Shade, a ransomware known to target Russian victims, has been spotted in several recent campaigns scoping out new locations – including in the U.S. and Japan.
The ransomware, first spotted in late 2014 by Kaspersky Lab researchers, has been known for focusing on Russian victims – but more recent cyberattacks indicate that the majority of Shade ransomware executables are targeting users outside of Russia.
“In fact, our research shows that the top five countries affected by Shade ransomware are not Russia or nations of the former Soviet Union; they are the United States, Japan, India, Thailand, and Canada,” said Brad Duncan, researcher with Palo Alto Networks’ Unit 42 group in a Wednesday analysis.
Meanwhile, “Russia only occurs at number seven, and the only other country we found in the top ten where Russian is an official language is Kazakhstan, at number 10. The top industries attacked in these countries were high-tech, wholesale and education.”
Ransomware Campaigns
The Shade ransomware is spread through malspam emails. In a recent February 2019 campaign for instance, the emails touted a link to an archive, archive attachment or attached PDF with a link to an archive, disguised as an invoice or bill.
These links and attachments lead to a Javascript or other script-based file that is designed to retrieve the Shade executable file.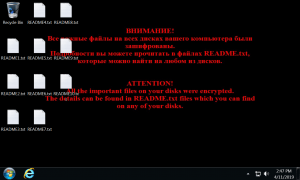
Interestingly, the payload remains “remarkably consistent” since its discovery in 2014, researchers said.
“When a Windows host is infected with Shade ransomware, its desktop background announces the infection, and 10 text files appear on the desktop, named README1.txt through README10.txt,” researchers said.
The desktop background message reads: “Attention! All the important files on your disks were encrypted. The details can be found in README.txt files which you can find on any of your disks.”
All of the README.txt files say the same thing: That is, asking users to send a code to an email address, which would then instruct them on how to make the payments.
New Targets
Recent malicious Shade emails are being sent to various countries other than Russia, indicating that the ransomware developers are looking to expand the breadth of their victim sets.
“We wouldn’t say this represents a switch in focus as much as another piece of the overall campaign over time and geography,” Bradley Duncan, Threat Intelligence Analyst for Unit 42 at Palo Alto Networks, told Threatpost. “Ultimately, attackers go where they think the money is and these attackers would seem to feel these countries may represent lucrative targets in the time we observed these attacks.”
Researchers conducted a deeper analysis between January through March 2019, tracking attempted deliveries of the Shade ransomware executable during an infection chain, focusing on packed executable (PE) files sent through a URL over TCP port 80.
Researchers found that the U.S. saw the most number of attempts to inject systems with Shade (outpacing Japan, India and Thailand).
“The top country with Shade ransomware inf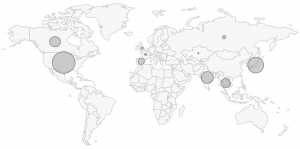 ection attempts among our customer base was the United States,” according to Palo Alto. “The vast majority of these URLs hosting Shade ransomware executables were reported from customer devices outside of Russia and Russian-language countries.”
ection attempts among our customer base was the United States,” according to Palo Alto. “The vast majority of these URLs hosting Shade ransomware executables were reported from customer devices outside of Russia and Russian-language countries.”
Meanwhile, the most common targets for Shade ransomware infection attempts were organizations in the high-tech category. Wholesale and retail, along with education and telecommunications, were also popular targets.
While researchers acknowledged that their results may be skewed towards English due to Palo Alto’s customer base from which it gathers its telemetry, “the analysis still “indicates Shade ransomware is very active outside of Russia and possibly targeting more English-speaking victims than Russian.”
“Attacks can be like sharks: they evolve as much as is needed to be effective,” Duncan told Threatpost. “When they reach a level of effectiveness that doesn’t require further evolution, they can stop evolving. Given that, it is reasonable to conclude that we will see Shade attacks continue.”
Want to know more about Identity Management and navigating the shift beyond passwords? Don’t miss our Threatpost webinar on May 29 at 2 p.m. ET. Join Threatpost editor Tom Spring and a panel of experts as they discuss how cloud, mobility and digital transformation are accelerating the adoption of new Identity Management solutions. Experts discuss the impact of millions of new digital devices (and things) requesting access to managed networks and the challenges that follow.











