Colonial Pipeline Co. may have turned off the tap following Friday’s ransomware attack, but the news about the devastating assault keeps gushing.
In the wake of the DarkSide cyberattack, President Biden signed an executive order Wednesday aimed at bolstering the federal government’s cyber defenses as the administration juggles a number of digital attacks including SolarWinds and last week’s ransomware incident against a major fuel pipeline causing lasting gas shortages.
While not specifically targeting critical infrastructure, the Biden directive instructs the Commerce Department to create new cybersecurity standards for tech companies that sell software services to the federal government.
“The Colonial Pipeline incident is a reminder that federal action alone is not enough,” the White House said in a statement.
IRL Dark Side of Pipeline Cyberattack
As of 5 p.m. on Wednesday evening, Colonial was sputtering back to life after closing the fuel faucet to the eastern and southern U.S.; the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) had issued a joint advisory about the threat actor – DarkSide – that mugged the company; and five affiliated crooks that rent DarkSide ransomware had been fingered by Mandiant FireEye.
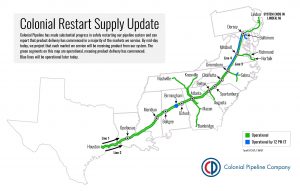
051321 09:22 UPDATE: Colonial announced that as of 9 a.m. Eastern on Thursday, delivery was back up in a majority of the markets it services. It projected that all of its markets would be getting fuel by mid-day. The company included a map, shown below, that indicates the segments of its pipeline that are now delivering liquid fuel, in green, with blue lines showing which lines will be back online later today.
Following the Biden administration’s declaration of a state of emergency across 17 states and Washington D.C., the nation convulsed at the thought that fuel was going to – what? Evaporate, maybe, or, at least, get a bit pricey? By Wednesday, the Twitterverse was featuring images of people stockpiling gasoline in any old thing they could get their hands on: sloshing-full trash bags, stacked piles of red gas canisters in the trunk of a car that hopefully wasn’t fated to be rear-ended, you name it.
Thus did the hashtag #gasshortage spring to life.
Better pick up a couple extra bags.
Oh, shit. #gasshortage? Better pick up a couple extra bags. pic.twitter.com/a09ue2eQfK
— Fiendishly Yours, (@FiendishlyYours) May 11, 2021
Colonial Restarts the Petro Heart of the Right Coast
You can see why the public had a buy-all-the-toilet-paper reaction to the hit on the nation’s fuel delivery infrastructure: Colonial carries 45 percent of fuel supplies to the eastern U.S.
Right now, things are on the road back to normal. Colonial issued a statement saying that it initiated the restart of pipeline operations around 5 p.m. Eastern on Wednesday.
Colonial, which moves about 2.5 million barrels of liquid fuels to the eastern and southern U.S. every day, had proactively shut down about 5,500 miles of pipeline in response to Friday’s attack.
The company said that it will take several days for its product delivery supply chain to return to normal. There may be some hiccups along the way: “Some markets served by Colonial Pipeline may experience, or continue to experience, intermittent service interruptions during the start-up period,” according to its statement. “Colonial will move as much gasoline, diesel, and jet fuel as is safely possible and will continue to do so until markets return to normal.”
Colonial, which has been working closely with law enforcement, the Department of Energy and the cybersecurity firm FireEye to mitigate the damage and restore operations, reportedly has no plans to pay the ransom to get its files decrypted, according to what sources told Reuters on Wednesday. DarkSide reportedly demanded nearly $5 million worth of Bitcoin in ransom, according to sources familiar with the incident.
On Wednesday, DarkSide said on its website that it was releasing data from three more victims, including a technology company in Chicago.
Finger Pointing
Earlier this week, President Biden said that Russia should bear some responsibility for the infrastructure disruption, since the hacking came from inside its borders. However, two people involved with the Colonial investigation told Reuters that the affiliate who launched the ransomware attack against Colonial was a Russian criminal, not a threat actor with specific ties to the Russian government.
DarkSide is, rather, one of the for-profit ransomware groups that call Russia their home. These cyber-gangs rent ransomware such as DarkSide, use it to steal companies’ data, and then hold it for ransoms ranging from $200,000 to $20 million.
CISA and FBI Ring the Alarm Bell
The fuel-buying public may experience some relief at the news about the pipeline restart, but the nation’s law enforcement agencies warned us that this is no time to relax. In a joint advisory, CISA and the FBI said that DarkSide affiliates leveraging DarkSide have recently been targeting organizations in industries including manufacturing, legal, insurance, healthcare, and energy.
Prevention is the best cure for this ransomware plague, the agencies said. They urged potential targets to use best practices in these resources to strengthen their cybersecurity posture:
- CISA and Multi-State Information Sharing and Analysis Center: Joint Ransomware Guide
- CISA webpage: Ransomware Guidance and Resources
- CISA Insights: Ransomware Outbreak
- CISA Pipeline Cybersecurity Initiative
- CISA Pipeline Cybersecurity Resources Library
Nozomi Networks CEO Edgard Capdevielle told Threatpost on Wednesday that the joint advisory is spot-on: Ransomware truly is a cyber pandemic. “Ransomware is out of control,” he said via email. “The FBI stats say it all – attacks were up 20 percent last year – and even more telling, ransom demands rose 225 percent. Attackers are going after higher-value targets with deeper pockets, which means critical infrastructure is in the cross hairs. Nozomi saw a 35 percent increase in grid attacks during COVID – a number that has remained steady since effective prevention measures combined with a post-breach mindset are critical to an effective defense.”
Even better than advice about best practices would be government action, he said. “My hope [in] this is where we finally turn a corner. We need organizations to stop waiting for attacks to prioritize their defenses, and we need the government to take necessary action to hold threat actors accountable.”
Capdevielle suggested that what the nation’s critical infrastructure organizations need are more aggressive programs and incentives, including tax breaks for cybersecurity or perhaps even entrusting private companies to take on their defense.
“From our work with critical infrastructure and industrial organizations around the world, we’ve found that those who invest early in cybersecurity are able to respond faster and with less financial damage to ransomware and other cyber-attacks” Capdevielle said. “Enterprises with mature cybersecurity are more resilient and able to navigate those challenges easier than those that waited until an incident to invest in their defenses.
“Frankly, it’s complicated,” he said. “There isn’t an easy solution, and real results must navigate government politics, privacy law, and international laws, and will require cooperation from nation-state adversaries. It’s not a simple task, but we can take steps now to solve the problem. Waiting will only make it more difficult to solve.”
Researchers Spy on DarkSide
Meanwhile, Mandiant FireEye released a new report on DarkSide that detailed three groups of affiliate threat actors that the firm has been tracking.
FireEye said that the creators of DarkSide and their affiliates have affected organizations in 15+ countries and multiple industries, pulling the double-extortion gambit of exfiltrating victim data, deploying the DarkSide ransomware, and then threatening to publish the stolen data to their blog in order to pressure victims into paying the ransom.
For what it’s worth, be it a publicity stunt or yet another attempt to portray themselves as crooks with ethics, DarkSide issued a mea culpa on the Colonial attack, calling it a “very big oops.” Our bad, they said: We were just after moolah, not the kneecapping of the nation’s infrastructure. We’ll vet our criminal customers better in the future, they promised.
The Affiliates That FireEye’s Eyeballing
FireEye tracks DarkSide activity in three different clusters of groups that it defines as UNC2628, UNC2659 and UNC2465. UNC2628 tends to use the Cobalt Strike framework and Beacon payloads, sometimes uses Mimikatz for credential theft and exfiltration, and has even deployed F-Secure’s custom command and control framework. For its part, the UNC2659 threat actor uses TeamViewer to establish persistence, while UNC2465 – which has been active for the longest of the DarkSide affiliate trio – delivers the PowerShell-based .NET backdoor known as SmokedHam.
Here are more details about the groups:
UNC2628
This threat actor isn’t interested in gaining a foothold to set up shop for the long term. Rather, it moves fairly quickly, with intrusions escalating to ransomware infection within two to three days. FireEye said it has some evidence suggesting that UNC2628 has also partnered with other RaaS networks, including Sodinokibi (aka REvil) and NetWalker ransomwares.
Researchers have seen UNC2628 make suspicious authentication attempts – consistent with a password-spraying attack – against corporate VPNs immediately prior to starting intrusion operations. Regardless of how it intrudes on victimized networks, it’s moved laterally in environments almost exclusively via Remote Desktop Protocol (RDP), using legitimate credentials and the Cobalt Strike commodity malware and Beacon payloads.
UNC2659
FireEye says this actor has been active since at least January 2021. Researchers have seen it cycle through the entire attack lifecycle in fewer than 10 days. One notable detail is its exploitation of zero days in SonicWall’s SMA100 SSL VPN, which SonicWall patched in January. “The threat actor appeared to download several tools used for various phases of the attack lifecycle directly from those tools’ legitimate public websites,” researchers said in FireEye’s report.
UNC2465
This actor has been around since at least April 2019. Researchers say that uses phishing emails and legitimate services to distribute the PowerShell-based SmokedHam: a .NET backdoor that supports keylogging, screenshot captures, and executing arbitrary .NET commands. FireEye tracked one case in which DarkSide was deployed, with months-long gaps, with only intermittent activity between the time of initial compromise to ransomware deployment. Researchers suggested that this “could indicate that initial access was provided by a separate actor.”
DarkSide Is Raking It In
While the country recovers from the attack and cybersecurity researchers dissect DarkSide, DarkSide itself must surely be laughing all the way to the bank. Joe Tidy, a cybercrime reporter for the BBC, noted that DarkSide’s bringing in some eye-watering profit, judging by the figures cited in FireEye’s report. “The money they must be making,” he tweeted. “In 2019 I remember the outrage caused by news that ransoms were hitting $1m. Now these ransomware groups have a specific commission band for $5m+.”
051321 09:22 UPDATE: Added Colonial’s update about fuel delivery getting back to normal on Thursday.
051321 13:56 UPDATE: Corrected Edgard Capdevielle’s reference to the increase in ransom demands, which the FBI says have increased 225 percent.
Join Threatpost for “Fortifying Your Business Against Ransomware, DDoS & Cryptojacking Attacks” – a LIVE roundtable event on Wed, May 12 at 2:00 PM EDT. Sponsored by Zoho ManageEngine, Threatpost host Becky Bracken moderates an expert panel discussing best defense strategies for these 2021 threats. Questions and LIVE audience participation encouraged. Join the lively discussion and Register HERE for free.