 Researchers have made a huge dent in a major variant of the Pushdo botnet, virtually crippling the network by working with hosting providers to take down about two thirds of the command-and-control servers involved in the botnet.
Researchers have made a huge dent in a major variant of the Pushdo botnet, virtually crippling the network by working with hosting providers to take down about two thirds of the command-and-control servers involved in the botnet.
Pushdo for years has been one of the major producers of spam and other malicious activity, and researchers have been monitoring the botnet and looking for ways to do some damage to it since at least 2007. Now, researchers at Last Line of Defense, a security intelligence firm, have made some serious progress in crushing the botnet’s spam operations.
After doing an analysis of Pushdo’s command-and-control infrastructure, the researchers identified about 30 servers that were serving as C&C machines for a variant of the botnet. Working with the hosting providers who maintained the servers in question, the LLOD researchers were able to get 20 of the C&C servers taken offline, the company said.
“We identified a total of 30 servers used as part of the
Pushdo/Cutwail infrastructure, located at eight different hosting
providers all over the world. The information about the activity was
extracted from Anubis reports,
which contain details about the system and network activities,
including a pcap file that contains the network traffic we observed
while doing the analysis. We contacted all hosting providers and worked
with them on taking down the machines, which lead to the take-down of almost 20 servers.
Unfortunately, not all providers were responsive and thus several
Command & Control servers are still online at this point,” researcher Thorsten Holz wrote.
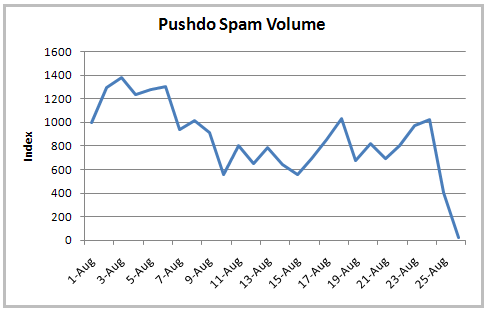
The result is that the volume of spam that Pushdo is producing has dropped to nearly zero.
At the time of Pushdo’s appearance several years ago, researchers found evidence that Pushdo’s creators had gone to some lengths to avoid detection and prevent removal of the malware associated withthe botnet. The creators had changed the way that Pushdo made HTTP requests, creating overly long GET requests to make them less identifiable.
“The length of the request will likely change between different service
pack levels of Windows. IDS/IPS signatures can still be written around
such a request, taking advantage of the fact that no other HTTP headers
are sent as one characteristic to key in on. However, even with this
approach, false positives may still occur,” SecureWorks researcher Joe Stewart wrote in an analysis in 2007. “Clearly the author of Pushdo is intent on evading detection for as long
as possible, in order to have the maximum amount of time to seed Cutwail
spambots into the wild.”
One of the interesting aspects of the original version of Pushdo is that its creator was using it not just to send spam, but also to spread other pieces of malware. This has become a more common business model in recent years as bot herders have looked for new ways to make money from the millions of compromised PCs under their control.
Spam volume graph from M86 Security Labs.









