An ongoing three-year-old phishing campaign has been targeting the credentials of Saudi Arabian government agencies — with a financially motivated actor the likely culprit.
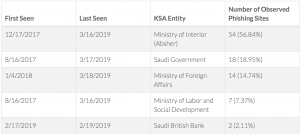
The campaign, code-named “Bad Tidings,” has siphoned victims’ credentials by pretending to be the Kingdom’s Ministry of Interior’s e-Service portal, known as “Absher.” The recent emails have targeted four government entities: the Ministry of Interior, Saudi Government, Ministry of Foreign Affairs and the Ministry of Labor and Social Development – as well as the Saudi British Bank.
While the campaign has been ongoing since November 2016, researchers with Anomali said that in the past few months, the number of phishing landing pages has suddenly spiked.
“Anomali and [Saudi Telecom Company] believe the Bad Tidings campaign’s heavy focus on the Kingdom of Saudi Arabia (KSA)’s government agencies electronic services is reflective of information-gathering operations employed by a financially-motivated actor or group attempting to steal and monetize personally identifiable information (PII) and other sensitive data,” researchers said in a Tuesday post.
Fake Landing Page
Since it first started in 2016, the campaign has used a total of 95 unique phishing host names to target its victims.
These were created as part of the campaign to impersonate the aforementioned Absher, which represents close to 60 percent of the Saudi-related phishing sites. The e-Service portal helps users with employment, passports, civil affairs, traffic services and more.
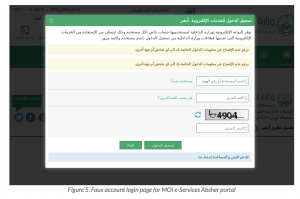
The phishing landing pages in the campaign would typically contain two web pages: A fake homepage, and a login page.
The fake login pages appear to display the legitimate account access portal for Absher – however, when users provide their user ID and password, they are redirected to the initial phishing landing page without logging into the intended resource.
“Typically, at this stage the phishers have stolen the user’s credentials and are likely to sell them on underground markets or use them to impersonate the victim to commit fraudulent actions,” researchers said.
Tricks and Tactics
The attackers have used multiple spoofing techniques to disguise the fraudulent sites, researchers said.
“We have observed the attackers creating sites using either a single or combined technique of punycode-based spoofing attacks, typosquatting or sub-domain spoofing attacks,” researchers said.
Researchers said that to trick users, the websites that were created were using slightly misspelled domain names (a technique called “typosquatting,” which registers domains that can be confused for the legitimate site or brand name by incorporating hard-to-spot spelling or grammatical errors); subdomain spoofing, using alternative top level domains (TLDs) (i.e., near-identical URL names that use something other than the legitimate gov.sa suffix), or punycode-based sites to masquerade as the real portal. Punycode is a method of representing International Domain Names in local language characters, which are normally limited by letters or hyphens when supported by DNS.
“For example, the Absher portal is a web page located underneath the website https://www.moi.gov.sa/; however, malicious actors have appropriated the brand name ‘Absher’ to create typosquatting domains with misspellings and wrong TLDs e.g. abshr[.]xyz or simply wrong TLDs e.g. absher[.]space,” said researchers.
Moving forward, researchers said they expect the campaign to continue targeting Saudi government e-services using phishing attacks, either via email or text message.
“Online government portals offering citizen services remain attractive targets, as they store vast amounts of personal and sensitive information in a centralized location and if compromised, can provide malicious actors with enough data for resale on underground markets or to commit fraudulent actions such as identity theft,” the researchers said.