IntegraXor, a manufacturer of supervisory control and data acquisition (SCADA) equipment, announced last week that it would implement a bug bounty program offering points redeemable for company services to researchers that disclose security vulnerabilities in their IGX SCADA system.
In most bug bounty programs, vendors pay researchers for responsibly disclosing bugs in their products. Most vendors offer modest monetary payments, though Microsoft, who was famously late to the bug bounty game, recently stirred the pot a bit by announcing it would dole out six figures for particularly severe vulnerabilities. However, even Microsoft’s relatively large payouts pale in comparison to what a researcher stands to make on the lucrative private vulnerability sales marketplace.
SCADA machines are those that help regulate industrial processes. They play a central role in the maintenance of critical infrastructure systems.
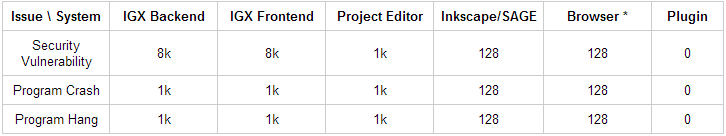
This program, however, is quite different. IntegraXor is not offering money for vulnerability reports. It has set up a system (see chart below) where researchers are rewarded points for disclosing vulnerabilities in the company’s IGX SCADA systems. Theoretically, more severe bugs warrant more points for the researcher that disclosed them. It’s a bit odd for the company to call their program “non-monetary” as the points can be exchanged for IntegraXor products and services and the company is also officially okay with researchers selling their points for whatever value they can attract on the open market. The company claims that their lowest payout is roughly the equivalent of $149 and their highest payout is just short of $4000.
IntegraXor says researchers will be disqualified for running vulnerability tests on live systems. In order to be eligible for reward, researchers must download their own testing environment, which is available on IntegraXor’s website. The company will only accept “closed disclosures.” Third party disclosures do not qualify.
Bug bounty programs are one of many sources for debate in the Internet security industry. The reality is that vendors are not willing to compete with governments with deep pockets that are capable of paying enormous sums of money for valuable exploits. Despite this, a recent study from the University of California Berkeley found that bug bounties are actually saving tech firms money in the end. Their research focuses mostly on the fact that it costs less to pay bounties than is it does to hire a full-time security researcher or two.
Lucky for the vendors, many researchers oppose selling exploits to anyone that would do anything other than fix the vulnerabilities. Because of this, many researchers are willing to forego large payments in order to guarantee that a certain bug gets fixed.
It’s one thing to pass on a stack of cash for doing something you perceive as ethically dubious. It’s a whole other thing to accept store credit for hard work.
Luigi Auriemma, a renowned SCADA researcher and bug hunter, expressed skepticism in an email conversation.
“Reporting vulnerabilities for some points that then you must try to resell on their forum is complex and the final monetary value is quite low,” he said. “Probably the only people interested in that bug bounty are the same customers of the product.”
Skepticism notwithstanding, SCADA machines, particularly ones with remotely accessible human machine interfaces (HMI), are notoriously vulnerable to attack. That a SCADA vendor would implement a bug bounty at all is a clear step in the direction of fortifying critical infrastructure. The question is whether or not researchers will be at all interested in scouring IntegraXor’s systems for bugs given the unusual payout method.