 Phishing gangs have been getting bolder of late, and there’s no clearer evidence than the cache of phishing data that researchers at Sunbelt found on a site owned by the Paraguayan government.The researchers discovered that a site belonging to the federal government in Paraguay is currently hosting a fairly large drop of phishing information related to attacks on banks, insurance companies and other targets in the U.K.The targets include some of the bigger companies in the U.K. business world: Barclays, Lloyds, Halifax and others.
Phishing gangs have been getting bolder of late, and there’s no clearer evidence than the cache of phishing data that researchers at Sunbelt found on a site owned by the Paraguayan government.The researchers discovered that a site belonging to the federal government in Paraguay is currently hosting a fairly large drop of phishing information related to attacks on banks, insurance companies and other targets in the U.K.The targets include some of the bigger companies in the U.K. business world: Barclays, Lloyds, Halifax and others.
[block:block=47]
This hidden cache, while sitting on a relatively high-profile server, is not much different than drops that have been found on servers all over the world. In many cases, researchers will sit and watch the servers in hopes of learning something about the gang behind the phish. In this case, the Sunbelt researchers have notified the site owners.
No less than fourteen different banking / financial services phishes
including Barclays, Abbey, Northern Rock, Halifax and Lloyds TSB.
Clearly, someone is desperate to get their hands on as many UK banking
credentials as possible. These phishes are all online at the moment
although some appear to be flagged in browsers such as Firefox. We’ve
contacted the hosts and hopefully all of the above will be offline
shortly.
The server on which the data is being hosted belongs to the Central Department of the federal government in Paraguay. But that doesn’t seem like much of a bother or a challenge to the gang behind the attack. It’s just another server on which to hide their wares; one’s as good as another. Here’s a look at the site’s index:
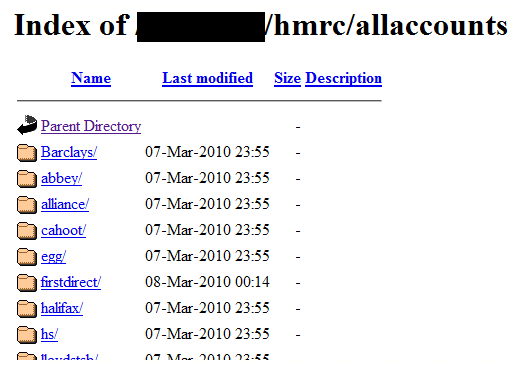
Phishing gangs long ago figured out that they were better off storing stolen credentials, malware and other interesting files on someone else’s servers than on their own. If the cache is discovered, as this one was, then the attackers simply find another compromised server to use as a hiding place and move on.









