Six hackers in total have each now pocketed more than $1 million from finding vulnerabilities in bug-bounty programs – including one from the U.S. That figure comes as more bug-bounty programs bump up their rewards due to participants finding more high-severity vulnerabilities in their platforms, according to a new HackerOne report.
In March 2019, HackerOne announced that 19-year-old Argentinian hacker Santiago Lopez (also known as @try_to_hack) was the world’s first hacker to earn $1 million with bug-bounty programs. Now, five more have joined the high-standing $1 million hacker ranks, including: Tommy DeVoss from the U.S., Mark Litchfield from the U.K., Nathaniel Wakelam from Australia, Frans Rosen from Sweden, and Ron Chan from Hong Kong.
DeVoss, whose bug-bounty contributions have included Verizon Media, the U.S. Department of Defense and a critical PayPal vulnerability that earned him $10,000 last year, is the first U.S.-based hacker to reach $1 million thus far in bounties: “Hitting that $1 million dollar milestone is a huge accomplishment and it feels amazing to know that the other five hackers and I have had such a huge impact. I hope our achievements will encourage other hackers to test their skills, become part of our supportive community and make the internet a much safer place,” he said in a media statement.
“I joined the wrong chat room when I was around 10 years old,” said DeVoss (also known as @dawgyg). “When I discovered bug-bounty programs about 20 years later, I was finally able to use my curiosity for breaking things and standing up for what I believe in the name of defending organizations I believe in.”
On top of the six who have each surpassed $1 million in lifetime earnings, seven other bounty hunters hit $500,000 in lifetime earnings, and more than 50 have earned $100,000 or more in the past year. That’s according to HackerOne in its 2019 Hacker-Powered Security Report, which examined the more than 120,000 vulnerabilities spotted for 1,400 bug bounty programs.
Overall, the report said, bounty hunters have earned $12 million over the past 12 months (and over $62 million in rewards overall) for finding vulnerabilities in platforms.
The average bounty paid for critical vulnerabilities increased 48 percent over last year’s average across all industries, from from $2,281 to $3,384, with the most competitive programs today like Google, Microsoft, Apple and Intel offering individual bounty awards as high as $1,500,000 for critical issues.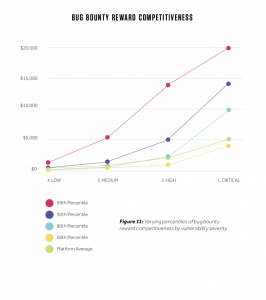
In fact, recently big companies like Apple and Google have sought to improve their programs, with Apple at Black Hat announcing more in-scope products (like MacOS) and higher rewards; and Google announcing a new bug-bounty program aimed at squashing data abuse on Google Play Android apps.
The higher rewards are due to more severe vulnerabilities being found, HackerOne says in its report. The report found that 25 percent of valid vulnerabilities found are classified as being of high or critical severity.
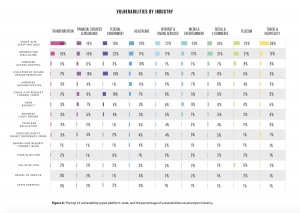
Bug-bounty programs are also extending to various new sectors: Government and Federal for instance had the strongest year over year industry growth at 214 percent, with the first launch of programs at the municipal level.
Also seeing growth were the automotive, telecommunications, consumer goods and cryptocurrency/blockchain industries. And, financial services organizations grew 41 percent this year, tapping into hackers to identify unknown security vulnerabilities; in fact, today, six out of 10 of the top banks in North America are running hacker-powered security programs.
Interested in more on the internet of things (IoT)? Don’t miss our free Threatpost webinar, IoT: Implementing Security in a 5G World, available on-demand. Please join Threatpost senior editor Tara Seals and a panel of experts as they offer enterprises and other organizations insight about how to approach security for the next wave of IoT deployments, which will be enabled by the rollout of 5G networks worldwide. Click here to listen to the recorded webinar.