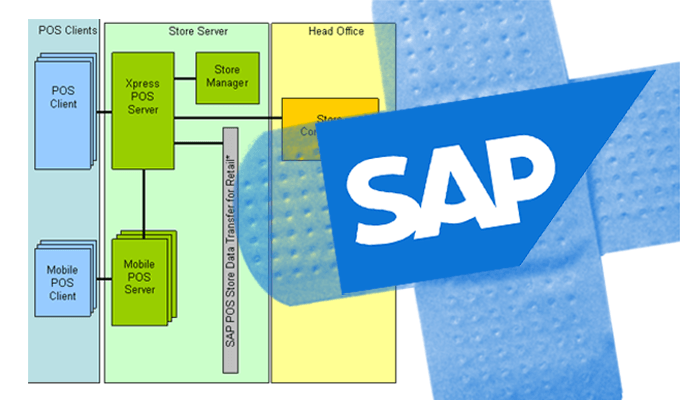
SAP fixed 23 vulnerabilities across roughly a dozen products on Tuesday, including a series of high-risk flaws that could allow an attacker to gain access to SAP POS, the company’s client/server point-of-sale (PoS) solution.
The issues in SAP POS, a series of missing authorization checks, could let an attacker access a service without authorization, according to ERPScan, a firm that specializes in SAP and Oracle security. The solution runs parallel to the company’s retail solution portfolio and is used by 80 percent of retailers in Forbes Global 2000, according to ERPScan. The vulnerabilities, which technically exist in the SAP solution’s Retail Xpress Server, could lead to information disclosure, privilege escalation and other attacks.
If exploited, an attacker could read, write, or delete files stored on the server, shut down the application, or monitor content from the receipt window of a targeted PoS system without authentication, researchers say.
Sensitive details of the vulnerabilities, which fetched the highest CVSS ranking of the bugs fixed Tuesday (8.1) weren’t disclosed but Dmitry Chastuhin and Vladimir Egorov, researchers with the Amsterdam-based firm, plan to dig into the bugs more in depth in a presentation at Hack in the Box Singapore in August.
The Retail XPress Server issue is one of four marked high priority by SAP. Two of those issues are updates to previously published security notes by the company. The remaining issue, a denial of service vulnerability, affects SAP Host Agent, a tool that allows users to monitor SAP instances, databases and operating systems.
According to Andres Blanco and Nahuel Sanchez, researchers with Onapsis who discovered the vulnerability, an attacker could remotely restart the agent without authorization via a malicious SOAP request.
‘If other scheduled jobs need these web services for regular processes, those jobs will subsequently fail. Depending on your business architecture, this could lead to more critical availability or performance issues on the system,” the two wrote Tuesday.
All versions of Host Agent, up to 7.21 PL24, are affected, according to Onapsis. Since the Agent is installed automatically with new SAP instances, the firm is cautioning that multiple SAP setups could be affected by the issue.
“Since the bug affects SAP Host Agent in any version, all Netweaver based applications and both HANA 1 and HANA 2 are affected,” Sebastian Bortnik, the firm’s head of research said Tuesday, “This increases the probability of being attacked and, consequently, the need for patching as quickly as possible.”
Today is SAP Notes Day. Working early in the morning, soon you will have @onapsis details for the most relevant vulns this month!
— Sebastian Bortnik (@onabortnik) July 11, 2017
The bulk of the remaining security notes issued by SAP address medium severity vulnerabilities in products such as SAP’s CRM admin console and its Access Controls product, including two cross-site scripting vulnerabilities, a code injection vulnerability and a pair of information disclosure vulnerabilities.
The patches make for a relatively quiet July and is the third month in a row a security update did not include a critical vulnerability for SAP administrators.
In April, the company pushed an updated patch for a critical two-year old code injection vulnerability in the TREX search engine. The issue in TREX, which figures into more than a dozen SAP products, was originally found back in 2015. Mathieu Geli, ERPScan’s head of threat intelligence, ultimately dubbed that patch incomplete when he found he could still get control on affected servers.
The company fixed a series of critical vulnerabilities in SAP HANA earlier this year, in March, that when chained together could have allowed for a full system compromise without authentication.