A crimeware kit dubbed the Rubella Macro Builder is betting on a “dirty deeds done dirt cheap” approach to gain popularity in the criminal underground. The kit does two things: with a point-and-click builder functionality, it generates an initial malware payload for social-engineering spam campaigns; and it only costs $40 per month.
Rubella is not particularly high-achieving: It eschews the exploitation of vulnerabilities for social-engineering techniques; users use it to take the well-worn route of sending out mail with Microsoft Word or Excel email attachments (with the goal of getting victims to enable malicious macros). It’s not very aspirational either: Its humble intent involves generating fairly simple first-stage loader malware that threat actors can use for subsequent downloads and installations on targeted machines.
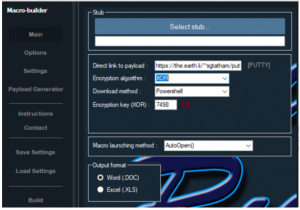
However, the price is right, and it’s got some attractive bells and whistles. A three-month license includes various encryption algorithm choices (XOR and Base64), download methods (PowerShell, Bitsadmin, Microsoft.XMLHTTP, MSXML2.XMLHTTP or a custom PowerShell payload), payload execution methods (executable, JavaScript, Visual Basic Script), and the ability to easily deploy social-engineering decoy themes.
“Despite being relatively new and unsophisticated, the kit has a clear appeal for cybercriminals: it’s cheap, fast and can defeat basic static antivirus detection,” said Flashpoint researchers, in a blog.
Cheap and easy: That phrase is music to criminals’ ears everywhere, and no less so in the cyberworld. And indeed it’s gaining traction: Flashpoint analysts determined that the criminal gangs behind the Panda and Gootkit banking malware each leveraged the Rubella first-stage loader as an initial attack vector in two recent but separate campaigns.
“It is likely that the gangs are customers of the actor offering Rubella on the underground,” the researchers said. “Specifically, the gangs behind the Panda malware distribution appear to have targeted customers through various social-media platforms, as well as an Australian financial institution through Panda’s web-inject functionality.”
The macro junk and substitution method appears to be relatively primitive, relying on basic string substitutions. Additionally, its copy/paste implementation of the Base64 algorithm is displayed in Visual Basic Script (VBS) code implementation. The code is obfuscated through general Chr ASCII values. But it lives squarely in the sweet spot for most financially motivated criminals, whose model relies on maximizing margins and volume. And the infection tactics, though arguably pedestrian, work.
“Microsoft Office macro-based malware appears to still be threat actors’ preferred method for obtaining initial access to compromised machines,” Flashpoint researchers said. “Such Microsoft Office-based loader malware works well as an initial decoy—disguising itself as a commonly exchanged Word or Excel document and impersonating normal Microsoft Office or Excel attachments—and is generally spread via email attacks. While relatively unsophisticated, the Rubella Macro Builder represents a moderate threat to various networks.”