An out-of-bounds read vulnerability in the Squirrel programming language lets attackers break out of sandbox restrictions and execute arbitrary code within a Squirrel virtual machine (VM), thus giving a malicious actor complete access to the underlying machine.
Given where Squirrel lives – in games and embedded in the internet of things (IoT) – the bug potentially endangers the millions of monthly gamers who play video games such as Counter-Strike: Global Offensive and Portal 2, as well as cloud services IoT platforms with ready-to-use open-source code library.
Squirrel is an open-source, object-oriented programming language used by video games and cloud services for customization and plugin development. It’s a lightweight scripting language that suits the size, memory bandwidth and real-time requirements of applications like video games and embedded systems.
Both of the games mentioned above use the Squirrel Engine game library to enable anyone to create custom game modes and maps.
Tracked as CVE-2021-41556, the Squirrel out-of-bounds read vulnerability can be exploited when a Squirrel Engine is used to execute untrusted code, as it is with certain video games.
The vulnerability was discovered by SonarSource and detailed in a post published on Tuesday. In that writeup, vulnerability researchers Simon Scannell and Niklas Breitfeld suggested a real-world scenario in which an attacker could embed a malicious Squirrel script into a community map and distribute it via the trusted Steam Workshop: a mod repository for Steam Games that lets creators upload their mods for a massive built-in audience while providing regular players with an easy way to obtain mods.
“When a server owner downloads and installs this malicious map onto his server, the Squirrel script is executed, escapes its VM, and takes control of the server machine,” the researchers explained.
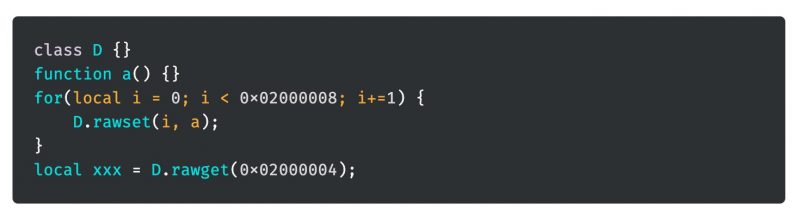
The security flaw concerns an “out-of-bounds access via index confusion” when defining Squirrel classes. “The fact that bitflags are set within indexes is problematic as it is entirely possible for an attacker to create a class definition with 0x02000000 methods,” the researchers explained. They created the following, “very simple” proof of concept (PoC): just a nibble’s worth of code that could be exploited to hijack a program and grant an attacker full control of the Squirrel VM.
“The rawset and rawget functions allow us to handily access members of a given class,” according to the analysis. “In this PoC, the squirrel interpreter will dereference a null pointer and segfault because the _defaultvalues array has not been allocated yet.”
An attacker could trigger the vulnerability by:
- Creating a class definition with 0x02000005 methods and 0x1 fields
- Accessing the method with the corresponding index 0x02000005
- The _isfield() macro returns true for this index as the bitflag 0x02000000 is set
- The _defaultvalues array is accessed with index 0x5. However, it only contains 0x1 entries and thus the attacker has accessed out of bounds.
The vulnerability is dangerous because a malicious actor could set up a fake array that could read and write values. By doing so themselves, the researchers found they could “hijack the control flow of the program and gain full control of the Squirrel VM,” which they did by overwriting function pointers.
SonarSource provided the following chart, which shows the chain of attacker-controlled pointer that enabled reading and writing to the entire address space:

Chain of attacker-controlled pointer that enabled reading and writing to the entire address space. Source: SonarSource.
Squirrel GitHub Repository Patched
The maintainer of the Squirrel GitHub repository acknowledged the vulnerability in August. A patch was pushed out as part of a code commit on Sept. 16.
But as noted by The Hacker News, the changes haven’t been included in a new stable release, with the last official version (v3.1) released on March 27, 2016.
Thus, the researchers who discovered the vulnerability are “highly” recommending that maintainers who use Squirrel in their projects apply the available fix commit in order to protect against attacks.
UPDATE 1: 102121 08:44 Removed references to vulnerability affecting a cloud services platform pending answers from SonarSource regarding whether researchers verified that the platform was actually affected.
UPDATE 2: 102121 13:27 Johannes Dahse, Head of R&D at SonarSource, confirmed that the company hadn’t reached out to Twilio Electric Imp before including it in a list of cloud services and games that are vulnerable to the issue. Dahse’s statement:
“Our research team regularly finds critical vulnerabilities in software that is incorporated into many other vendors’ software. When publishing our findings we are often asked about the impact and severity. For this reason, we named a few examples of who uses Squirrel to illustrate the problem. We do not test all other vendors’ exact implementation for resource purposes. Therefore, as stated in our post, we did not test concrete exploits against a specific third-party implementation and we did not actively reach out to Twilio ourselves. However, we’ve seen the Electric Imp team contact the Squirrel maintainer for details two months ago as part of our GitHub issue. With our blog post we hope to raise awareness of this vulnerability with more Squirrel users so they can test or harden their software. We are impressed to see how quickly this was done by Twilio and that security is taken very seriously. We are happy to add an update about this example to our blog post or to remove the mention of Twilio if this causes any confusion.”
Check out our free upcoming live and on-demand online town halls – unique, dynamic discussions with cybersecurity experts and the Threatpost community.