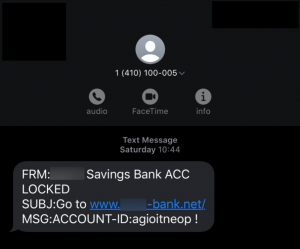
Attackers are sending SMS messages purporting to be from victims’ banks – but once they click on the links in the text messages, they are asked to hand over their banking credentials and download a file that infects their systems with the Emotet malware.
Emotet has continued to evolve since its return in September, including a new, dangerous Wi-Fi hack feature disclosed last week that can let the malware spread like a worm. Now, this most recent campaign delivers the malware via “smishing,” a form of phishing that relies on text messages instead of email. While smishing is certainly nothing new, researchers say that the delivery tactic exemplifies Emotet’s operators constantly swapping up their approaches to go beyond mere malspam emails – making it hard for defense teams to keep up.
“Emotet’s operator, the Mealybug gang, has varied its activity levels over time, sometimes going into lengthy lulls and periods of low-volume activity,” said researchers with IBM X-Force in a Wednesday analysis. “Since late 2019, Mealybug has been pushing its activity through various channels, including spam, sextortion emails, SMiShing and ploys like fake Coronavirus warnings that were spread in Japan.”
The SMS messages purport to be from local U.S. numbers and impersonate banks, warning users of locked bank accounts. The messages urge victims to click on a link, which redirects them to a domain that’s known to distribute Emotet (shabon[.]co). Visually, when victims click on the link they see a customized phishing page that mimics the bank’s mobile banking page.
Threatpost has reached out to X-Force researchers regarding how many victims have received the SMS messages, and which banks the messages purport to be associated with.
The smishing landing page domain was registered on the same day that the text messages were sent, said researchers. The domain features the bank’s name (with a different top-level domain) and is designed to persuade victims into entering their credentials as a first step, and then have them download a document file loaded with the malicious macros as a second step.
After examining two binary files that are served to victims from this file, researchers found some junk content in the file, containing “news” excerpts regarding President Donald Trump and presidential candidate Michael Bloomberg. Researchers believe that this tactic is a way to evade detection.
Interestingly, the TrickBot trojan frequently uses a similar type of anti-detection method relating to junk content – leading to a potential link to the malware as part of the campaign, researchers said. While Emotet started life as a banking trojan in 2014, it has continually evolved to become a full-service threat-delivery mechanism, including as one for TrickBot in previous attacks like a recent one targeting the United Nations.
“Knowing that Emotet is one of the ways TrickBot payloads are dropped to infected systems, there is a possibility that this attack is a targeted campaign designed to enable the spread of the TrickBot trojan,” researchers said.
Looking forward, researchers believe that this recent smishing campaign, coupled with other recent Emotet appearances, shows that its operators may be looking to launch future cyberattacks, potentially around the upcoming 2020 Olympics, which kick off July 2020.
“Mealybug is gearing up to expand its botnet, diversify its illicit income sources and prepare for a wider attack surface in Japan, possibly ahead of the 2020 international sporting event coming to Tokyo in the summer,” they said.
Learn how Operational Technology and Information Technology systems are merging and changing security playbooks in this free Threatpost Webinar. Join us Wednesday, Feb. 19 at 2 p.m. ET when a panel of OT and IT security experts will discuss how this growing trend is shaping security approaches for IoT and 5G rollouts. This webinar is for security and DevOps engineers, IoT edge developers and security executives.