Teslacrypt, the fairly new strain of ransomware that’s been targeting gamers, is continuing to make the rounds online. Researchers have spotted exploit kits like Sweet Orange and Angler dropping the malware on machines over the past few months. This week, Brad Duncan, a handler over at the SANS InfoSec Community Forums, discovered the Nuclear Exploit Kit dropping a variant of the malware.
Duncan, who discussed his findings in a post on the site Wednesday, points out that as a whole the Nuclear Kit seen distributing the malware hasn’t changed much since SANS last looked into it, but this time he noticed the kit doling out a Flash exploit that targeted a dated version (13.0.0.182) of Flash Player, then dropped the obfuscated malware payload.
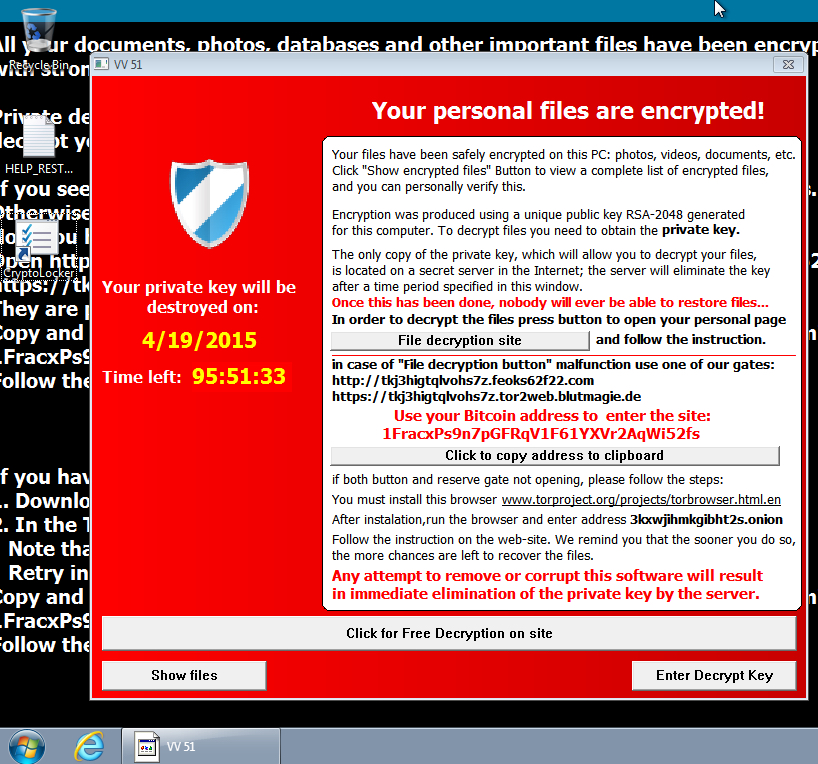
Once a machine is infected, like most ransomware, Teslacrypt warns users their personal files have been encrypted. After clicking through to a file decryption site, they can allegedly decrypt the files for 2.5 BTC, or $550 USD.
According to Duncan it doesn’t look like this particular strain of Teslacrypt has duped anyone into paying yet. When checked, the blockchain says there have been zero transactions thus far, but ransomware as a whole has had a very successful run of late.
The ransomware, which some have called a variant of CryptoLocker, first surfaced earlier this year when it was spotted targeting video gaming files like images, documents, videos and app databases. Apparently 50 different types of files associated with popular games like MineCraft, Call of Duty, and World of Warcraft were some of the first to be targeted, according to a post at Bleeping Computer back in February.
Ransomware #Teslacrypt Still Targeting Gamers via @Threatpost
Tweet
Although it wasn’t familiar with the malware’s name at the time, Bromium Labs did some further research on the malware in March and noted a version they were tracking was being deployed from a WordPress site that had been hijacked by the Angler EK via a Flash vulnerability.
“Encrypting all these games demonstrates the evolution of crypto-ransomware as cybercriminals target new niches,” Vidim Kotov, a researcher with Bromium wrote at the time.
Duncan notes that this strain of Teslacrypt, which is slightly different than those that came before it, has the same end result.
“Those files may be lost if you don’t have a backup. Even if you pay the ransom, there’s no guarantee you’ll receive the decryption key,” Duncan writes, “As always your best defense is regularly backing up your data.”