Recently discovered spear-phishing emails are using a unique “scare-factor” lure to convince victims to open attached malicious Microsoft Excel documents: Their HIV test results.
Researchers are warning of a recent campaign involving emails claiming to come from Vanderbilt University Medical Center, a legitimate medical complex in Nashville, Tenn. The emails were sent to a slew of unnamed companies in various industries, including global insurance, healthcare, and pharmaceutical firms. If victims clicked on the embedded attachment in the emails, they were infected with the Koadic RAT, which allows attackers to run programs and access victims’ data, including sensitive personal and financial information.
“Healthcare concerns drive us to do a lot of things like change our diet, work out more, and take medication,” said researchers with Proofpoint on Tuesday. “But they should never lead us to fall victim to phishing campaign. Threat actors regularly use purported health information in their phishing lures because it evokes an emotional response that is particularly effective in tricking potential victims to open malicious attachments or click malicious links.”
Victims received an email purporting to come from “Vanderbit [SIC] Medical,” with the subject line “Test result of medical analysis.” The body of the email encourages victims to open a malicious Microsoft Excel attachment titled “TestResults.xlsb,” claiming that the recipient’s HIV results are contained within it.
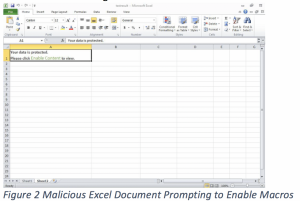
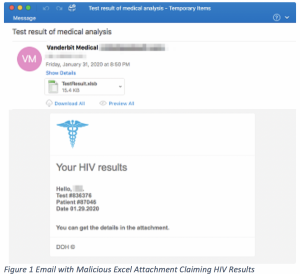 Once the victim opens the attachment, the Excel document opens and prompts the user to enable macros – and once they do that, the document then downloads the Koadic RAT.
Once the victim opens the attachment, the Excel document opens and prompts the user to enable macros – and once they do that, the document then downloads the Koadic RAT.
Koadic is an open source, post-exploitation remote access trojan that uses the Windows Script Host. Originally, Koadic was intended as a tool for network defenders and allows the actor to take complete control over a user’s system.
However, researchers said in recent years it has been used by a variety of nation state actors, including both Chinese and Russian state-sponsored groups, as well as attackers associated with Iran. In 2017, researchers said that the China-linked Stone Panda APT was using Koadic in its “Chessmaster” campaign against Japan. And in 2018, the Fancy Bear APT was seen leveraging Koadic with its custom Zebrocy malware.
Sherrod DeGrippo with Proofpoint told Threatpost that the emails don’t appear to have been targeted in terms of individual recipients. However, they do appear to have been very focused in terms of their targeting of industries, she said.
“While we do not have insight into the medical history of targeted individuals, we have no reason to believe that the attackers had specific awareness of the recipient’s HIV status or whether they were patients of Vanderbilt (which was misspelled as “Vanderbit” within the campaign),” she told Threatpost. “We do regularly observe threat actors taking advantage of medical scenarios that can create a sense of urgency. This campaign is social engineering based on fear. They know that the individuals targeted will be more likely to click on a potentially malicious message or download an attachment due to either concern for their own safety if they have recently been tested or out of curiosity if they haven’t been tested.”
This most recent spear-phishing attack is a reflection of attackers continuing to use innovative lures to convince victims to click on malicious links or attachments. More recently they have been spotted tapping into the panic around the Coronavirus with spear-phishing emails that mention the virus. Beyond that, attackers are also using anything from taxes to real estate decoys.
 Researchers said that sensitive health-related information is typically safely transmitted using secured messaging portals, over the phone, or in-person. If potential victims receive emails claiming to have sensitive health-related information, researchers said they should their medical provider’s patient portal directly or call their doctor rather than open the email.
Researchers said that sensitive health-related information is typically safely transmitted using secured messaging portals, over the phone, or in-person. If potential victims receive emails claiming to have sensitive health-related information, researchers said they should their medical provider’s patient portal directly or call their doctor rather than open the email.
“This latest campaign serves as a reminder that health-related lures didn’t start and won’t stop with the recent Coronavirus-themed lures we observed,” researchers said. “They are a constant tactic as attackers recognize the utility of the health-related ‘scare factor.'” We encourage users to treat health-related emails with caution, especially those that claim to have sensitive health-related information.”
Interested in security for the Internet of Things and how 5G will change the threat landscape? Join our free Threatpost webinar, “5G, the Olympics and Next-Gen Security Challenges,” as our panel discusses what use cases to expect in 2020 (the Olympics will be a first test), why 5G security risks are different, the role of AI in defense and how enterprises can manage their risk. Register here.











