 Spammers, it turns out, aren’t like everyone else: they have fewer friends. That, according to new research by Microsoft scientists who have developed a new method of distinguishing attacker-created spam email accounts from legitimate ones. The new finding, from researchers Yinglian Xie and Fang Yu of Microsoft is described as Social Graphs for Online Service Security. The two are using studies of legitimate and malicious social networks to spot bogus email accounts that are used to push spam, malware, and otherwise malicious links.
Spammers, it turns out, aren’t like everyone else: they have fewer friends. That, according to new research by Microsoft scientists who have developed a new method of distinguishing attacker-created spam email accounts from legitimate ones. The new finding, from researchers Yinglian Xie and Fang Yu of Microsoft is described as Social Graphs for Online Service Security. The two are using studies of legitimate and malicious social networks to spot bogus email accounts that are used to push spam, malware, and otherwise malicious links.
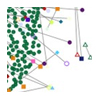
The researchers are analyzing natural social connections between users on the Web that are difficult for attackers or botnets to replicate. Spotting a spammer isn’t hard, they say, when you look at his or her patterns of communication.
“If you look at individual malicious-user-created accounts,” Xie tells Rob Knies in a Microsoft Research blog post, “it can be very difficult to tell them from legitimate user accounts. One thing we want to look at is whether we have a way of looking across a large number of users, looking at their connectivity among each other, to be able to differentiate the legitimate user community from the attacker part.
“The intuition here is very simple,” she continues, “if we define connectivity as mutual email exchange, a normal user will talk to other people—send email and receive email. But attackers will mostly send malicious content. They do not receive messages back from legitimate users. Essentially, all the legitimate users are going to be connected in some way into communities. Attackers are more isolated users on the connectivity graph.”
The dots on the graph represent assigned or inferred IP addresses, which have been mined from Microsoft’s Hotmail servers.
In studying these graphs, Xie and Yu found legitimate users are enmeshed in the graph, establishing dynamic and multi-directional relationships of sending and receiving messages. In contrast, malicious user lurk on the periphery and only really send unidirectional messages, to the center of the graph.
Using patterns of communications to spot spammers is nothing new. Existing online reputation systems also look at the pattern of outbound messages from accounts to spot malicious users.
In recent months, Microsoft has scored a number of victories in its efforts to stem spam. Among other things, the company helped take down the Coreflood and Rustock botnets respectively. The company continues a search for their operators.










