Researchers are highlighting the insecure nature of Internet of Things devices in a report released Tuesday alleging a bevy of popular consumer connected devices sold at major retailers such as Walmart and Best Buy are riddled with security holes and privacy issues.
In analyzing 12 different IoT devices, researchers with Dark Cubed and Pepper IoT reported security failures that ranged from a lack of encryption for data and missing encryption certificate validations.
Dark Cubed told Threatpost that it did not reach out to the device manufacturers listed in the report before publication. Threatpost reached out separately to the makers of these IoT devices for comment and has not yet heard back.
“IoT is a fast-growing market, however what we found is not just that these companies did not catch all of the security flaws, rather we found that the manufacturers and retailers are likely not even considering security at all,” researchers said in their report, “The State of IoT Security,” published Tuesday. “This has to change today if we have any hope of being secure tomorrow.”
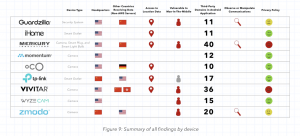
The researchers examined IoT devices, including smart cameras, plugs and security systems, from manufacturers: iHome, Merkury, Momentum, Oco, Practecol, TP-Link, Vivitar, Wyze and Zmodo. The devices were purchased from popular retailers Walmart, Best Buy, Amazon, and Micro Center.
Readers may want to take the report with a grain of salt. The Dark Cubed and Pepper IoT includes an unusually broad disclaimer:
“This entire report was written and designed by the technical team at Dark Cubed. This report was not composed or graphically designed by a marketing or advertising firm. As such, we accept full responsibility for any typos or errors. If any of our statements or findings are found to be in error, we will swiftly correct or retract such statements after confirming the error and will be certain to publicly accept responsibility for any such errors.”
Researchers said they specifically analyzed devices’ privacy policy to understand where data is being shared; monitored traffic and communication patterns; collected full packet data for manual reviews of communications; and performed analyses of devices’ complementary Android applications.
Security Issues
Researchers allege that several of the devices they looked at were designed on platforms that either do not fully utilize encryption for the transmission of information or would allow anyone to bypass the encryption due to poor implementation.
For instance, researchers assert Merkury devices that they reviewed did not encrypt traffic on the network, giving researchers full visibility to the names of the queues used by each device, as well as the username and password necessary to access those queues.
Connected devices from Guardzilla and Zmodo did not confirm whether encryption certifications for encrypted communications were valid. Guardzilla devices contained default hardcoded passwords, according to the researchers.
“We are certainly concerned about the devices themselves, however we strongly suspect that the security issues we found are representative of the fact that these companies have not considered security important enough to even conduct a single security review of these devices,” researchers wrote.
These types of design flaws have dangerous implications. In fact, of the nine IoT manufacturers analyzed, six of them allegedly featured devices that were vulnerable to man-in-the-middle attacks, where data transmitted between two parties can be intercepted and manipulated.
Not all products were rendered insecure. In fact, researchers stressed that the iHome Smart Outlet, the Momentum Axel Camera, and the TP-Link Kasa Smart Outlet were all “well developed, secure, and straighforward devices with no identified communications of concern.”
Privacy Flaws
Data privacy collected and transmitted between the IoT devices and their complementary applications was another cause for concern highlighted by researchers.
For instance, though the Merkury lightbulb does very little – this IoT device only turns on and off the lights. However, its complementary app itself reportedly requires “a significant number of permissions such as knowing your location at all times, recording audio, and reading and writing to external storage on your phone,” researchers said.
The Merkury app also features hard coded links to 40 third-party websites within the application code to include both U.S. and China-based entities such as Alibaba, Taobao, QQ, Facebook, Twitter, and Weibo – presumably for advertising purposes, researchers reported.
“Many of the applications required or at least requested location permissions in order to use the app,” Vince Crisler, CEO of Dark Cubed, told Threatpost. “For example, the Android application with the Merkury lightbulb requires location permissions to even function. And the application was observed sending data to servers in China, but we aren’t clear on what information was being sent due to encryption.”
In the case of the home security cameras made by Zmodo Camera, researchers were able to observe communication made to and from the camera including images, video, birthdates, e-mail addresses and phone numbers. While examining smart outlets and lightbulbs made by Merkury, researchers were able to observe all actions taken to turn on and off devices.
Privacy policy guides were another aspect: According to researchers, companies such as Merkury and Vivitar had “overly broad and non-restrictive” privacy policies.
Pepper IoT researchers stressed that these issues are systemic and cannot be fixed merely by patching.
“While companies can undoubtedly patch their devices to fix many of the issues we found, the problem is much more severe: many product companies do not care about security and only act when outsiders find issues,” they said. “This reactive approach does not work, security must be proactive.”
The Future of IoT
While issues have persisted for years, IoT security were highlighted when the 2016 Mirai botnet mounted a distributed denial of service (DDoS) attack through 300,000 vulnerable IoT devices. More recently, potential attack vectors is proliferating. For instance, Google Home devices, smart plugs and smart padlocks have all recently been in the spotlight for security flaws.
Researchers point out IoT security issues are only getting worse – not better. In the first half of 2018, researchers at Kaspersky Lab said they picked up three times as many malware samples targeting IoT devices as they did for the entirety of 2017.
An internet of things bill that would mandate unique passwords for connected devices was approved in September by the California state legislature. The bill (SB-327) requires “reasonable security feature or features that are appropriate to the nature and function of the device” – however, researchers say more needs to be done to regulate and control IoT security.
Interested in learning more about privacy and data breach trends? Watch the free, on-demand Threatpost webinar, as editor Tom Spring examines the data breach epidemic with the help of noted breach hunter and cybersecurity expert Chris Vickery. Vickery shares how companies can identify their own insecure data, remediate against a data breach and offers tips on protecting data against future attacks.