroot, a majority (79 percent) of people reported being able to distinguish a phishing message from a genuine one – yet nearly half (48 percent) of respondents said their personal or financial data had been compromised by a phishing message.
Also, nearly half (49 percent) also admitted to having clicked on a link from an unknown sender while at work, with nearly one third of respondents overall (29 percent) admitting to doing so more than once. Of those who clicked a link from an unknown sender at work, most (74 percent) did so via email.
“This [percentage-encoding] campaign highlights the ingenuity with which digital criminals craft increasingly more sophisticated phishing attacks,” said David Bisson, researcher at Tripwire, in a posting on the campaign. “Acknowledging this trend, organizations have an incentive to educate their entire workforce about the dangers of phishing.”
What are the top cybersecurity issues associated with privileged account access and credential governance? Experts from Thycotic will discuss during our upcoming free Threatpost webinar, “Hackers and Security Pros: Where They Agree & Disagree When It Comes to Your Privileged Access Security.” Click here to register.