Necurs botnet activity is spiking as scammers use the network to flood inboxes with promises of companionship, in part of a seasonal wave of Valentine’s Day-themed spam. Victims are encouraged to share revealing photos of themselves, which scammers later use as leverage in extortion shakedowns.
The IBM X-Force research team reported the uptick Monday and said campaigns began in mid-January and are being driven by 6 million zombie Necurs bots.
“The first quarter of the year typically plagues email recipients with tax season spam and romance scams that start arriving in January leading up to Valentine’s Day,” wrote Limor Kessem, Dirk Harz and Johannes Noll, the X-Force researchers who co-authored the research blog.
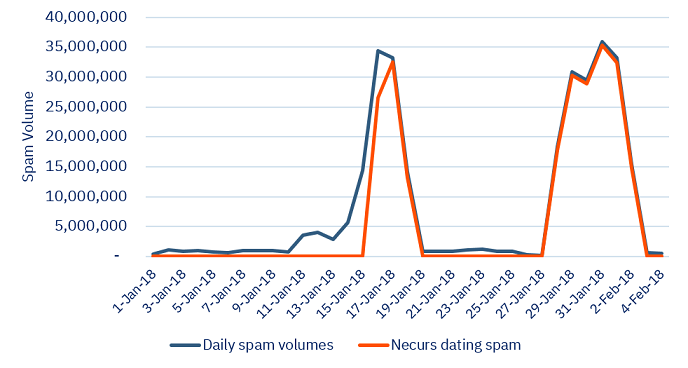
X-Force data shows two current campaign from Necurs totaling 230 million spam messages sent within 14 days. The first wave spiked between Jan. 16 through Jan. 18 and the second separate wave began Jan. 27 and lasted through Feb. 3. On average 30 million spam messages were sent each day.
“The current campaign delivers short email blurbs from supposed Russian women living in the U.S. While typical spam email is notorious for bad spelling and grammar, these samples are rather well-worded,” researchers said.
Necurs has proven a versatile tool for cybercriminals and has been typically used to spread banking trojans Dridex and TrickBot, and ransomware Locky, Scarab and Jaff, said researchers. “Necurs is not only about malware. Its operators dabble in distributing spam for other fraud endeavors as well, which brings to light this recent romance scam campaign,” researchers said.
In October, SANS Internet Storm Center reported the Necurs botnet was being used to spread Locky ransomware using the Office feature called Dynamic Data Exchange fields. Last month, Forcepoint researchers said a new Dridex banking trojan variant was being spread via Necurs.
According to X-Force, Necurs is likely the largest spam distributor active today.
Characteristics of this most recent campaign include simple spam messages that entice recipients to engage with the sender. “The threat actors behind this campaign will likely lure their victims to share revealing photos and extort them, ask for money to come visit or simply infect them with malware,” researchers said.
Spam messages are being sent from about 950,000 unique IP addresses, with 55 percent hosted in Vietnam and India.
“It’s worth noting that spammers constantly shuffle the resources they leverage and the originating IPs logged in one campaign are not likely to be used in the next one. This is how fraudsters avoid blacklists and blocking,” researchers note.