The number of phishing attacks declined in the first half of 2010, but a report from the Anti Phishing Working Group warns that might not be such a good thing.
The group released its Global Phishing Survey on Monday covering the first six months of 2010. Overall, the survey reported a steep decline in the number of phishing sites – 48,244. That’s a 38 percent decline from the preceding six months and the lowest number since the first half of 2008. Similarly, the number of domain names hosting attacks is down, albeit slightly, from the first half of 2009, despite an overall growth in the number of Internet domains.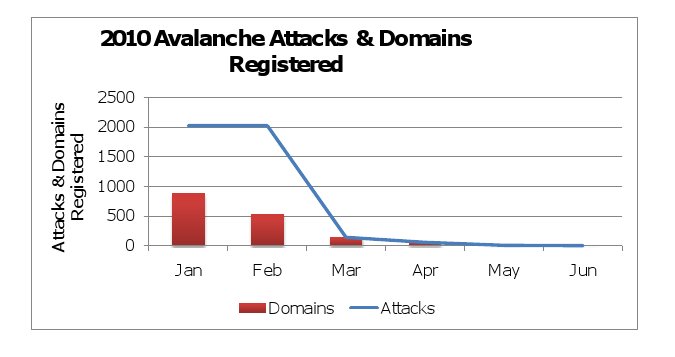
That’s good news, right? Not necessarily, according to APWG. The cross industry group says a big reason for the decline is a shift by The Avalanche phishing gang from phishing scams to distribution of the Zeus Trojan, rather than actions by large tech vendors and infrastructure owners, such as Google’s recently announced Phishing Alert Service.
Avalanche was a source of two thirds of global phishing activity in the first half of 2009, and phishing activity from the group plunged in the fourth quarter of 2009 – from 26,411 phishing attacks launched from 924 domains in October, 2009 to just 4 attacks from 4 domains in June, 2010.
While the gang’s decision to stop using its considerable global network infrastructure of hosted Web sites and infected computers for phishing has translated into a drop in attacks, the shift from credential theft to identity theft and bank fraud – Zeus’s two main activities – may make the Net an even more dangerous place. A recent report from Kroll Consulting found that theft of information was a more important problem for enterprises than physical theft.
Why the shift to crimeware from phishing? Profit, according to APWG.
“It is simply more profitable to control someone’s computer remotely and move large amounts of money than to simply steal victims’ online banking credentials,” the report said.
Among the report’s other findings:
- Phishing campaigns lasted longer in the first half of 2010 – staying online an average of 58 hours 10 minutes, compared with just 39 minutes 11 seconds in the same period a year earlier. APWG attributes the increase – again- to the disappearance of Avalanche phishing attacks, which had prompted a quick response from ISPs, hosting services and domain operators.
- Compromised domains – rather than domains established by the phishers – were used for the vast majority of phishing attacks: 23,872 of 28,647 – or 83%. And, despite the association of phishing attacks with brand hijacking and the use of domain names that can confuse victims, just 5% of the domains APWG says were used in phishing attacks contained a relevant brand name or variation of a brand name. Most domains registered by phishing crews and used in attacks made no effort to confuse victims.
Read the full APWG Global Phishing Survey: Trends and Domain Name Use in 1H2010 at the group’s Web site.









