 There was lots of noise and distraction on the crowded Expo floor of the RSA Security Conference this year. After a grueling couple of years, vendors were back in force with big booths, big news and plenty of entertainment designed to attract visitor traffic. Wandering the floor, I saw – variously – magic tricks, a man walking on stilts, a whack-a-mole game, a man dressed in a full suit of armor and a 15 foot long racetrack that I would have killed for when I was 10.
There was lots of noise and distraction on the crowded Expo floor of the RSA Security Conference this year. After a grueling couple of years, vendors were back in force with big booths, big news and plenty of entertainment designed to attract visitor traffic. Wandering the floor, I saw – variously – magic tricks, a man walking on stilts, a whack-a-mole game, a man dressed in a full suit of armor and a 15 foot long racetrack that I would have killed for when I was 10.
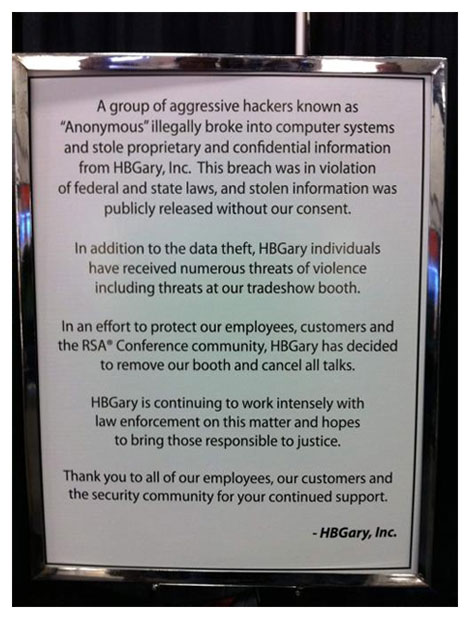
The most telling display, however, may have been the one in Booth 556, where malware forensics firm HBGary displayed a simple sign saying that it had decided to remove its booth and cancel scheduled talks by its executives. This, after the online mischief making group Anonymous broke into the computer systems of the HBGary Federal subsidiary and stole proprietary and confidential information. The HBGary sign stayed up for a couple days, got defaced by someone at the show and was later removed. When I swung by HBGary’s booth on Thursday, it was a forlorn and empty patch of brown carpet where a couple marketing types where holding an impromptu bull session.
It would be easy to say that the lesson of HBGary is that “anyone can get hacked.” After all, the company’s founder, Greg Hoglund is one of the smartest security folks around – hands down. He’s a recognized expert on malware and, literally, wrote the book on rootkit programs. HBGary Federal’s customers included the U.S. Department of Defense as well as spy agencies like the CIA and NSA.
Or maybe the lesson of HBGary is simply not to “kick the hornet’s nest,” so to speak: needlessly provoking groups like Anonymous who have shown themselves to be hungry for publicity and have little to lose in a confrontation. Maybe, the lesson is simply that, if you’re going to kick the hornet’s nest, as HBGary Federal CEO Aaron Barr was determined to, then at least to spend some time securing your Web- and e-mail infrastructure and following password security best practices before you commence said kicking.
But I think the real lesson of the hack – and of the revelations that followed it – is that the IT security industry, having finally gotten the attention of law makers, Pentagon generals and public policy establishment wonks in the Beltway, is now in mortal danger of losing its soul. We’ve convinced the world that the threat is real – omnipresent and omnipotent. But in our desire to combat it, we are becoming indistinguishable from the folks with the black hats.
Of course, none of this is intended to excuse the actions of Anonymous, who HBGary President Penny Leavy, in a conversation with Threatpost, rightly labeled “criminals” rather than politically motivated “hacktivists.” The attack on HBGary was an unsubtle, if effective, act of intimidation designed to send a message to Barr and other would be cyber sleuths: ‘stay away.’
We can see their actions for what they are, and sympathize deeply with Aaron Barr, Greg Hoglund and his wife (and HBGary President) Penny Leavy for the harm and embarrassment caused by the hackers from Anonymous, who published some 70,000 confidential company e-mails online for the world to see. Those included confidential company information, as well as personal exchanges between HBGary staff that were never intended for a public airing. Its easy to point the finger and chortle upon reading them, but how many of us (or the Anonymous members, themselves) could stand such scrutiny?
Its harder to explain away the substance of many other e-mail messages which have emerged in reporting by Ars Technica as well as others. They show a company executives like HBGary Federal CEO Aaron Barr mining social networks for data to “scare the s***” out of potential customers, in theory to win their business. While “scare ’em and snare ’em” may be business as usual in the IT security industry, other HBGary Federal skunk works projects clearly crossed a line: a proposal for a major U.S. bank, allegedly Bank of America, to launch offensive cyber attacks on the servers that host the whistle blower site Wikileaks. HBGary was part of a triumvirate of firms that also included Palantir Inc and Berico Technologies, that was working with the law firm of the U.S. Chamber of Commerce to develop plans to target progressive groups, labor unions and other left-leaning non profits who the Chamber opposed with a campaign of false information and entrapment. Other leaked e-mail messages reveal work with General Dynamics and a host of other firms to develop custom, stealth malware and collaborations with other firms selling offensive cyber capabilities including knowledge of previously undiscovered (“zero day”) vulnerabilities.
Look, there’s nothing wrong with private firms helping Uncle Sam to develop cyber offensive capabilities. In an age of sophisticated and wholesale cyber espionage by nation states opposed to the U.S., the U.S. government clearly needs to be able to fight fire with fire. Besides, everybody already knew that Greg Hoglund was writing rootkits for the DoD, so is it right to say we’re “shocked! shocked!” to read his e-mail and find out that what we all suspected was true? I don’t think so.
What’s more disturbing is the way that the folks at HBGary – mostly Aaron Barr, but others as well – came to view the infowar tactics they were pitching to the military and its contractors as applicable in the civilian context, as well. How effortlessly and seamlessly the focus on “advanced persistent threats” shifted from government backed hackers in China and Russia to encompass political foes like ThinkProgress or the columnist Glenn Greenwald. Anonymous may have committed crimes that demand punishment – but its up to the FBI to handle that, not “a large U.S. bank” or its attorneys.
The HBGary e-mails, I think, cast the shenanigans on the RSA Expo floor in a new and scarier light. What other companies, facing the kind of short term financial pressure that Barr and HBGary Federal felt might also cross the line – donning the gray hat, or the black one? What threat to all of our liberties does that kind of IT security firepower pose when its put at the behest of corporations, government agencies, stealth political groups or their operatives? Bruce Schneier – our industry’s Obi-Wan Kenobi – has warned about this very phenomena: the way the military’s ever expanding notion of “cyber war,” like the Bush era’s “War on Terror” does little to promote security, but a lot to promote inchoate fear. That inchoate fear then becomes a justification for futher infringement on our liberties.
“We reinforce the notion that we’re helpless — what person or organization can defend itself in a war? — and others need to protect us. We invite the military to take over security, and to ignore the limits on power that often get jettisoned during wartime,” Schneier observed. That kind of conflation is clear reading Barr’s e-mails where the line between sales oriented tactics and offensive actions blur. The security industry veterans I spoke with at this year’s show were as aghast at Barr’s trip far off reservation, but they also expressed a weary recognition that, in the security business, this is where things are headed.
What’s the alternative? Schneier notes that focusing on cyber crime as “crime” rather than “war” tends to avoid the problems with demagoguery. Focus on cyber crime and hacking in the same way as you focus on other types of crimes: as long term problems that must be managed within the “context of normal life,” rather than “wars” that pose an existential threat to those involved and must be won at all costs. The U.S. needs peacetime cyber-security “administered within the myriad structure of public and private security institutions we already have” rather than extra-judicial vigilantism and covert ops of the kind the HBGary e-mails reveal. Here’s hoping HBGary is the wake up call the industry needed to reverse course.









