Admittedly, the payouts for Apple’s bug bounty announced last week at Black Hat drew mixed reactions ranging from reasonable to raucously funny.
Apple made a big splash at the annual hacker conference, first via a last-minute announcement that well-regarded Ivan Krstic would be giving a talk on some of the inner workings of iOS 10 security features, and then during Krstic’s talk, the curtain was pulled back on the bounty program.
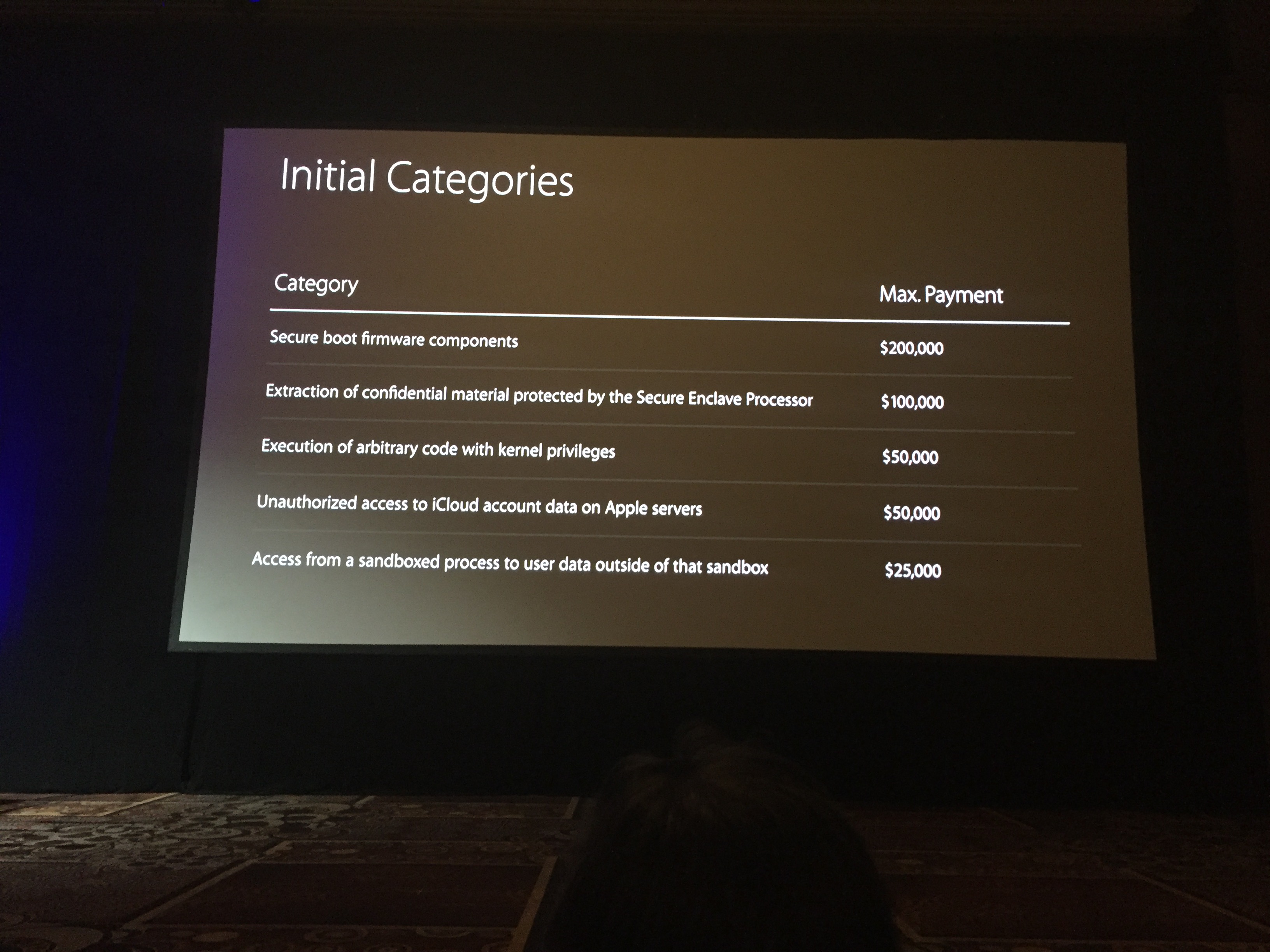
Apple is offering researchers a maximum payout of $200,000 for SecureBoot firmware compromises. Five areas of iOS are in scope for payouts ranging at the low end of $25,000 for sandbox escapes, upwards to $50,000 for bugs allowing access to iCloud accounts on Apple’s servers and code execution bugs at the kernel level, to $100,000 for exploits against the Secure Enclave Processor.
Given that it’s well known the black market has paid seven figures in the past for iOS bugs and last year, zero-day buyers Zerodium offered a $1 million iOS bounty, Apple’s payouts do pale a tad despite being among the highest corporate bug bounty payouts on record.
Then yesterday, Exodus Intelligence announced its Research Sponsorship Program, an acquisition program focusing on zero-day and N-day vulnerabilities and exploits that further dampened the hype around Apple’s new program. Exodus’ so-called zero-day Hitlist, or payment structure, severely undercuts Apple’s bounty program by offering a $500,000 maximum for iOS 9.3+ bugs.
Exodus is also offering six figures for Google Chrome and Microsoft Edge zero days ($150,000 and $125,000 respectively), $80,000 for Firefox, $75,000 for Windows 10 local privilege escalation zero-days, and $60,000 each for 0day in Adobe Flash and Reader.
Exodus also described a unique payment system that includes bonuses paid out until the zero day is patched.
“For each new Zero-Day acquired, Exodus will offer the researcher an initial payment, received after the request is reviewed and accepted. Once accepted, the researcher could receive payments every quarter the Zero-Day exploit is still alive. The specific values of the initial payment and quarterly bonus will be included in an offer presented to the researcher, following the review of their work. Additionally, Exodus also offers payment in the form of Bitcoin for Zero-Day research.”
Apple’s bug bounty was received with applause at Black Hat and Apple was generally considered the last holdout among major technology vendors to reward researchers for disclosing security flaws.
“This is somewhat of a no-brainer for Apple—in terms of increasing the security of their devices and OSes,” said Synack director of research Patrick Wardle, a longtime Mac OS X bug hunter who has disclosed numerous issue to Apple. “Apple has a solid security team comprised of intelligent individuals. However, it’s unlikely that any company’s security team can provide the same coverage as a well-managed bug-bounty program. Generally speaking, having more ‘eyes’ looking for bugs is a good thing.”
Apple has limited its bounty program to a couple dozen researchers, Krstic said at Black Hat. Despite the program being invitation-only at first, Krstic said that researchers who submit bugs in any of the classes in scope could also be considered.
“The scope is pretty tight, only extending to iOS and iCloud vulnerabilities. It would make sense for Apple to extend it to other properties — they likely will eventually, assuming the current program is successful,” said researcher Randy Westergren Jr., who has privately disclosed security issues to Adobe, Verizon, United Airlines and Marriott hotels among others. “I think Apple joining the bug bounty club was inevitable, especially since most of its serious competitors have been operating theirs for some time. It continues to send the right message to other top tier organizations that are holding out: bug bounties are a step in the right direction.”
Apple would not say what the tipping point was for it to move forward with a bug bounty. But iOS in particular has been in the headlines for months starting with the FBI’s very public fight against Apple for help in unlocking the San Bernardino terrorist’s iPhone earlier this year. Needless to say, iOS bugs are at the top of most hitlists beyond Exodus Intelligence’s.
“As Apple often does, it approaches things in a calculated, somewhat cautious manner. Due to recent events (FBI vs. Apple), iOS is somewhat on the forefront of security – both in the press and on people’s minds,” Wardle said. “Also, there are companies who are willing to pay a ton of money for iOS bugs. Both these things, make it quite reasonable for Apple to begin their bug bounty program with iOS and iCloud.”
The priorities of the rewards show that Apple doesn't care too much about the bugs real attackers care about most. https://t.co/KpdVZN7aOJ
— thaddeus e. grugq thegrugq@infosec.exchange (@thegrugq) August 5, 2016
https://twitter.com/addelindh/status/761490936744517632
https://twitter.com/JZdziarski/status/748651601968136192
While some were dismayed by the payouts announced, others such as Westergren and Wardle said the payouts were fair and reasonable.
“There will always be researchers that complain about payouts, but we’ve come a long way from the days of threats of legal action,” Westergren said.
Wardle added: “I think some are reasonable. Paying $25,000 for a sandbox escape is decent. However, if the FBI is supposedly paying over $1M for certain iOS bugs—that may be (more) appealing to some. Of course if somebody is reporting bugs to Apple currently, for free—the payouts Apple are providing are quite generous!”