A variant of an older piece of adware built for Macs called OperatorMac has been seen in the wild, and while like most adware it tries to turn a profit, it also illustrates some defensive shortcomings native to Apple’s ecosystem and the industry.
Components of the new strain, which is called Mughthesec, are signed with a legitimate Apple developer certificate allowing it to bypass macOS’ native Gatekeeper protection that keeps users from installing unsigned applications. Detection on VirusTotal has also been minimal to date, despite some users reporting infections going back as long as six months.
I can confirm it’s been there for at least 6 months when I found it on my parents MacBook. I just wiped it but thanks for the write up!
— Neal (@iNeal) August 9, 2017
The adware otherwise behaves typically, said researcher Patrick Wardle, chief security researcher at Synack, who along with others analyzed Mughthesec. Wardle said in a report published on the Objective-See blog that the adware is likely spreading through malicious ads or popups. The blog contains removal instructions.
Mughthesec masquerades as an Adobe Flash installer which drops the malware onto the victim’s machine and asks permission to install other programs such as Advanced Mac Cleaner, Safe Finder and Booking[.]com. Advanced Mac Cleaner, Wardle said, triggered a number of alerts as it attempted to install a persistent agent on the computer. The malware also attempts to connect to any of three embedded URLs known for malicious behavior, including banking malware.
“The PUPs are in my opinion, rather shady. I mean they automatically install browser plugins circumventing Apple’s security mechanisms in Safari,” Wardle said. “So sure, they ask for user permission to be installed during install, but then do things that generally the user probably doesn’t want. It’s that gray area between legit code and malware.”
The researcher also said that the malware contains detection capabilities that prevent it from executing if it’s running inside a virtual machine. If it does sense the presence of a VM, it will instead drop a legitimate version of Flash.
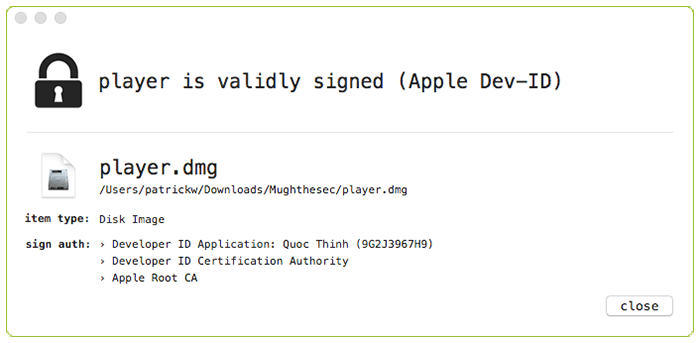
The installer and the application itself were both signed with an Apple developer certificate issued to a Quoc Thinh, below. The installer disk image was uploaded to VirusTotal on Aug. 4 and had zero detection from antimalware engines at the time. The binary also has zero detections on VirusTotal; it also contains logic that helps it evade detection by numerous security products, Wardle said.
“In a nutshell, I think the issue isn’t that anything here is incredible new or exciting; more that existing security/mitigation strategies are rather failing miserably,” Wardle said. “So we’ve got Gatekeeper that’s designed to block unsigned code from the internet to prevent users from getting tricked into installing malware (e.g. fake flash updaters)….which is a great idea. But now most Mac adware/malware is just signed with certs. So gatekeeper is basically a moot point. Normal-everyday users are still going to go around infecting themselves…and things designed to protect them; Gatekeeper/AV etc, really don’t offer any help.”
Using a homegrown process monitor called ProcInfo, Wardle was able to watch execute a particular process called “i” which persists and launches an agent. Wardle said the agent has three jobs: execute the Mughthesec binary, pass in a parameter “r,” and automatically start when the user logs in. The Mughthesec binary, Wardle said, is unsigned and has zero VirusTotal detections.
Once installed, the malware’s goal is profit.
“A common tactic of adware is to hijack the victim’s browser (homepage, inject ads, etc) for financial gain,” Wardle said. “Mughthesec (which is installed when the user ‘agrees’ to install ‘Safe Finder’) appears to conform to goal.”
First, the malware changes the victim’s browser homepage to an attacker-controlled domain.
“If we open Safari; indeed the home page has been hijacked–though in a seemingly innocuous way,” Wardle said, adding that he did not test the sample on Google’s Chrome browser. “It simply displays a rather ‘clean’ search page—though looking at the source, we can see the inclusion of several scripts ‘Safe Finder’ scripts.”
Wardle said that an AnySearch browser extension has also been added that funnels a user’s search queries through a number of affiliates, generating revenue along the way, before eventually rendering search results from Yahoo. The Safe Finder scripts, meanwhile, have injected SafeFinder logos and more into search results, Wardle said.
Thomas Reed of Malwarebytes said it’s likely that Mughthesec is an OperatorMac variant.
Thanks, Patrick sent me the hash too. Looks like a new variant of something we call OperatorMac (though that may be a bad name).
— Thomas Reed (@thomasareed) August 8, 2017
“Yes it’s rather unsophisticated macOS malware, but it’s installer is signed (to ‘bypass’ Gatekeeper) and at the time of this analysis no anti-virus engines were detected it….and mac users are being infected,” Wardle said. “Speaking of infection, due to the fact that the installer is masquerading as Flash Player installer, it’s likely that this adware is relying on common infection techniques to gain new victims. Either way, user interaction is likely required.”