Research shows that the cost of phishing attacks has nearly quadrupled over the past six years: Large U.S. companies are now losing, on average, $14.8 million annually, or $1,500 per employee.
That’s up sharply from 2015’s figure of $3.8 million, according to a new study from Ponemon Institute that was sponsored by Proofpoint.
According to the study, released Tuesday, phishing leads to some of the costliest cyberattacks.

One of the most expensive threat types is business email compromise (BEC). BEC costs ramped up significantly in 2020, with more than $1.8 billion stolen from organizations as cybercrooks launch ever slicker attacks, either impersonating someone inside an organization or masquerading as a partner or vendor in order to pull off financial scams.
One of the other most expensive attacks is ransomware, as experts have tracked skyrocketing ransom costs.
But what businesses shell out for extortion payments in ransomware attacks or what gets jimmied out of them in fraudulent BEC wire transfers are both just portions of the true costs of phishing attacks, according to the study, titled The 2021 Cost of Phishing.
“When people learn that an organization paid millions to resolve a ransomware issue, they assume that fixing it cost the company just the ransom. What we found is that ransoms alone account for less than 20 percent of the cost of a ransomware attack,” said Larry Ponemon, chairman and founder of Ponemon Institute, in a press release. “Because phishing attacks increase the likelihood of a data breach and business disruption, most of the costs incurred by companies come from lost productivity and remediation of the issue rather than the actual ransom paid to the attackers.”
Lost Productivity is the Biggest Gotcha
It’s the lost productivity and mopping up that eat up the lion’s share of the costs of phishing attacks, with a host of other investigative and compliance costs in the mix. Below is a table that summarizes the annual hours incurred for six tasks by the average-sized organization on an annual basis. As it depicts, the most time-consuming tasks to resolve phishing scams are the cleaning and fixing of infected systems and conducting forensic investigations.
The study found that in an average-sized U.S. corporation of 9,567 people, that lost productivity translates to 63,343 wasted hours every year. Each employee wastes an average of 7 hours annually due to phishing scams: an increase from 4 hours in 2015.

Estimated hours per employee each year spent dealing with phishing scams. Source: Ponemon Institute.
The study, initially conducted in 2015, surveyed nearly 600 IT and IT security practitioners.
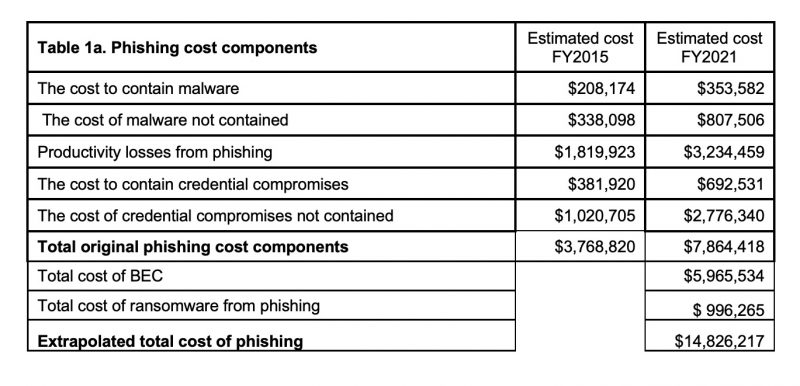
Researchers found that the average annual cost of phishing has increased from $3.8 million in 2015 to $14.83 million in 2021. As the table shows, productivity losses have spiked, from $1.8 million in FY2015 to $3.2 million in FY2021. (Information about BEC and ransomware wasn’t available in FY2015.) In this, the most current study, annual cost of phishing for BEC was estimated to be $5.97 million, while average ransomware costs were estimated to total $996,000.
The BEC Blues
Some of the study’s key takeaways:
- BEC costs nearly $6 million annually for a large organization. Of that, illicit payments made annually to BEC attackers is $1.17 million.
- Ransomware annually costs large organizations $5.66 million. Of that, only $790,000 accounts for the paid ransoms themselves.
- Security awareness training reduces phishing expenses by more than 50 percent on average.
- Costs for resolving malware infections have more than doubled since 2015. The average total cost to resolve malware attacks is $807,506 in 2021, an increase from $338,098 in 2015.
- Credential compromise costs have increased dramatically since 2015. As a result, organizations are spending more to respond. The average cost to contain phishing-based credential compromises increased from $381,920 in 2015 to $692,531 in 2021. Organizations experienced an average of 5.3 compromises over a 12-month period.
- Business leaders should pay attention to probable maximum loss scenarios. For instance, BEC attacks could incur losses from business disruptions of up to $157 million if organizations aren’t prepared. Malware resulting in data exfiltration could cost businesses up to $137 million.
Ryan Kalember, executive vice president of cybersecurity strategy for Proofpoint, said in a release that the cost of credential compromise has “exploded” in recent years due to threat actors targeting employees instead of networks. It leaves the door “wide-open for much more devastating attacks like BEC and ransomware,” he said. “Until organizations deploy a people-centric approach to cybersecurity that includes security awareness training and integrated threat protection to stop and remediate threats, phishing attacks will continue.”
![]() Worried about where the next attack is coming from? We’ve got your back. REGISTER NOW for our upcoming live webinar, How to Think Like a Threat Actor, in partnership with Uptycs on Aug. 17 at 11 AM EST and find out precisely where attackers are targeting you and how to get there first. Join host Becky Bracken and Uptycs researchers Amit Malik and Ashwin Vamshi on Aug. 17 at 11AM EST for this LIVE discussion.
Worried about where the next attack is coming from? We’ve got your back. REGISTER NOW for our upcoming live webinar, How to Think Like a Threat Actor, in partnership with Uptycs on Aug. 17 at 11 AM EST and find out precisely where attackers are targeting you and how to get there first. Join host Becky Bracken and Uptycs researchers Amit Malik and Ashwin Vamshi on Aug. 17 at 11AM EST for this LIVE discussion.