Employees are demanding that employers enable flexible workstyles. Apps are moving to the cloud. A company’s device and application mix are increasingly heterogeneous. All of these factors are breaking down the enterprise security perimeter, rendering traditional security approaches obsolete, and paving the way for zero-trust approaches.
Traditional security methods broadly classify everything (users, devices and applications) inside the corporate network as trustworthy. These models leverage legacy technologies, such as virtual private networks (VPNs) and network access control (NAC), to verify the credentials of users outside the network before granting access. The focus therefore is on strengthening the network perimeter and then granting full access to corporate data once credentials are successfully validated. This is sometimes referred to as the “castle and moat” approach, in which the castle refers to the enterprise holding valuable data and applications, while the moat refers to layers of protection aiming to keep potential threats out.
However, in today’s complex IT world, in which users access all types of apps (software-as-a-service, on-prem, native, virtual) from all types of devices (mobile, desktop, internet of things) and from many locations both inside and outside the corporate network, organizations need a security model that is dynamic, flexible and simple. Perhaps the most notable of the emerging security models is zero trust.
“Zero trust” is a phrase first coined by John Kindervag of Forrester in 2010 to describe the need to move security leaders away from a failed perimeter-centric approach and guide them to a model that relies on continuous verification of trust across every device, user and application. It does this by pivoting from a “trust but verify” to “never trust/,always verify” approach. In practice, this model considers all resources to be external and continuously verifies trust before granting only the required access.
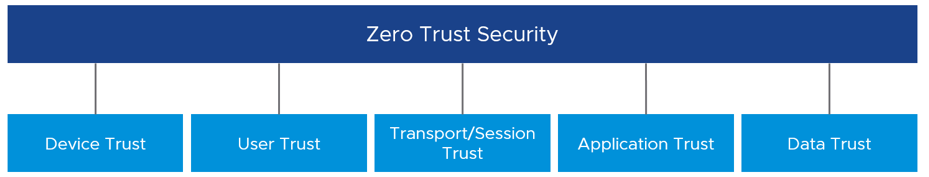
This all makes sense in theory, but what does implementing zero trust look like in practical terms? When talking to customers about steps they can take to build a zero-trust security architecture, I focus on five main pillars – device trust, user trust, transport/session trust, application trust and data trust.
Let’s take a closer look at each of these pillars and the underlying technology required to establish trust in each one.
Device Trust: For zero trust, as an IT administrator, you need to know your devices before you can trust them. You must have an inventory specifying which devices are owned and thereby controlled by your company. You must have a solution that monitors, manages and controls these devices. By interrogating the device posture, you can determine if the device can be trusted and if the device is compliant, based on pre-determined security policies. A unified endpoint management (UEM) solution enables IT teams to manage, monitor and control all devices – mobile, desktop, rugged and IoT – across all platforms from a single console. And, integrating endpoint detection and response (EDR) technology can further improve device security posture by further enabling the detection of possible malicious endpoint activities.
User Trust: Time after time, password-based user authentication has been proven inefficient and ineffective. Therefore, as a part of zero trust, organizations must make use of more secure user authentication methods. A strong conditional access engine, for instance, can make decisions using dynamic and contextual data. Technology building blocks to enable a strong conditional-access engine include password-less authentication (e.g., biometrics, certificates), multi-factor authentication (MFA), conditional-access policies and dynamic risk scoring.
Transport/Session Trust: Another key component of zero trust is the concept of least-privilege access. The idea is that a user or system should have access to only those resources that are specifically required to perform the task at hand. No more, no less. By using the principle of least-privilege access to resources, we limit access to users and grant the minimum permissions required to perform their work. Technology building blocks to help implement least-privilege access include micro-segmentation, transport encryption and session protection. Per-app tunnel, as a specific example, lets certain applications access internal resources on an app-by-app basis. This restriction means that you can enable some apps to access internal resources while you leave others unable to communicate with your back-end systems.
Application Trust: Enabling employees to securely and seamlessly access any application, including traditional Windows applications, from any device is key to creating a digital workspace and enforcing zero trust. With the modernization of user authentication, allowing single sign-on (SSO) to applications, we gain both security and an improved user experience. For traditional applications that are not designed for zero trust, we add protection in the form of isolation. In order to isolate and modernize traditional applications, one can utilize a virtual desktop or application environment to create a bridge between the traditional architecture and the future based on zero trust.
Data Trust: At the end of the day, it is the data that is of utmost importance — and the whole reason we need strong security. We must protect against data breaches and leaks, and make sure it is the correct, unmodified data that our users are interacting with. Technologies such as data loss prevention (DLP) ensure unwanted exfiltration or destruction of sensitive data. Although data classification and integrity are, for the most part, handled by the application itself, we should enhance the trust level wherever we can when building a zero-trust architecture.
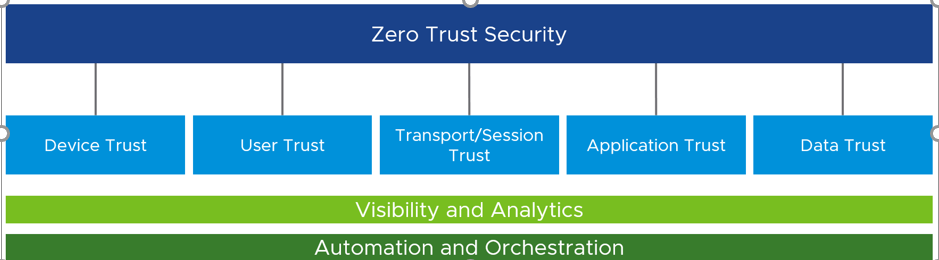
Once trust is established across all five pillars, informed decisions can be made to grant or deny access. Once the decision of granting access has been made, it is critical to constantly re-verify. If the trust level changes, organizations must be able to immediately act. In addition, by establishing trust across the five pillars, we gain visibility and can gather analytics across the digital workspace environment. And with visibility and analytics, we can build automation and orchestration.
You can see above how all five of these pillars can come together to provide security organizations with a holistic platform-based approach that combines rich context from users, devices, applications and more with conditional access policies. While there are a few required technology blocks, getting to zero trust is a non-linear journey. The journey is one that is not arduous nor impossible but one that requires IT and infosec teams to architect and build towards, in order to address all the different attack vectors in a digital workspace.
Tony Kueh is vice president of product management, End User Computing, VMware.
Enjoy additional insights from Threatpost’s InfoSec Insider community by visiting our microsite.