A new hacking technique used against vulnerable MikroTik routers gives attackers the ability to execute remote code on affected devices. The technique is yet another security blow against the MikroTik router family. Previous hacks have left the routers open to device failures, cyptojacking and network eavesdropping.
The hacking technique, found by Tenable Research and outlined on Sunday at DerbyCon 8.0 in Louisville, Kentucky, is tied to the existing directory traversal bug (CVE-2018-14847) found and patched in April. That vulnerability was rated medium in severity and impacted Winbox, which is a management component and a Windows GUI application for MikroTik’s RouterOS software.
Tenable Research says it has found a new attack technique that exploits the same bug (CVE-2018-14847) that allows for unauthenticated remote code execution. “By exploiting the flaw, the remote attacker can get a root shell on the device as well as bypass the router’s firewall, gain access to the internal network, and even load malware onto victims’ systems undetected,” Tenable Research said in a blog post accompanying the presentation.
The underlying flaw is tied to a Winbox Any Directory File that allows threat actors to read files that flow through the router without authentication. The new technique, found by Jacob Baines, researcher at Tenable Research, goes one step further allowing an adversary to write files to the router. Baines also created a proof of concept of the attack outlined Sunday.
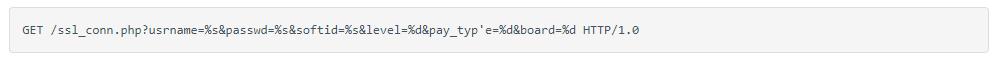
“The licupgr binary has an sprintf that an authenticated user can use to trigger a stack buffer overflow. The sprintf is used on the following string:
“Where the user has control of the username and password strings, an authenticated user can exploit this to gain root access to the underlying system,” he wrote.
This is as bad as it gets, Baines told Threatpost. “This bug was reported in April, but we are now able to show how an attacker can use it to get root shell on a system. It uses CVE-2018-14847 to leak the admin credentials first and then an authenticated code path gives us a back door.”
While MikroTik patched CVE-2018-14847 in early August, a recent scan by Tenable Research revealed only approximately 30 percent of vulnerable modems have been patched, which leaves approximately 200,000 routers vulnerable to attack. MikroTik’s RouterOS powers the company’s business-grade RouterBOARD brand, as well as ISP/carrier-grade gear from the vendor.
“Based on Shodan analysis, there are hundreds of thousands of MikroTik deployments worldwide, with strong concentrations in Brazil, Indonesia, China, the Russian Federation and India. As of the October 3, 2018, approximately 35,000 – 40,000 devices display an updated, patched version,” Tenable Research wrote.
The read version of the vulnerability is currently being exploited by a number of different campaigns. In August, it was reported 3,700 MikroTik routers were being abused in a cyptojacking campaign. Last month, 360 Netlab reported that 7,500 MikroTik were forwarding their owners’ traffic to eavesdropping cybercriminals. MikroTik routers have also been targeted by threat actors behind the malware VPNFilter who also used CVE-2018-14847.
Tenable researcher Baines said he is not aware of the technique being exploited in the wild. He said MikroTik’s patch for affected RouterOS versions 6.40.9, 6.42.7 and 6.43 stops all attack techniques associated with CVE-2018-14847.
On Sunday, Tenable Research also announced it had discovered additional MikroTik RouterOS vulnerabilities. The vulnerabilities include a stack buffer overflow vulnerability (CVE-2018-1156), a file upload memory exhaustion (CVE-2018-1157), a www memory corruption (CVE-2018-1159) and a recursive parsing stack exhaustion (CVE-2018-1158).