 For five years, it hid in the weeds of networks used by Eastern European diplomats, government employees and scientific research organizations, stealing data and infecting more machines in an espionage campaign rivaling Flame and others of its ilk. The campaign, called Rocra or Red October by researchers at Kaspersky Lab, focused not only on workstations, but mobile devices and networking gear to gain a foothold inside strategic organizations. Once inside, attackers pivoted internally and stole everything from files on desktops, smartphones and FTP servers, to email databases using exploits developed in China and Russian malware, Kaspersky researchers said.
For five years, it hid in the weeds of networks used by Eastern European diplomats, government employees and scientific research organizations, stealing data and infecting more machines in an espionage campaign rivaling Flame and others of its ilk. The campaign, called Rocra or Red October by researchers at Kaspersky Lab, focused not only on workstations, but mobile devices and networking gear to gain a foothold inside strategic organizations. Once inside, attackers pivoted internally and stole everything from files on desktops, smartphones and FTP servers, to email databases using exploits developed in China and Russian malware, Kaspersky researchers said.
While Kaspersky would not go so far as to call it a nation-state campaign, the resources behind the attackers and the targets they chose—which also included oil and gas companies, aerospace, nuclear research, and trade and commerce organizations—would indicate an interest in a particular type of information.
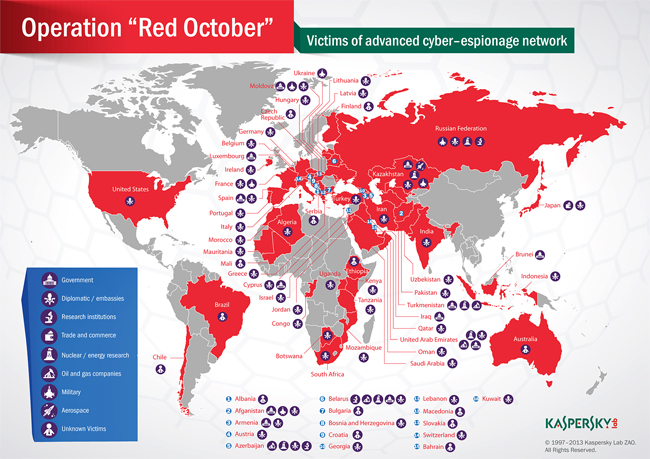
Most of the victims were specific organizations in Eastern Europe, former USSR nations and countries in Central Asia. Some attacks were also noticed in Western Europe and North America, Kaspersky said.
“The campaign is currently still active with data being sent to multiple command-and-control servers through an infrastructure which rivals the complexity of the Flame malware,” Kaspersky said in a report released today.
Kaspersky said it was alerted of the Rocra attacks by a partner last October when it began its analysis of the campaign. Several hundred infections worldwide have been counted. Three exploits have been used in the attack, all of which Kaspersky said were developed in China; the malware modules dropped in the attacks were created by Russian-speaking operatives, Kaspersky concluded.
“Currently, there is no evidence linking this with a nation-state sponsored attack. The information stolen by the attackers is obviously of the highest level and includes geopolitical data which can be used by nation states,” the report said. “Such information could be traded in the underground and sold to the highest bidder, which can be of course, anywhere.”
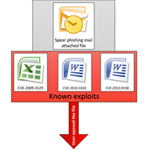
Like most of these APT-style targeted attacks, this one begins with a spear phishing message; one example provided was an announcement of a diplomatic car for sale.The email messages contain one of three attachments, each a different exploit of an existing vulnerability. One targets CVE-2009-3120 using a malicious Microsoft Excel document, while the other two are Word docs exploiting CVE-2010-3333 or CVE-2012-0158. These exploits were used in previous attacks against Tibetan activists and military and energy targets in Asia; for Rocra, the attackers not only reused the exploits, but replaced the payload with their own malware.
The documents are tailored for specific victims and the malware modules have specific victim ID numbers, Kaspersky said. Rocra operates on a personal level with the victim; the level of interaction is high and driven by the victim’s system configuration, the types of documents on their machine, software installed, native language and more.
Once the victim opens the malicious document, a Trojan is dropped on the machine which drops a module that scans the local network for other hosts vulnerable to MS08-067, the same vulnerability exploited by the Conficker worm, Kaspersky said. It also looks to access other hosts using credentials from its own password database. Another module tries to infect remote hosts on the same network. Kaspersky said the malware authors have Russian-speaking origins, and researchers had not seen the malicious executables before; one, for example, would change the default system codepage to 1251, which is required to render Cyrillic fonts, Kaspersky’s report said.
The campaign targets not only Office documents, email and a long list of document types including the acid* extension, which Kaspersky said refers to the classified Acid Cryptofiler software used by the European Union and NATO.
“The main purpose of the operation appears to be the gathering of classified information and geopolitical intelligence, although it seems that the information gathering scope is quite wide,” the report said. “During the past five years, the attackers collected information from hundreds of high profile victims although it’s unknown how the information was used. It is possible that the information was sold on the black market, or used directly.”
The command and control infrastructure behind this campaign is made up of 60 domains and a number of server host locations in Russia and Germany, most of which act as proxies in order to hide the true C&C server. Kaspersky said it was able to sinkhole six of the domains and watch them over since Nov. 2. More than 55,000 connections were made to the sinkhole from close to 250 IP addresses. Most of those IP addresses were in Switzerland, Kazakstan, Greece and Belarus; there are victims in 39 countries.
Kaspersky said it has not found any connections between Rocra and Flame, yet did say the campaign was more sophisticated than the Aurora attacks on Google or Night Dragon; its researchers found more than 1,000 unique malware files among 30 different categories, including reconnaisance, credential harvesting, email and USB specific, propagation, mobile devices and data exfiltration.
Some of the modules are one-time tasks, while others must remain persistent. Examples of persistent tasks include: search and extract files from a USB drive; wait for a mobile phone to connect and if it’s an iPhone or Nokia, steal its contents, or if a Windows phone, install a mobile version of Rocra; record keystrokes and screenshots; and more. Examples of one-time tasks include: collection of system, network and software information; extract browsing history, saved passwords, Windows account hashes and Outlook account information; write and execute arbitrary code; scan for administrative credentials; scan for Cisco network devices; and more.
Massive amounts of data were lost, the researchers said.
“With Rocra, the attackers managed to stay in the game for over 5 years and evade detection of most antivirus products while continuing to exfiltrate what must be hundreds of Terabytes by now,” Kaspersky said.