Researchers are keeping close tabs on a new ransomware strain called Spora that offers victims unique payment options and comes with top-notch encryption.
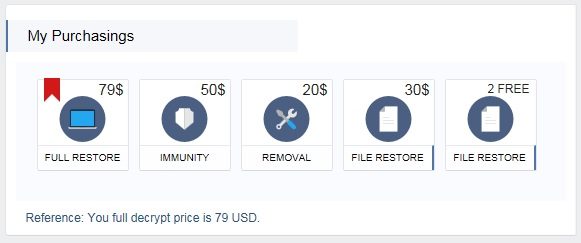
Spora was spotted last week by ransomware experts at BleepingComputer, who said after Spora encrypts files on your computer, it offers four tiered payment options: Full Restore ($79); Immunity ($50); Removal ($20); and File Restore ($30). Spora also offers a Free option that allows you to decrypt two random files in order to win confidence that encrypted files can be restored. Pricing varies based on the system infected.
“Spora’s decryption service is something that we haven’t seen in any other ransomware decryption site,” wrote BleepingComputer in a technical breakdown of the ransomware. It said Spora had “the most sophisticated (payment site) it has seen from ransomware authors as of yet.”
Payment options are straightforward with Immunity meaning immunity from future attacks. The Select File option allows victims to choose a limited group of files to restore, but not a full system decryption.
The unique payment options, researchers believe are inspired by cybercriminals seeking more options to provide victims who may be less inclined to pay a full ransom. For example, a victim might be less inclined to pay $79 to recover files they had safely backed up. But they might pay $20 to have the ransomware removed from their system.
Another distinguishing feature of Spora is the implementation of the encryption which researchers say is well thought through. The ransomware works offline, staying low profile and generating no network traffic to outside C2 servers.
“Spora has top notch encryption,” noted BleepingComputer. “Spora does not appear to contain any weaknesses in its encryption routine. The entire encryption operation appears to be very complicated,” according to its analysis.
Currently, the ransomware is targeting Russian-language users and is being delivered via a spam message. Emails contain what is meant to look like a PDF invoice, but it is actually a HTA file that contains a VBScript program or dropper. Launching the HTA files sets off a chain reaction, ultimately leading to the encryption of the computer.
The VBScript program creates and runs an embedded JavaScript file in the system’s %TEMP% directory called Close.js. That Close.js file extracts yet another executable (with a randomly generated name) within the same folder. And it’s that file that encrypts data, according to the BleepingComputer’s analysis.
Because Spora works entirely offline, the encryption process requires a number of different longwinded steps. In a nutshell, Spora uses a combination of RSA and AES to encrypt data and takes advantage of the Windows CryptoAPI to do it. The process leverages a public-private 1024 bit RSA key pair that is unique to the victim’s computer along with a random 256 bit AES key for each file encrypted.
“Unlike most of today’s ransomware families, Spora works offline and does not generate any network traffic to online servers,” BleepingComputer wrote. According to BleepingComputer, the encryption process targets local files and network shares, but does not append any extra file extension at the end of files, leaving file names intact.
Another interesting aspect of Spora is the .KEY file created by the ransomware which contains the victim’s RSA private key, and also statistical data such as infection date, the victim’s username and a hard-coded identifier of the Spora sample used in the campaign.
The way the decryption process works is it requires the infected machine to visit the Spora decryption portal via a Tor gateway on the domain Spora[.]bz. Users are then required to “synchronize” their computer with the decryption portal by uploading the .KEY file, according to BleepingComputer.
“By synchronizing the key file, unique information about the encryption of your computer is then uploaded to the payment site and associated with your unique id… Everything on this portal is neatly arranged as a website dashboard, complete with helpful tooltips that appear when hovering over certain options,” wrote BleepingComputer.
After the victim synchronizes it to the decryption portal, Spora determines how much the ransom should be, based on the amount and type of data encrypted. Ransom demands have ranged from $79 to $280 for the Full Restore option.
“Spora seems to be a ransomware family as advanced and well-run as Cerber and Locky, and we may soon see its operators expand from Russia to other countries across the world,” researchers note in the report.