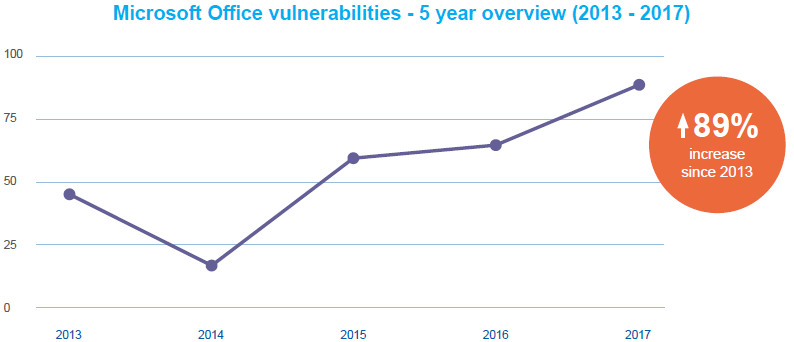
The number of reported vulnerabilities in Microsoft software has mounted from 325 in 2013 to 685 last year, a rise of 111 percent, according to new research.
Moreover, there has also been a 54 percent increase in critical Microsoft vulnerabilities since 2016, researchers at Avecto said in their report, which is based on data from Microsoft’s Security Update Guide.
The number of vulnerabilities in Windows 10 jumped 64 percent last year, and critical vulnerabilities in Microsoft browsers rose 46 percent since 2013. Some of this can be attributed to the fact that Windows 10 and Microsoft’s Edge browser are both fairly new products and therefore subject to ongoing refinement, along with extra scrutiny from security researchers.
Last year, Microsoft reported 587 vulnerabilities spanning Windows Vista, Windows 7, Windows RT, Windows 8/8.1 and Windows 10, according to the report. “This is a record high, coming in 232 vulnerabilities more than last year’s report, and marking a 132% increase on the numbers from 5 years ago,” Avecto said.
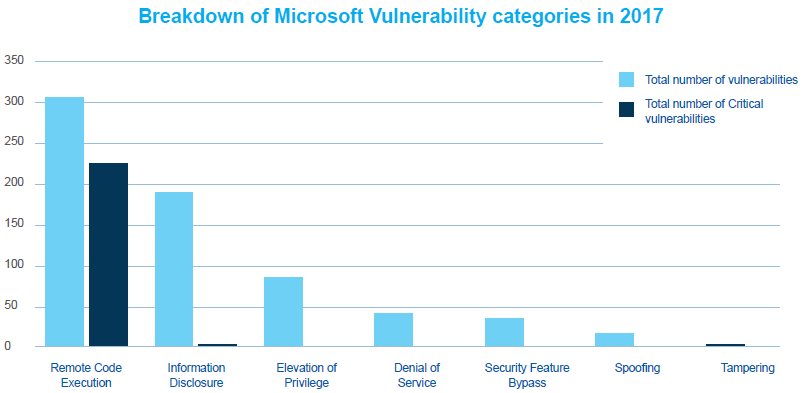
Remote code execution vulnerabilities took up the biggest chunk of the 685 reported overall in 2017, at 301. RCE vulnerabilities in Microsoft software have risen 58 percent since 2013, according to Avecto’s report.
The remaining vulnerabilities were categorized–in order of their incidence–as information disclosure, elevation of privilege, denial of service, security feature bypass, spoofing and tampering. Avecto’s research didn’t provide percentages for those categories.
Avecto develops user privilege management software. To that end, its report repeatedly stresses the importance of removing admin rights from end users.
Avecto contends that taking away admin rights would mitigate 80 percent of the critical vulnerabilities reported in 2017. The report also says that 134 of the 140 critical vulnerabilities found in Edge last year could have been mitigated by the removal of user admin rights.
“Some organizations believe that user account control (UAC) will protect them, but attackers know of many methods to silently bypass UAC popups,” said Jake Williams, president of Rendition Infosec, in the report. “Even Microsoft says that UAC is not a security control. By removing administrative rights from your users, you ensure that the attacker cannot take full control of a machine even if a vulnerability is exploited.”
“Ideally all machines would be patched immediately and users wouldn’t have local admin on their machines,” Williams added. “But we live in the real world and often organizations are dealing with years of technical debt and poor architecture decisions.”