We
all know what happens when a software vendor downplays the severity of
a security vulnerability. It usually comes back to haunt them, when the
vulnerability is eventually discovered by the bad guys and used to
exploit innocent computer users.
Microsoft, Apple and even Mozilla have all been guilty of this in the past. Lately (and sadly), Adobe has joined this train.
We all have heard about the recent zero-day vulnerabilities in several widely deployed Adobe products. Adobe’s response to some of them has been at times outrageous. As another example, I recommend reading this blog post by Mike Bailey, regarding Adobe’s response to his latest discovery of security problems with Adobe’s Flash Origin-Policy.
Recently, I found a design flaw on Adobe’s website,
which allows the abuse of the Adobe Download Manager to force the
automatic installation of Adobe products, as well as other software
products (e.g. Google Toolbar).
Instead of admitting that this design flaw is indeed a problem which
can be abused by malicious attackers, Adobe decided to downplay this
issue. When ZDNet Zero Day blogger Ryan Naraine reported my discovery
to Adobe, the company sent this response:
A few important points:
- The Adobe Download Manager is intended for one-time use. The
Adobe Download Manager is designed to remove itself from the computer
after use at the next restart. The user can also remove the Adobe
Download Manager prior to this using Add/Remove Programs. - The Adobe Download Manager can only be used to download the latest version of software hosted on Adobe.com.
- The Adobe Download Manager presents a very large user dialog box when downloading software…”
I think they missed the whole point here. While it is true that the
Adobe Download Manager is removed upon computer restart, the user, who
has just updated their Adobe product (usually without the requirement
to restart the computer after the update), is still exposed to forced
automatic installation until they restart their computer.
This specific design flaw does indeed force installation of the
latest version of Adobe products. But, what if there is a zero-day flaw
in an Adobe product, and you have decided to remove it from your system
because of that zero-day? This is not a far-fetched “what if.”
An attacker can force you to automatically download and install the
vulnerable Adobe product, and then exploit the zero-day vulnerability
in that product.
This is the kind of scenario that’s common when skilled, motivated attackers are going after select targets.
And yes, you do get a big dialog box when you are forced to download
the software. Like this will really matter to the attacker, when all he
wants is to get his malicious software on your machine.
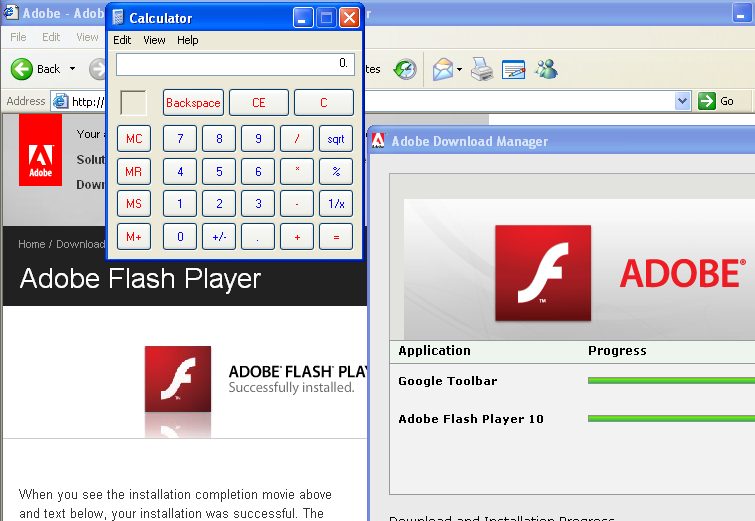
On the same day I published my last blog post, I found yet another
issue — a remote code execution flaw in the Adobe Download Manager.
Basically, what I found is that an attacker can force an automatic
download and installation of ANY executable he desires. So, if you go
to Adobe’s website to install a security update for Flash, you really
expose yourself to a zero-day attack.
Until Adobe decides to fix this vulnerability, I’m going to withhold
the technical details of how to exploit this vulnerability. But, I can
say that Adobe’s claim in regards to Adobe Download Manager use of SSL in downloading the software is simply not true.
I can only hope that Adobe will not downplay this vulnerability as well.
* Aviv Raff manages a security research team for a Fortune 500 company. You can read about his research at his blog or follow his daily activities on Twitter.
UPDATE: Following the publication of this editorial, Adobe issued the following advisory:
Adobe
is aware of the recently posted report of a remote code execution
vulnerability in the Adobe Download Manager. We are working with the
researcher, Aviv Raff, and the third party vendor of this component to
investigate and resolve the issue as quickly as possible. We will
provide updates on this issue via the Adobe PSIRT blog and the Security Advisory section of the Adobe web site.










