Researchers warn of an ongoing spear-phishing attack mimicking a well-known telecommunications company, EE, to snatch up corporate executives’ credentials and payment details.
Highly targeted emails have been sent to a few executives – including one at a leading financial firm – purporting to be from British internet service provider EE, which as of 2019 is one the largest mobile network operators in the UK, with around 32 million customers.
The phishing campaign comes with a few sloppy red flags that eagle-eyed recipients might pick up on – but researchers say its use of HTTPS and SSL certificates for its landing page help it evade detection.
“This new, targeted campaign shows that while exploiting well-known telecommunications brands is nothing new, such phishing emails continue to go undetected by popular email gateways designed to protect end users, leading to possible theft of prized corporate credentials,” said researchers with Cofense in a Monday analysis.
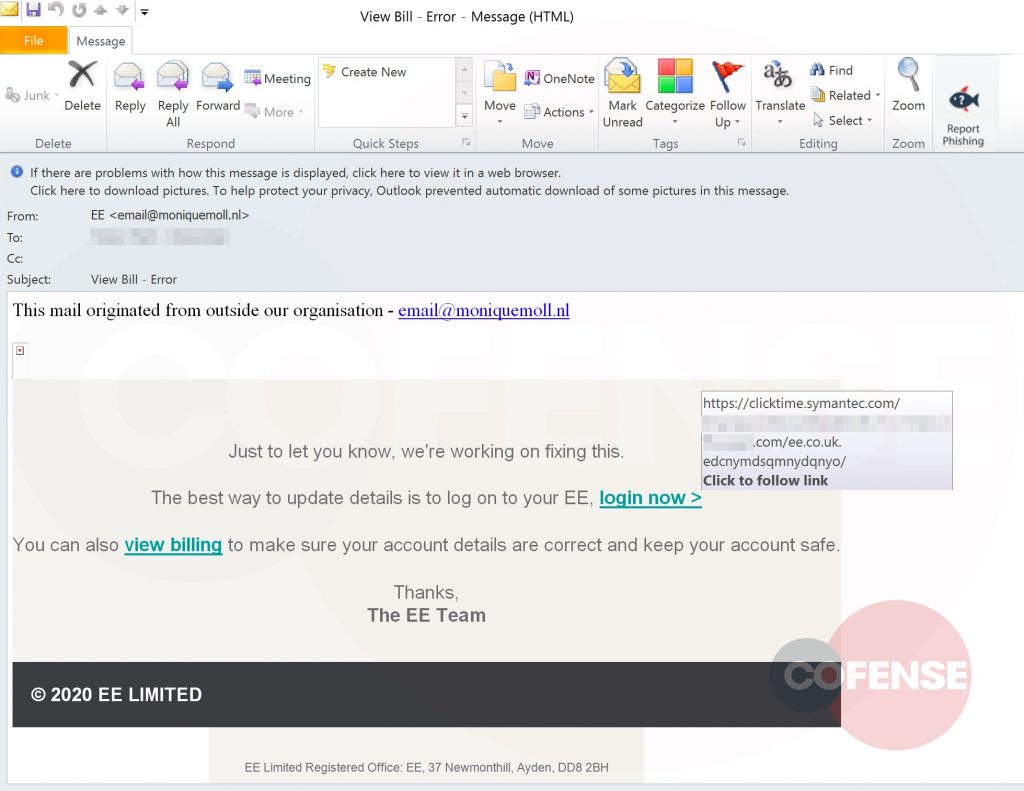
The emails bear a subject line reading “View Bill – Error” that comes from a purchased, top-level domain (moniquemoll[.]nl). Therein lies the first red flag: EE’s trademarked name isn’t included in any part of the full email address.
Another red flag is the content of the email, which remains strangely vague, only saying “we’re working to get this fixed,” without going the step further to indicate what the actual error is. Also, the threat actor includes an incorrect registered office address (at the bottom of the email).
The email tells recipients that “the best way to update details is to log on to your EE” and offers a hyperlink that states ‘view billing to make sure your account details are correct’ to entice the recipient to click the phishing link.
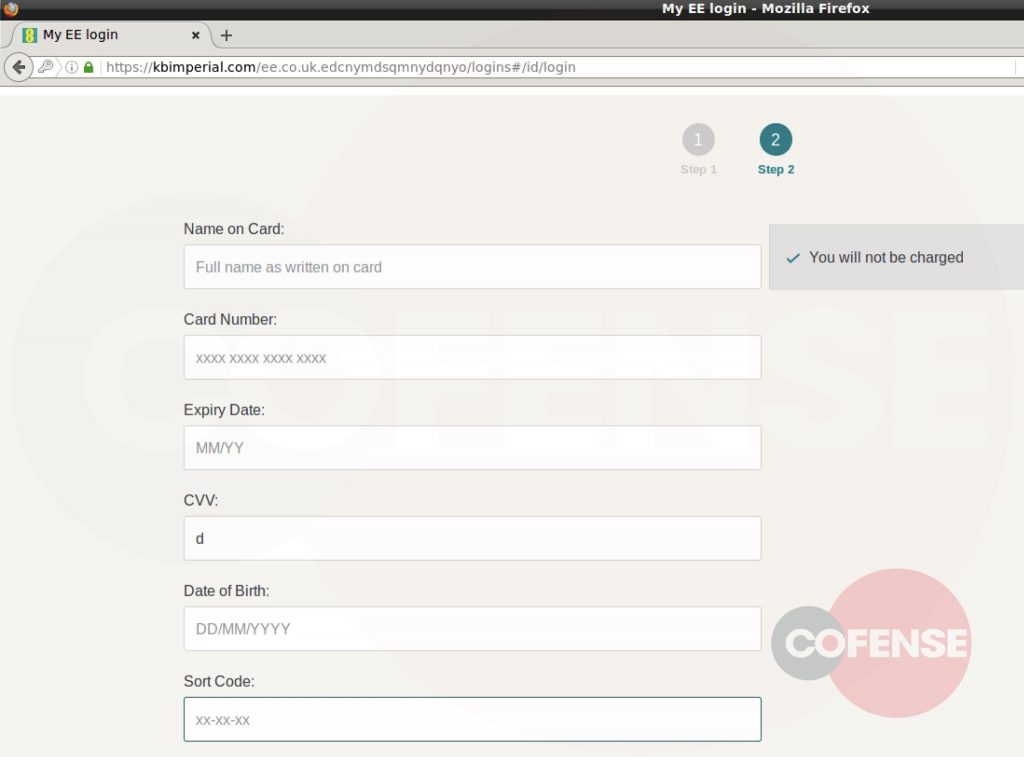
If a user clicks one of the links, they are redirected to a phishing page. The phishing landing page uses the trusted HTTPS protocol (also displayed as the green padlock) within the URL. The use of HTTPS, which other phishing campaigns have utilized, gives false hope to the user that network traffic is being encrypted and that it’s therefore safe. However, just because the traffic is encrypted, does not mean that a website isn’t malicious.
The attackers went a step further by obtaining SSL certificates for the phishing landing page’s domain to further add an air of legitimacy. Researchers said, it has become much easier for site owners, including fraudsters, to obtain these certificates. The initial phishing landing page then asks for victims to log in to their EE (formerly Everything Everywhere) accounts. They are then taken to a page requesting their payment information.
“The peculiar aspect is the message in which the threat actor included: ‘You will not be charged’ to reassure recipients and trick them into providing their payment information,” said researchers.
The user is then automatically redirected to the legitimate EE website to avoid suspicion. This is a common tactic to make the user believe the session timed out or their password was mistyped, researchers said. Researchers said the phishing pages are still live and active as of Monday.
Phishing campaigns continue to target online users over the past month, particularly with the new troves of remote workers. Earlier in April, several U.S. universities were targeted in a widespread spear-phishing attack that uses adult dating as a lure. Also in April, threat actors continued to capitalize on fears surrounding the spread of the COVID-19 virus through a surge in new phishing campaigns that use spoofing tactics to effectively evade Proofpoint and Microsoft Office 365 advanced threat protections (ATPs), researchers have found.
Inbox security is your best defense against today’s fastest growing security threat – phishing and Business Email Compromise attacks. On May 13 at 2 p.m. ET, join Valimail security experts and Threatpost for a FREE webinar, 5 Proven Strategies to Prevent Email Compromise. Get exclusive insights and advanced takeaways on how to lockdown your inbox to fend off the latest phishing and BEC assaults. Please register here for this sponsored webinar.
Also, don’t miss our latest on-demand webinar from DivvyCloud and Threatpost, A Practical Guide to Securing the Cloud in the Face of Crisis, with critical, advanced takeaways on how to avoid cloud disruption and chaos.