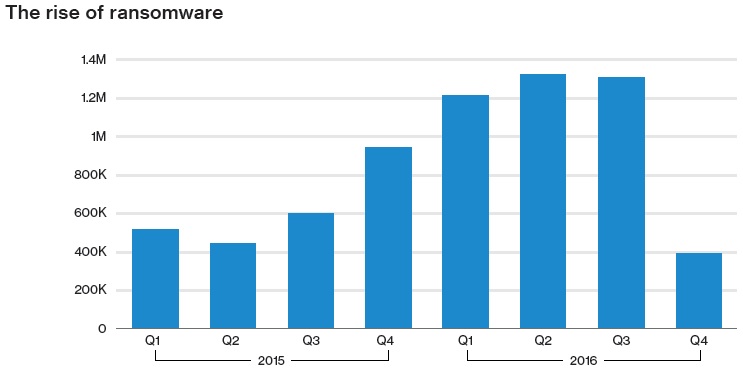
Ransomware dominated malware-related data breaches investigated by Verizon last year, appearing in 71 percent of cases, according to the annual Verizon Data Breach Investigations Report (DBIR) released Thursday.
Compared to last year’s DBIR report, ransomware attacks are up 50 percent. Still, Verizon suspects the true number of ransomware attacks and victims is likely going under reported.
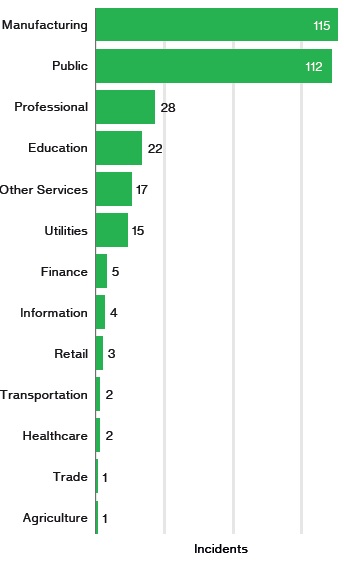
The DBIR, an analysis of more than 40,000 incidents (including 1,935 breaches) investigated by Verizon, shows that cybercriminals targeted manufacturing, the public sector and education the most, but Verizon senior network engineer Dave Hylender said the healthcare industry was hit the hardest with ransomware.
“Organized criminal groups continue to utilize ransomware to extort money from their victims, and since a data disclosure in these incidents is often not confirmed, they are not reflected in statistical data,” Verizon wrote.
Last year, ransomware attacks against healthcare organizations dominated headlines such a Locky ransomware attack against the hospital chain MedStar and Samsam ransomware attacks that crippled two California hospitals. Last year also saw the emergence of new types of ransomware and ransomware business models, with the DBIR citing Petya and Mischa specifically.
“Ransomware has evolved over the past year,” Hylender said. “We are seeing new strains with new attributes.” Instead of immediately infecting and encrypting data, criminals are now taking their time infiltrate systems and targeting high-value data with ransomware, he said.
“Ransomware gangs are using unforeseen and unusual command lines and are using new packaging techniques for their malware so they can evade detection,” Hylender said. Last year there was no shortage of unique ransomware from those that used fileless attack techniques, to campaigns that coupled elaborate phishing attacks with complex malicious Word macros.
 The 2017 DBIR also singles out cyberespionage and APTs as a prevalent threat. Verizon said 21 percent of breaches last year were tied to organized nation-state groups that dominated headlines such as Fancy Bear, Equation Group and Turla.
The 2017 DBIR also singles out cyberespionage and APTs as a prevalent threat. Verizon said 21 percent of breaches last year were tied to organized nation-state groups that dominated headlines such as Fancy Bear, Equation Group and Turla.
State-affiliated actors were responsible for a quarter of recorded phishing attacks, up from nine percent last year. “Targeted phishing campaigns continue to be the tip of the spear for espionage-related breaches,” Verizon wrote. Hardest sectors hit by cyberespionage were manufacturing (representing 38 percent of attacks investigated by Verizon), public (34 percent), professional (9 percent) and education (7 percent), according to the DBIR.
The interesting change in the DBIR is the rise of academia as a target of these attacks, Hylender said. Colleges are centers of innovation and are building technologies that would certainly be targeted by state affiliated groups, he said.
“Criminals are realizing that intellectual property and trade secrets are being held by institutions of higher learning. And, state actors are realizing it’s easier to break into a university system and steal the R&D there than break into a government system or a well-developed and well-protected manufacturer’s system,” Hylender said.
In the report, Verizon offers several words of advice for business. One, don’t go out of your way to give hackers a reason to attack you. “Stay off the radar of any potential hacker,” Verizon said. It also suggests keeping an ear to the ground when it comes to understanding the type of defenses needed based on reliable threat intelligence. And then, there is the obvious – secure your environment. “Implement a timely and effective patch management program; conduct regular penetration-testing activities,” it suggests.
Verizon also recommends implementing two-factor authentication and offering security awareness training for staffs.
“People are still not using two-factor authentication and hackers are still using brute force passwords attacks. There are all sorts of things we tell people to do to be more secure. Nevertheless, people continue to practice poor security hygiene. Will things change next year? Why would criminals morph and change their tactics if what they are doing today is easy, successful and making them a great deal of money.”