 A new variety of spyware has been targeting users in Iran, Israel and the Middle East for the last eight months according to joint research from Israeli security software firm Seculert and Kaspersky Lab. The new malware is using a variety of odd techniques and misdirection to entice users to install it, and researchers say it is targeting a specific group of potentially high-value targets.
A new variety of spyware has been targeting users in Iran, Israel and the Middle East for the last eight months according to joint research from Israeli security software firm Seculert and Kaspersky Lab. The new malware is using a variety of odd techniques and misdirection to entice users to install it, and researchers say it is targeting a specific group of potentially high-value targets.
The Madi campaign takes aim at “Middle Eastern critical infrastructure engineering firms, government agencies, financial houses and academia,” and can be programmed to monitor computer screens, record audio and steal screenshots, keystrokes, documents and e-mail correspondence, according to a Securelist post early Tuesday. The malware’s name, Madi or Mahdi, refers to files used by the spyware and according to Islam, is a Shiite reference to the prophesied redeemer that rules before the Day of Judgment.
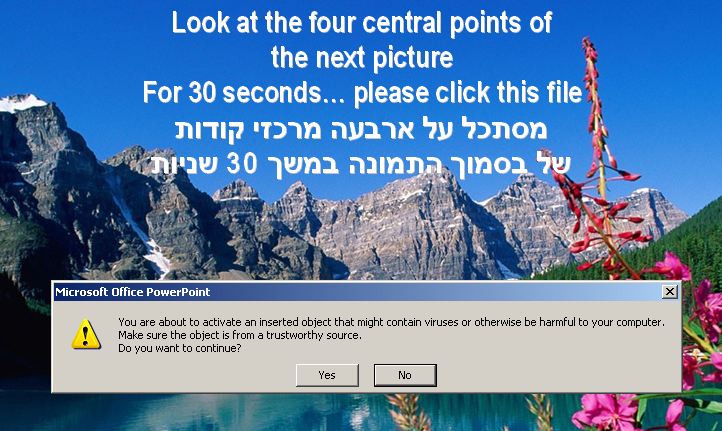
The campaign was first detected in February when Seculert encountered a spear phishing attack that enclosed a malicious Microsoft Word document, “Mahdi.txt.” If clicked, the document, a copy of a 2011 Daily Beast article on how Israel was planning on using cyber crime to attack Iran, drops a series of backdoors and bizarre PowerPoint slide shows.
Through an assortment of “calm, religious themed, serene wilderness, and tropical images,” the slideshows aim to confuse users and trick them into running a payload similar to the one seen below:
According to Seculert’s CEO Aviv Raff, his company contacted Kaspersky Lab about Madi last month following the firm’s Flame discovery. While both campaigns targeted critical infrastructure, an investigation into possible connections between Flame and Madi failed to turn up any solid connections.
However, in sinkholing the malware and using Seculert’s analytics technology, the two discovered Madi communicated with four separate command and control (C&C) servers for eight months and affected 800 victims. Variants of the malware communicated with servers in Tehran at one point and most recently Canada, according to Seculert’s research.
A post on Seculert’s blog insists it still isn’t clear whether Mahdi falls into the category of a ‘state-sponsored attack’.
For more on Madi, head to Seculert’s blog and Securelist’s.









